Crypto Academy / Season 3 / Week 4 - Homework Post for Crypto Professor @pelon

Hello Steemians, its nice to be in @pelon53 class today. I hope you'll enjoy reading through my assignment.
1.- Explain in detail the hash rate.
Cryptocurrencies like Bitcoin that use the Proof-of-Work (PoW) Blockchain requires miners to add blocks to the blockchain. To create a single block, miners need to produce a 'hash' which is an alphanumeric code that has a fixed length (usually a 64 digit hexa-decimal number).
Now, mining requires a lot of energy and computational speed high powered computer devices which is where the concept of hash rate comes in. The hash rate or hash power has to do with the speed of the mining process.
HASH RATE can be defined as the total amount of computational power exerted by the mining devices usually measured in seconds. So we have for instance, MH/s which is one million hashes per second, EH/s which is one quintillion hashes per second and so on.
The higher the hash rates, the more secure the blockchain. This is because the possibility of an individual or a group of malicious attackers to create a computational power that can control over 50% of the blockchain's hashrate, a concept called 51% attack would be near impossible.
In addition, the higher the hash rate, the higher the possibility of a miner or group of miners adding a block to the blockchain although this comes with its own cost since there is an increase in energy consumption and an increase in the capacity of the computer devices used.
2.- Make the following Merkle Tree:
Merkle tree (Hash Tree), Is an upsidedown tree where every leaf node is labeled with it's unique cryptographic hash block and also every non leaf node is labeled with it's own unique cryptographic hash arising from that of it's child's nodes.
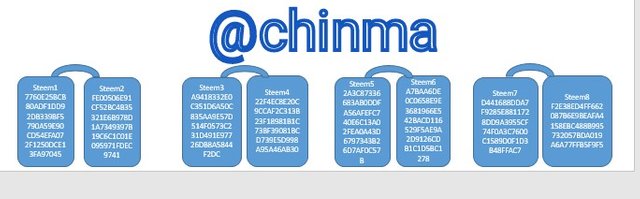
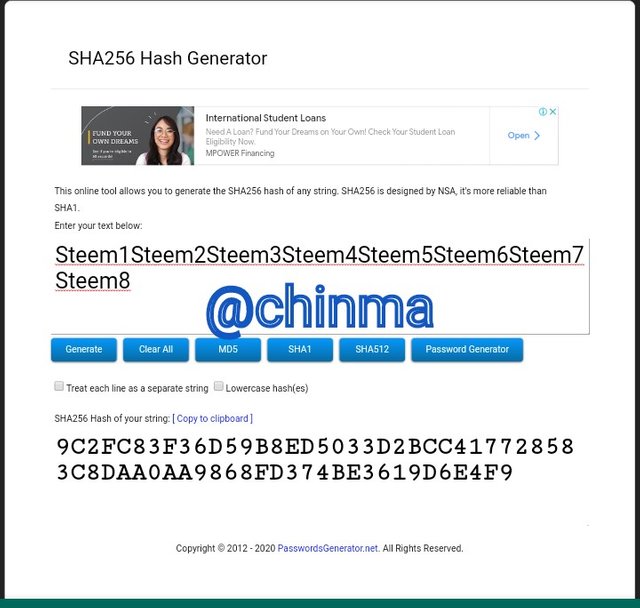
In order to build the Markle Tree, I will first generate the hash of each and every one of the following phrases (inputs) with SHA-256:
Steem1; Steem2; Steem3; Steem4; Steem5; Steem6; Steem7; Steem8.
