Steemit Crypto Academy S5 - Blockchain, Decentralization, Block explorer - Homework Post for Task 4
(1) Write the definition of blockchain. And how our data on Blockchain is protected from hackers. ? And write details about Data, Hash and Previous Hash tag and explain through screenshot.

Write the definition of blockchain.
Before talking about blockchain technology, I must remember our past transaction technology. Actually, for a long time, the trust in the transactions was provided by individuals, intermediaries, or any other financial companies. It was a bit complicated and sometimes they didn't respond to our transactions properly. Therefore, sometimes we had to lost our money or waste our valuable time.
Asa result of this problem, the world financial system collapsed at a certain level. Then, as a solution for this problem, a person named Satoshi Nakamoto proposed a protocol, creating a new direct electronic payment system between the parties using a cryptocurrency. It was called the world's first Cryptocurrency known as Bitcoin. This was controlled through the use of a new technology called Blockchain. The most interesting part of this Blockchain technology is that a third party was not necessary to handle it.
The first Blockchain was created together with the first cryptocurrency that I have already mentioned above Bitcoin. All cryptocurrencies require the use of Blockchain to be operational, as operational information needs to be transmitted over a network and stored on the blockchain.
To tell the truth, we can define a Blockchain as a distributed information network that contains the detail of a lot of transactions. Blockchain works as an accounting ledger that stores every transaction chronologically. In addition to a single copy of the updated information, several copies have been copied into different ledgers around the world, so it is said to be distributed ledgers. They are located in different nodes that can be simply defined as different computers. Below I have clearly defined the internal process separately.
Below I have highlighted several types of Blockchain
- Public Blockchain :-
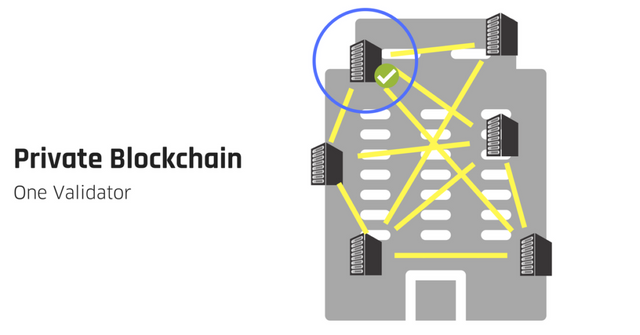
- Private Blockchain :-
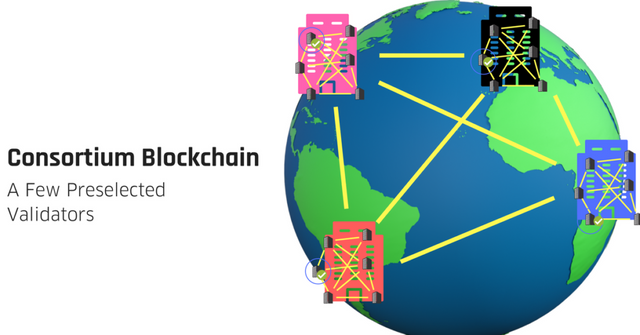
- Consortium Blockchain :-

How our data on Blockchain is protected from hackers ?
As I mentioned above, the blockchain is a distributed ledger among millions of different computers around the world. Sometimes, they act as miners to contribute to validating transactions.
According to every transaction that happened on the blockchain, it records its data one by one within Blocks. The most important thing is that this information will not save in one place. It will save in millions of computers around the world. Therefore, if someone needs to change or delete any detail of one transaction, you have to change that ledge data which has already been recorded in millions of computers. That's why we can directly say, this is the safest method in the world for accomplishing our online transactions.
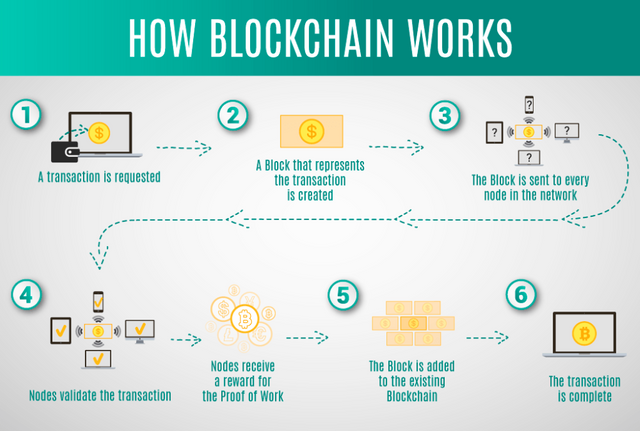
We can clearly understand it when we study the internal process of a Blockchain. I will explain it through a graphical explanation following the below-attached image.
As the first step, someone should request a transaction. Then it will automatically create a block that consists of our transaction data. After this block will copy-paste this data in different nodes within the network. Now miners will validate this transaction using their mining machines. Finally, the block will be added to the existing blockchain confirming the transaction. So, it is completely difficult to change these data by an external party.

