Crypto Academy / Season 3 / Week 2 - Homework Post for @pelon53
COLLISION RESISTANCE
The collision resistance is supposed to be a property of the hash function in cryptography, you can't discuss the collision resistance without going on about the cryptographic hash function. A hash function is supposed to be collision resistant when it gets hard to get 2 information sources hashing to a similar yield.
This is to say for example having two data sources say x and y in that H(x) will be equivalent to H(y). At whatever point hash functions have a larger number of contributions than it has yields, they will encounter collisions.
At the point when we talk about hashing, we are discussing the way toward making a yield that has a fixed size from an info that an alternate sizes. This must be accomplished by utilizing the utilization of numerical recipes that are alluded to as hash functions.
Despite the fact that it's anything but all hash functions that includes utilizing cryptography, the hash functions are the fundamentals of the digital currency. This has made square chains and other conveyed frameworks to accomplish a huge degree of safety and information respectability.
As referenced, a collision results when unique sources of info produce precisely the same hash. This implies that the hash function is supposed to be resistant to collision till the second when somebody can discover its collision.
Collisions will consistently be accessible for hash functions in light of the fact that the potential information sources are boundless, while the potential yields are restricted. In other words, a hash function is resistant to collision when the probability of finding a collision is little to such an extent that it needs such countless long stretches of number juggling.
Along these lines, in spite of the fact that there are no hash functions that are liberated from collision, there are some hash functions that are sufficiently able to be alluded to as resistant. This could be said on account of SHA-256.
Discussing the SHA calculations, the blends of SHA-0 and SHA-1 are lacking as far as security in light of collisions yet we can say that when we consolidate SHA-2 and SHA-3 they are supposed to be resistant to collision. A collision happens when an assailant can lay hands on 2 sources of info say a1 and a2 that will both outcome in a similar yield.
Search for any two sources of info a1 and a2 with the goal that H(a1) will be equivalent to H(a2) also, will all be equivalent to Y(and a1 won't be equivalent to a2)
This is very unique in relation to the second preimage assault (which later be talked about as we gain ground) in light of the fact that the assailant can choose both the data sources, this makes it a lot simpler to achieve.
The collision resistance turns into a need when you rely upon the hash functions to have the option to produce 2 contributions to 2 shifting yields. at the point when the yield space is little contrasted with the information space, then, at that point numerous data sources will produce similar yields. despite the fact that we are sure of the presence of collisions, we can in any case utilize certain subset hash functions for cryptography. This is the thing that we allude to as collision resistant hash function.
THE RESISTANCE TO PRE IMAGE
This is a flat out need for hash functions since it implies that the function is one way, The idea of preimage is identified with one way functions. At the point when we talk about preimage resistance in hash function, we are alluding to whenever there is little possibility of an individual discovering the input that will give an output.
This security property is not quite the same as the past one on the grounds that the individual attempting to attack should think about what the input is by taking a gander at an output. This isn't so for a crash as an impact happens when somebody discovers various inputs that create a similar output, yet the input utilized is essentially not a thought about factor.
In the preimage attack we are given the output to discover the input that created it. That is we are given say x = H(a) to discover a.
The preimage resistance is vital in hash functions in the assurance of information since simply a hash of the message can affirm if it is legitimate even without uncovering significant data.
USING ETHERSCAN TO VERIFY HASH
To be able to verify hash address using etherscan, below were the following procedures I followed to get both the hash address and the number of transactions carried out on the last block.
first of all, I opened the etherscan website which is https://etherscan.io
Once the website is opened you will see the latest blocks and latest transactions section, for this demo, I will use the last block which is 12793105
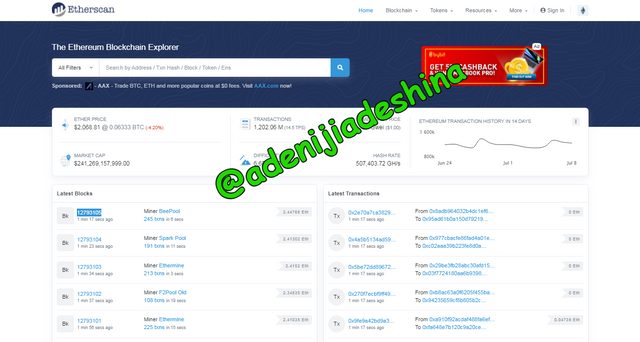
To get the hash for the block, I tapped the said block above thereby opening every one of the informations about the block.