Steem1 Hash
7760E25BCB80ADF1DD92DB339BF5790A59E90CD54EFA072F1250DCE13FA97045
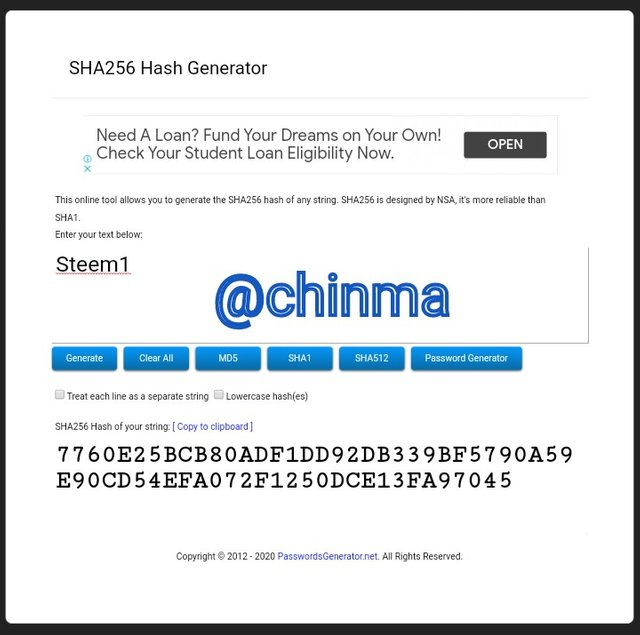
Steem2 Hash
FE00506E91CF52BC4B35321E6B978D1A7349397B19C6C1C01E095971FDEC9741
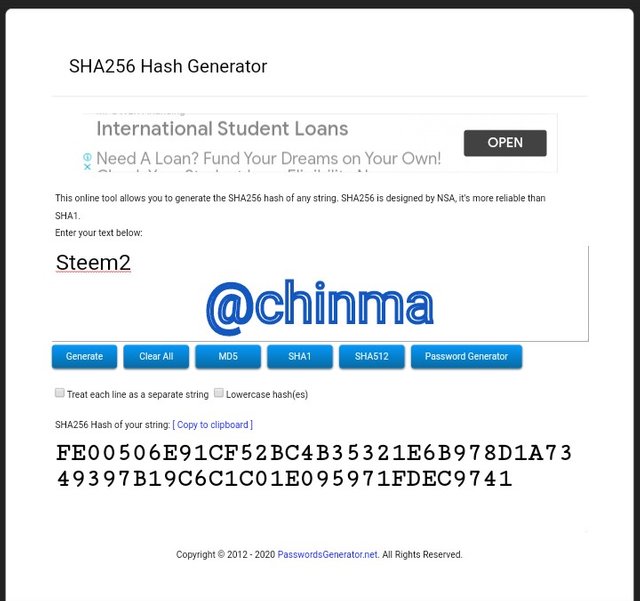
Steem3 Hash
A9418332E0C351D6A50C835AA9E57D514F0573C231D491E97726DB8A5844F2DC
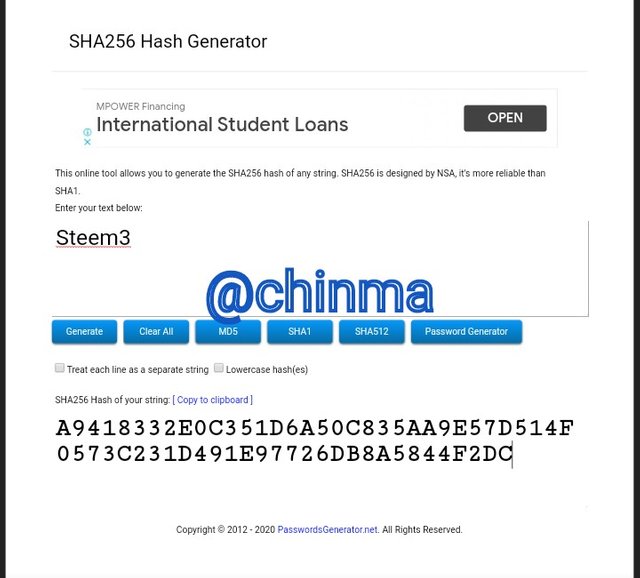
Steem4 Hash
22F4EC8E20C9CCAF2C313B23F18981B1C73BF39081BCD739E5D998A95A46AB30
