Simple, effective, early-warning hacker detection tool!
AHHHH HACKERS!!!
Are you concerned about hackers gaining access to valuable information in your computer, email, or cloud storage drive? Me too and you and I are not alone.
We are living in an age where digital theft is becoming a daily occurrence, and it can not only be stressful for us, it can also be damaging to your finances, reputation, and general well-being.
It is time that we start formulating a plan on how to protect ourselves from our adversaries! These adversaries could be nation states, low-level script-kiddie hackers, an ex-partner, a colleague, or even just some random person that finds your flash drive on the ground that fell out of your pocket!
This is my first post that will give you a simple early warning tool that should help let you know if your system is compromised. We are basically, going to set a trap for the hacker, and when they trip it, you'll get a warning.
It's EASY!
This one is so simple, anyone can do it. All you need is an internet connection. These traps can, and should, be placed everywhere! Have a few sprinkled on each computer, your smartphone, your email, your digital drive, your flash drive, basically anywhere a hacker or other adversary may want access to.
Instructions:
- Go to Canary Tokens
- Click on Select your token
- Pick which token you want to create (for this example we are going to use a Word Document)
- Enter the email address you want to be notified to (make sure it is one that your regularly check)
- Enter a very detailed description of this token (I use [location of what device, where on that device is it (like desktop), what type of token, and file name])
- Click Generate
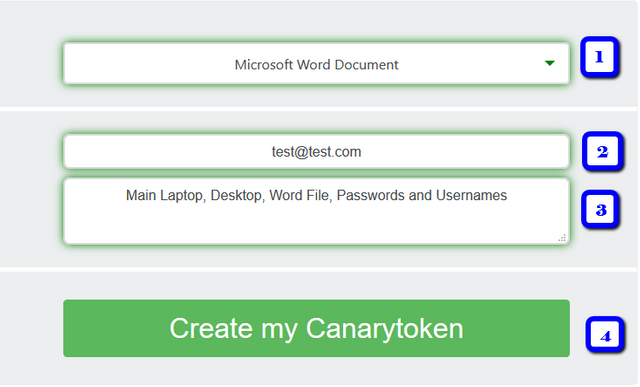
- You will see a button to download your document, go ahead and click that
- After your download is finished (make sure you save it where you want it or move it to the location you specified in step 5), go ahead and open the file.
- Most of you will have to click Enable Editing once Word opens, click that, but from that point out you wont have to anymore.
- Now comes the fun part, you want to fill this document in with FAKE information, that looks real. I have this file for you that you can use as a template. Remember, FAKE information (except your name) but make it look real! Canary Token Template
- Save your document, then rename it to what you called it in step 5.
- You are done!
Extra Security!!!
If you want a bit of extra security and a second warning, for the link for the drive in the Word Document token, use a Web-Bug URL token as the link (be sure to change the display text to something enticing)!
Final Thoughts
Anytime this document is opened from now on, you will get an email with a lot of information about who opened it. You'll get their IP address, location, user-agent string. It really is a simple, but effective way to determine if someone is snooping around your systems. Sprinkle these traps all over, like your email, cloud drive, devices, etc and you will have a nice set of traps for your adversaries!
I hope you enjoyed this and learned a lot today! Follow me for more content and tips on being safe in our digital world!
Bonus Video Link!
Check out this video below for a full walk-through on how to use a Canary Token to see if a hacker is in your system!
Very good anti hackers. Thank you friend
You are welcome! Make sure you make the data convincing but fake. It is a great way to keep yourself safe.
Congratulations @atccodex! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOP@OriginalWorks
The @OriginalWorks bot has determined this post by @atccodex to be original material and upvoted(1.5%) it!
To call @OriginalWorks, simply reply to any post with @originalworks or !originalworks in your message!