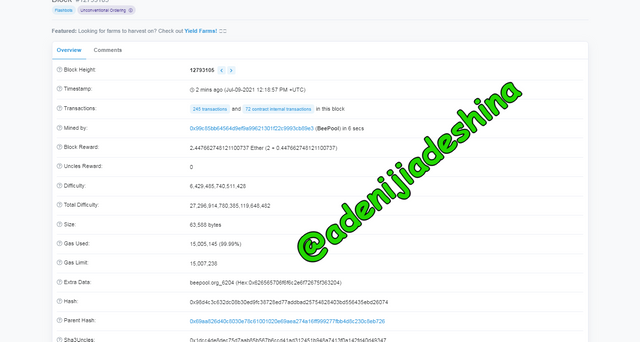
From the showed data, the hash to the block is 0x98d4c3c632dc08b30ed9fc38728ed77addbad25754828403bd556435ebd26074
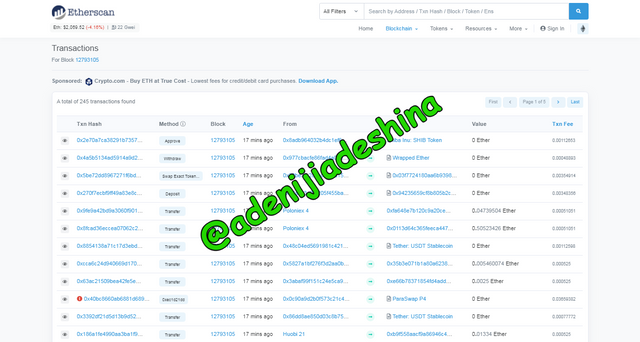
Copy the hash address or the block from the table shown above and paste it in the search space provided at the top, this will be used to get the number of transactions carried out on the block.
From the below image the total number of transactions that was carried out on this block is 245.
USING TRONSCAN TO VERIFY HASH AND TO CHECK TRANSACTION CARRIED OUT ON ITS BLOCK
Just like I did with the etherscan, I will also be using the tronscan for the verification of hash and also be using it to check the total number of transactions that were carried out on the block that I will be choosing.
To use tronscan you may want to use the app on your mobile device, if that is the case then you can download the tronscan app from your phone’s app store but for the sake of this article, I will be login in through the tronscan website which is www.tronscan.org.
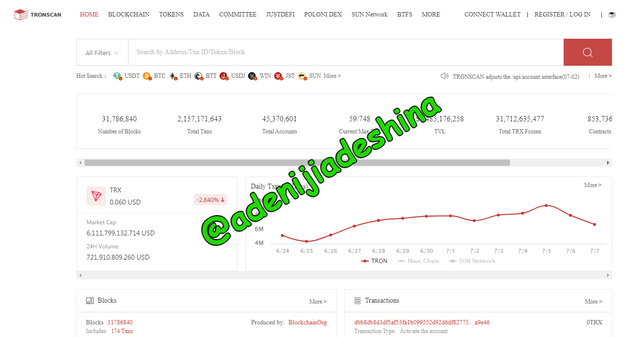
After you open the website, go down and you will see the blocks section and the transactions section.
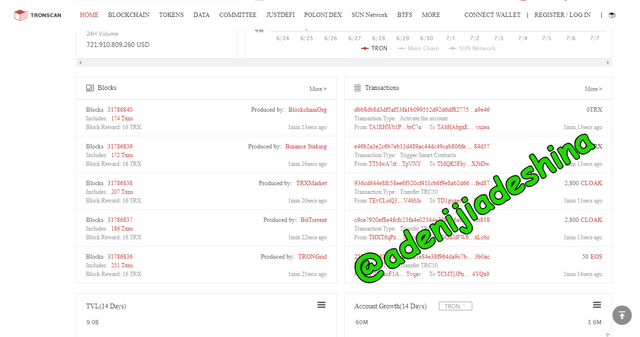
Click on the block of your choice, but I wil be making use of the last block which is block 31786840
To get the hash for this block, click on the block and all informations about the block will be displayed as in the image below.