Write details about Data, Hash and Previous Hash tag and explain through screenshots.
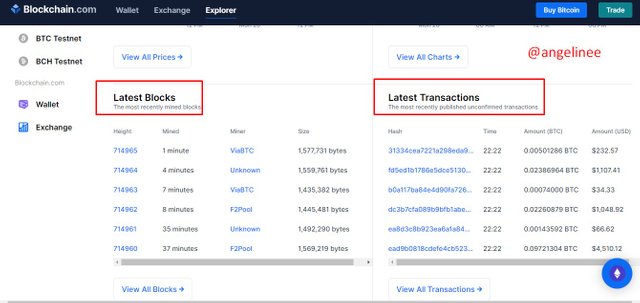
As the first step, I will access to https://www.blockchain.com website. Here we can explore all the above-mentioned data. Then I will choose the Explorer section.
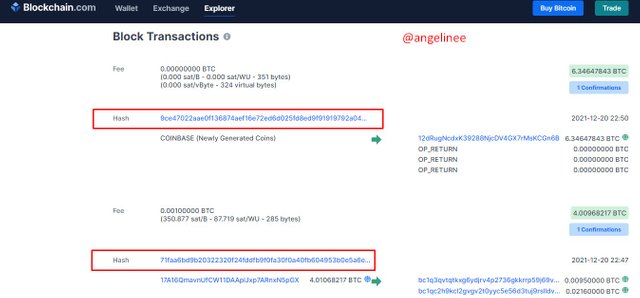
Here mainly we can see two sections. That is Latest Blocks and Latest Transactions. The latest block means that already confirmed transactions and the Latest Transactions mean that still unconfirmed transactions.
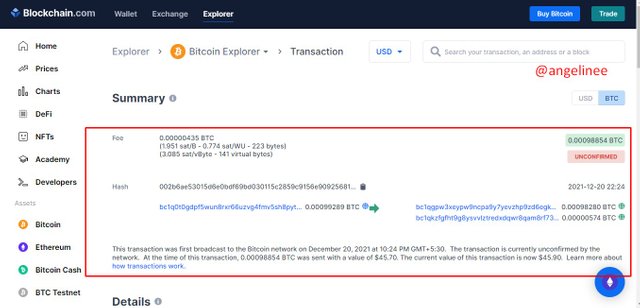
So, now I will choose Latest Transactions to explain Data. Here we can get some details of our transactions as a summary including sender info, the receiver, and the amount of coins that we have transferred.
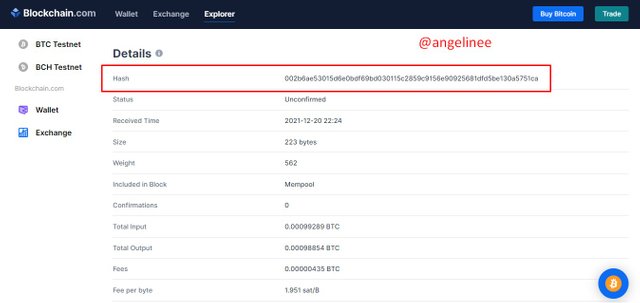
The hash is used to identify the block and all its contents. Once a block is created, a hash associated with it is created automatically. If something is changed in a block, its hash also changes, and we can tell by the hash that a block has changed.
The previous Hash tag is the key that makes a blockchain secure. If someone changes the present hash tag, it will no longer validate as it does not match with the previous hash tag. This way, we can protect our transactions from external parties.

Blockchain technology is the best option for securing our every transaction. When we talk about its internal process, it has some amazing methods to protect our data without deleting or changing. Today, we successfully learned these facts studying blockchain transactions.
.png)

.png)