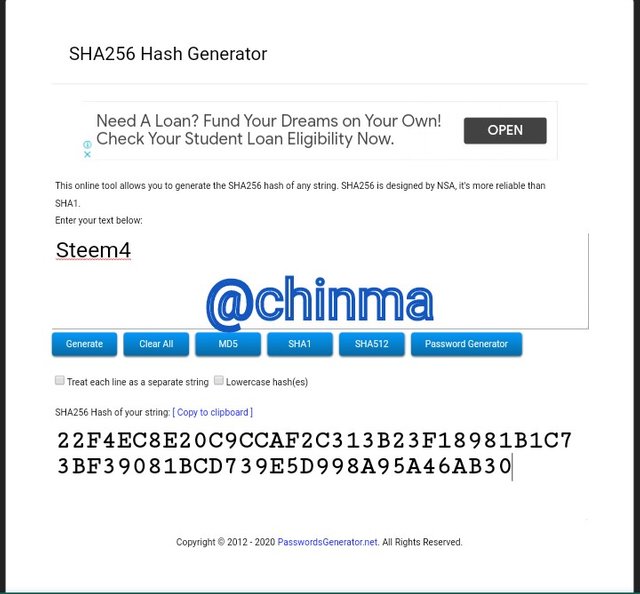
Steem5 Hash
2A3C87336683AB0DDFA56AFEFC740E6C13A02FEA0A43D6797343B26D7AF0C57B
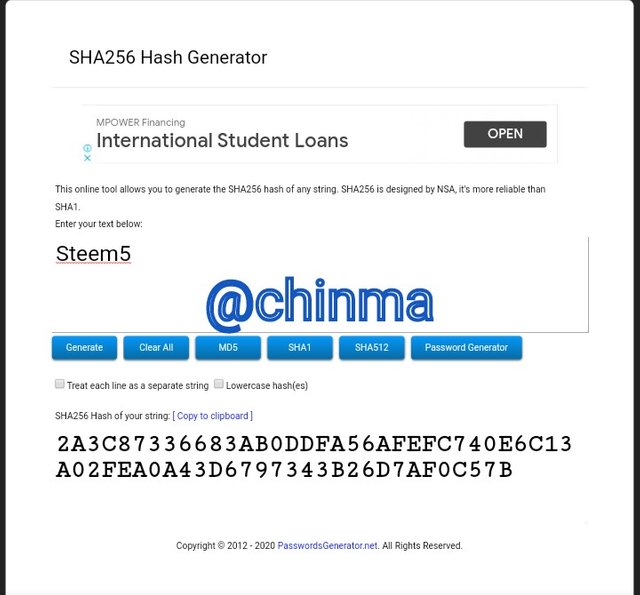
Steem6 Hash
A7BAA6DE0C0658E9E3681966E542BACD116529F5AE9A2D9126CDB1C1D5BC1278
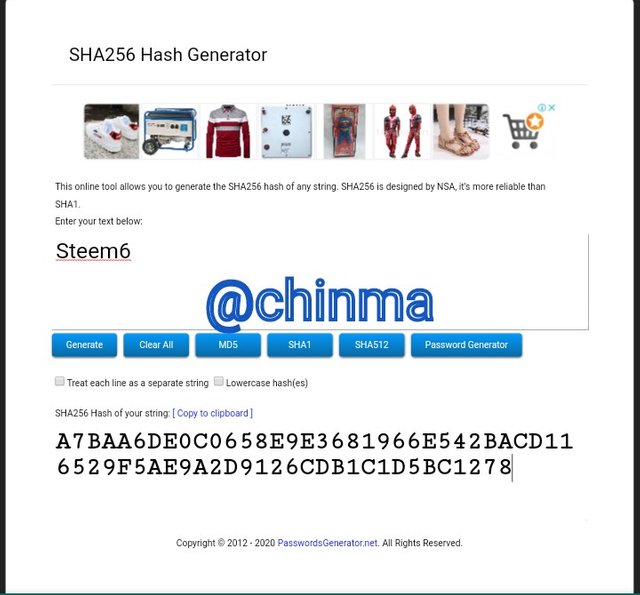
Steem7 Hash
D441688DDA7F9285E8811728DD9A3955CF74F0A3C7600C1589D0F1D3B48FFAC7
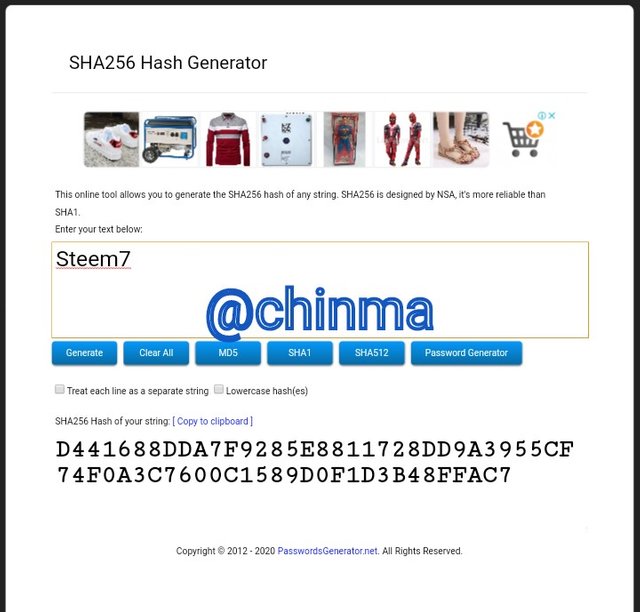
Steem8 Hash
F2E38ED4FF662087B6E9BEAFA4158EBC488B995732057BDA019A6A77FFB5F9F5