The block hash for block 31786840 above is 0000000001e507589b3095bd59541de2414784d0d13c27d875088379db8306f3
Unlike like in the case of etherscan where you need to search the transactions separately, in tronscan the transaction is just below the blocks information, all you have to do is to just scroll down.
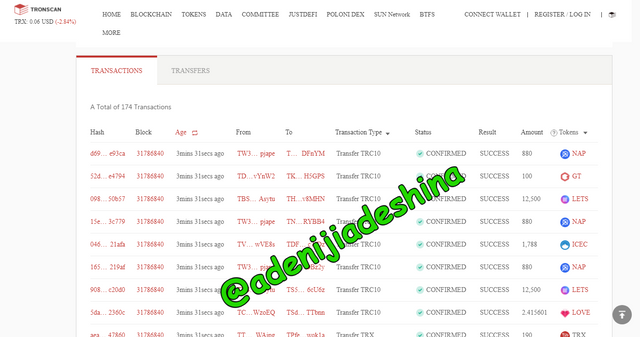
As could be seen from the image above the total number of transactions made on this block is 174 transactions.
HOW TO GENERATE HASH USING SHA-256, FROM THE WORD CryptoAcademy and cryptoacademy
I will be generating hash with the use of SHA-256 from the word CryptoAcademy and cryptoacademy.
To achieve this I used the password generator for SHA-256 website which is https://passwordsgenerator.net/sha256-hash-generator/
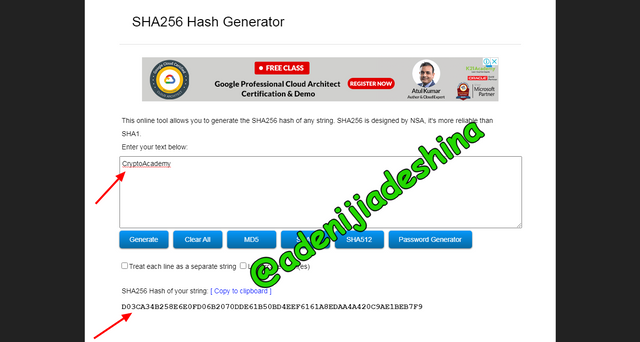
Using the provided search bar I wrote the word I wanted to generate hash for, that is CryptoAcademy.
from the below image, this was the result I got D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
Using the provided search bar I wrote the word I wanted to generate hash for, that is cryptoacademy.
from the below image, this was the result I got 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
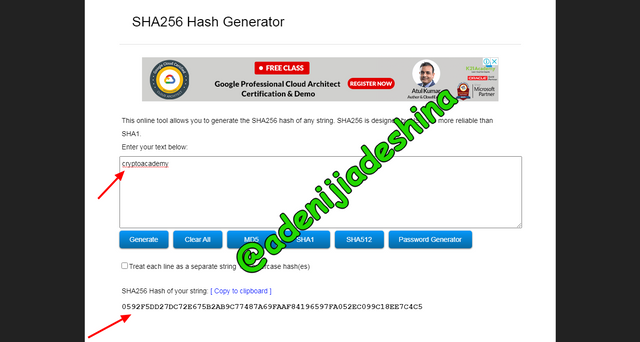
This is a proof that no two different inputs can give us the same output, The motivation behind why the hashes for the two words are diverse is on the grounds that it has distinctive casing, the primary word we looked for had Upper cases in them while the subsequent word just had lower cases. From these outcomes we can say that hash is collision resistant since 2 same words created various outcomes.
WHAT IS DIFFERENCE BETWEEN HASH AND CRYPTOGRAPHY
HASH:
At the point when we talk of hashing, we are alluding to a technique for cryptography that is utilized to change over information into an uncommon line of text. They are utilized for encoding information into extraordinary alphanumeric string, this is to guarantee security and protection.
Note that a wide range of information can be hashed as there is no sort, length nor size requirement. The consequence of any produced hash consistently has a fixed length.
Like we said toward the start, the hash goes about as a single direction work. Each hash has an alternate yield, actually like in the exhibit we completed previously. A similar information will consistently produce a similar yield.
CRYPTOGRAPHY:
Cryptography guarantees the security of the two exchanges and the clients. Cryptography completes encoding and translating undertakings of different information by utilizing numerical techniques. It is the technique for sending secure messages between numerous clients, how it is done is that the sender of the message will scramble the message utilizing a particular key and calculation, and afterward when the recipient at the opposite end gets this message, he should decode the message to have the option to get the first message sent.
Below are few observable differences between the hash and the cryptography.
Hash doesn't utilize keys while cryptography utilizes keys to have the option to recuperate its informations.
The length of yield in hash is consistently a similar regardless of the kind of information while in cryptography as data builds, the length likewise increments.
Data in hash can't be recuperated while on account of cryptography it tends to be recuperated by the utilization of keys.
Gracias por participar en Steemit Crypto Academy Season 3:
No cumples con las reglas para participar en esta tarea.
Recomendaciones:
Calificación: No cumple con las reglas
Hello professor. I have a minimum of 250 steem power. I qualify for the intermediate and to be Verifed.
This is the screenshot below
@pelon53 @pelon53
I guess there was a mix up somewhere. I have even been Verifed before last week and even voted by steemcurator last week so I am still surprise how I didn't meet the minimum requirements.
Check this screenshot again to reconfirm please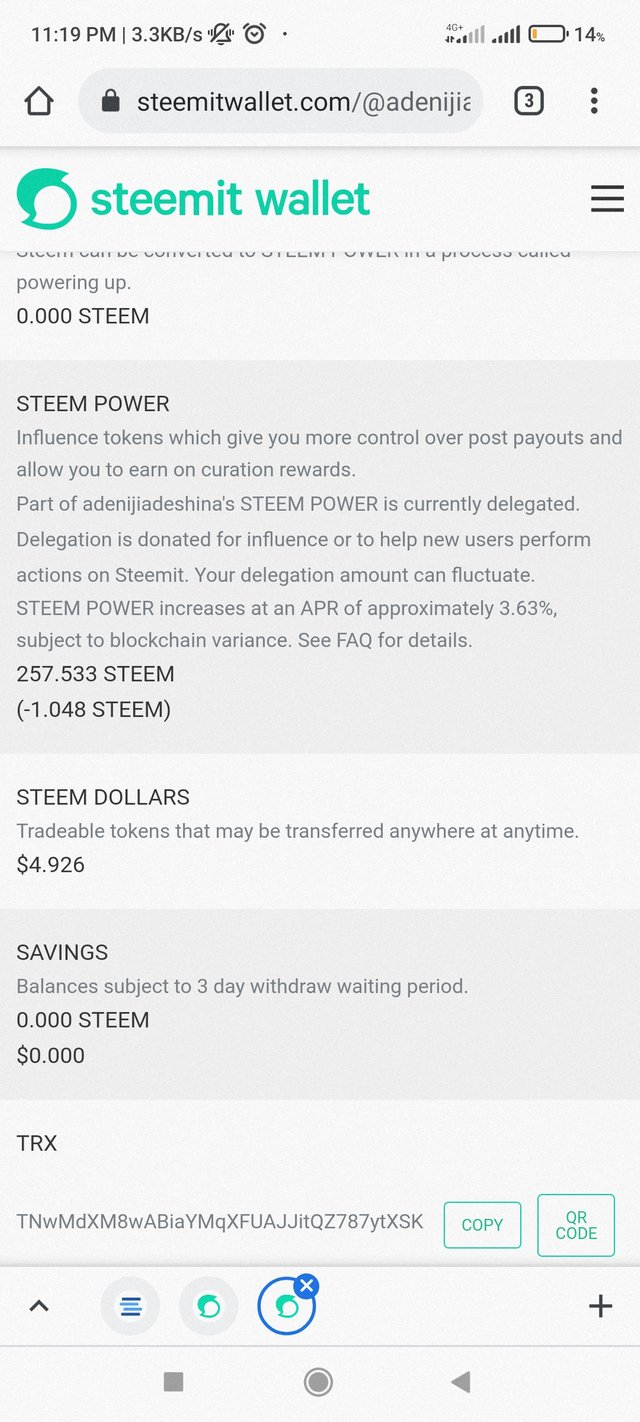
Me disculpa, pero no hubo ninguna confusión. En el momento de la revisión de su tarea, no cumplía con las reglas.