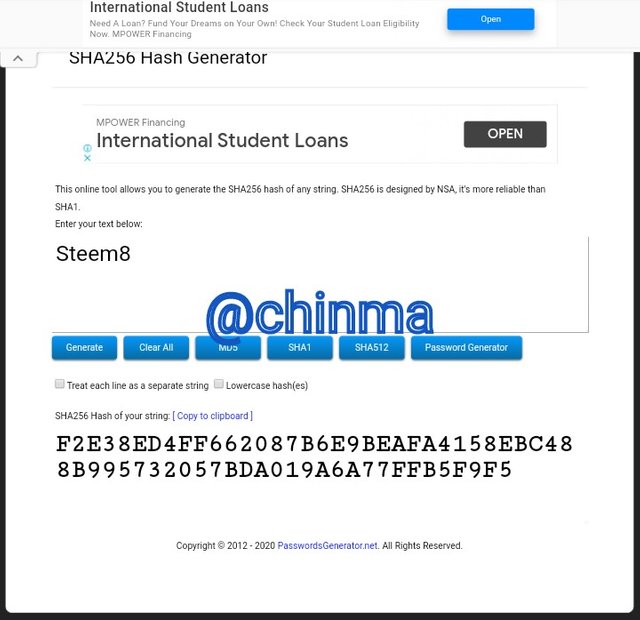
The leaf is as shown below:
Having completed the leaf's, I will begin to generate and build the first branche of the Markle Tree. As follows:
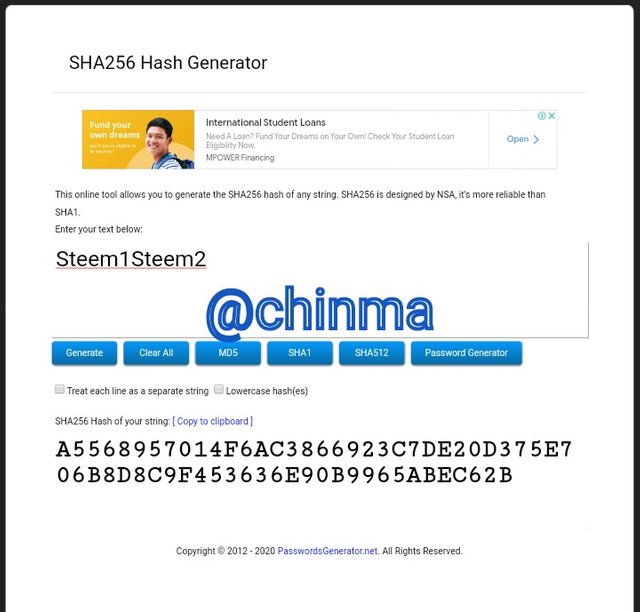
Steem1Steem2 Hash:
A5568957014F6AC3866923C7DE20D375E706B8D8C9F453636E90B9965ABEC62B
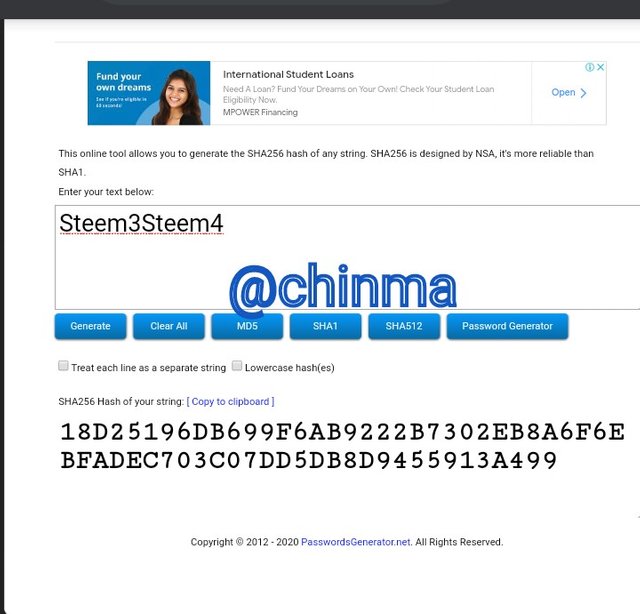
Steem3Steem4 Hash:
18D25196DB699F6AB9222B7302EB8A6F6EBFADEC703C07DD5DB8D9455913A499
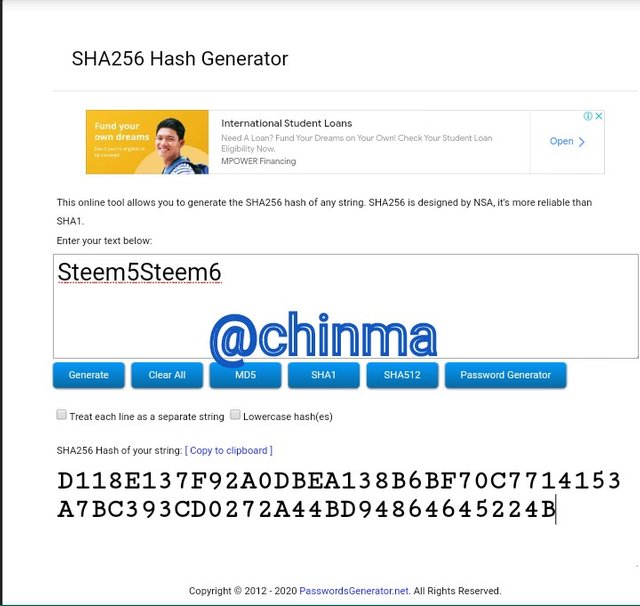
Steem5Steem6 Hash:
D118E137F92A0DBEA138B6BF70C7714153A7BC393CD0272A44BD94864645224B
Steem7Steem8 Hash:
A81D57BA11AEDFA9EFBBA42F6523D75D1EFA50B22C5E3557A21CEFFE87DDFC4A
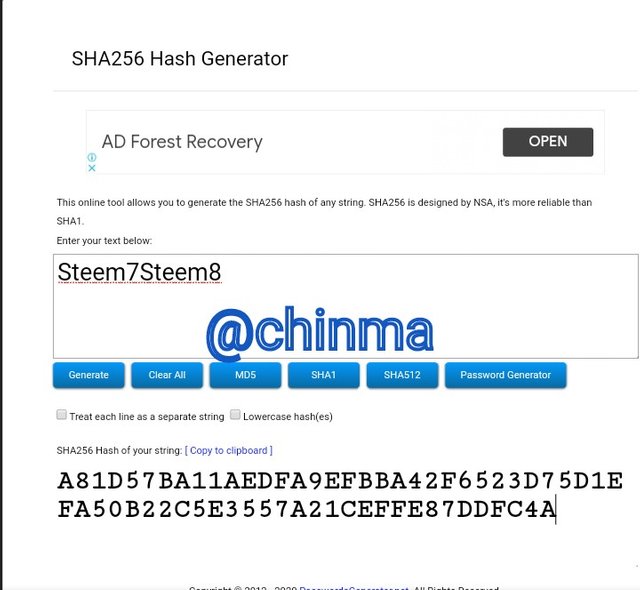
The leaf and the first branch of the Markle Tree is as shown:
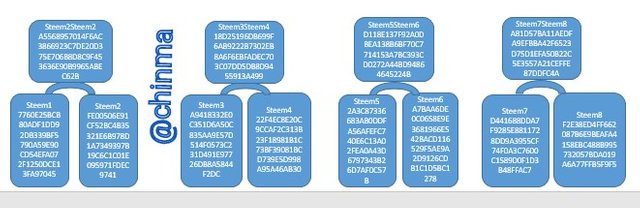
Now let's begin to generate and build the second branch of the Markle Tree.
Steem1Steem2Steem3Steem4 Hash:
8A248C05E69C4F1AA403AD18A7F445FF500C42483DA425CE0C980CDB2FD1AD9B
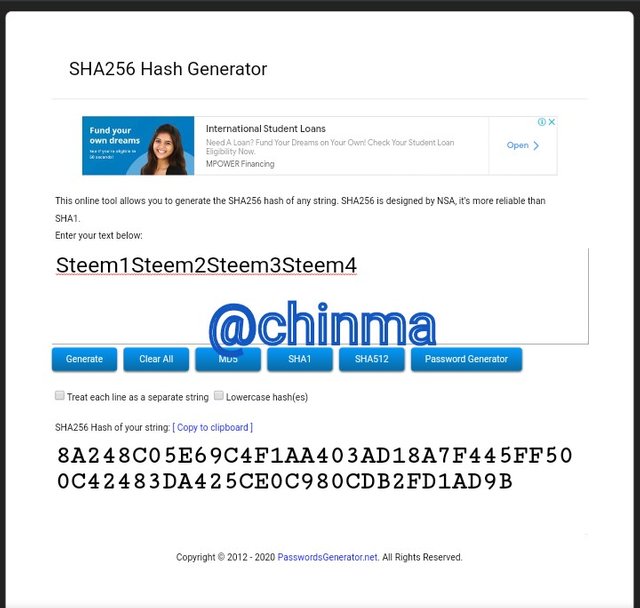
Steem5Steem6Steem7Steem8 Hash:
8B0935AEAB3F51BFA2B0750703EE2387E2B20EB19B0D24227E180C03A851AF17
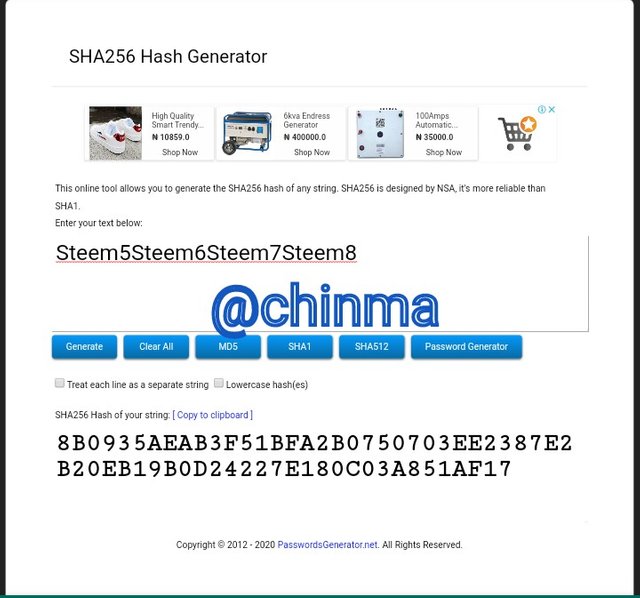
The leaf, first and second branch of the Markle Tree is as shown:
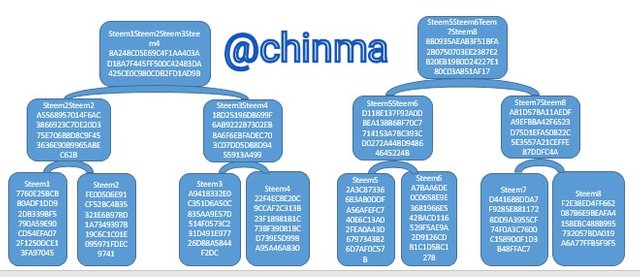
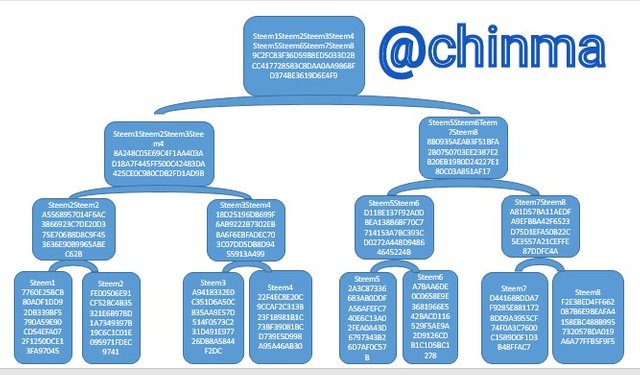
Now, let's generate and complete the task by adding the root, which is the Root Hash:
Steem1Steem2Steem3Steem4Steem5Steem6Steem7Steem8 Hash:
9C2FC83F36D59B8ED5033D2BCC417728583C8DAA0AA9868FD374BE3619D6E4F9
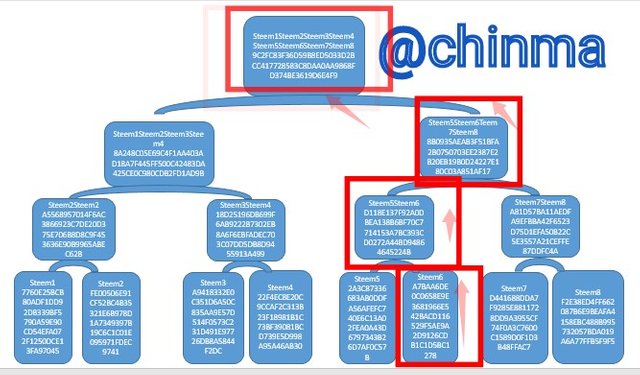
Tell the steps to follow to verify if Steem6 is included in the Markle Tree.
The steps to follow in order to verify if Steem6 is in the Markle Tree.
We have to look along the Steem6 path.
First, we follow the Steem6 path, in the following order:
- Start with the Steem6 leaf (bottom).
- Work your way up through, it's siblings Steem5Steem6.
- Next, Steem5Steem6Steem7Steem8
- Finally, Steem1Steem2Steem3Steem4Steem5Steem6Steem7Steem8 (Markle Tree)
Now, turning the tree around, so we can go from the Markle Tree (Root) to the Leaf:
- Markle Tree (Steem1Steem2Steem3Steem4Steem5Steem6Steem7Steem8)
- First branch (Steem5Steem6Steem7Steem8)
- Second branch (Steem5Steem6)
- The target leaf (Steem6)
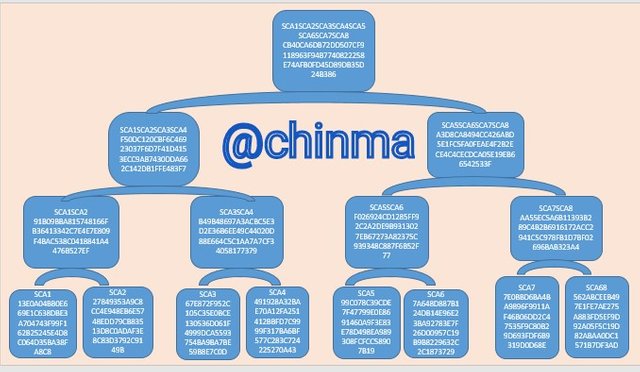
3.- Using the SHA-256; you must place each complete hash in the Merkle Tree.
Transaction (tree leaves): SCA1; SCA2; SCA3; SCA4; SCA5; SCA6; SCA7; SCA8. Explain each step, show screenshots.
The following are the process to generate and build the Tree leaves( SCA1; SCA2; SCA3; SCA4; SCA5; SCA6; SCA7; SCA8.) into a Markle Tree:
SCA1 Hash:
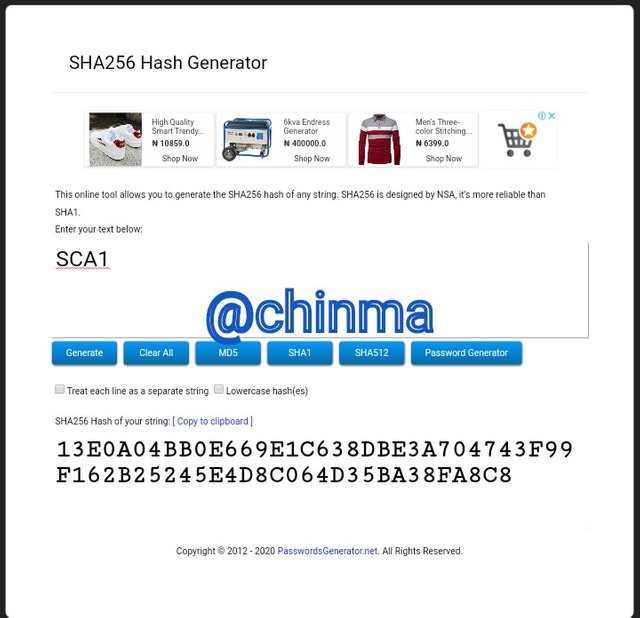
SCA2 Hash:
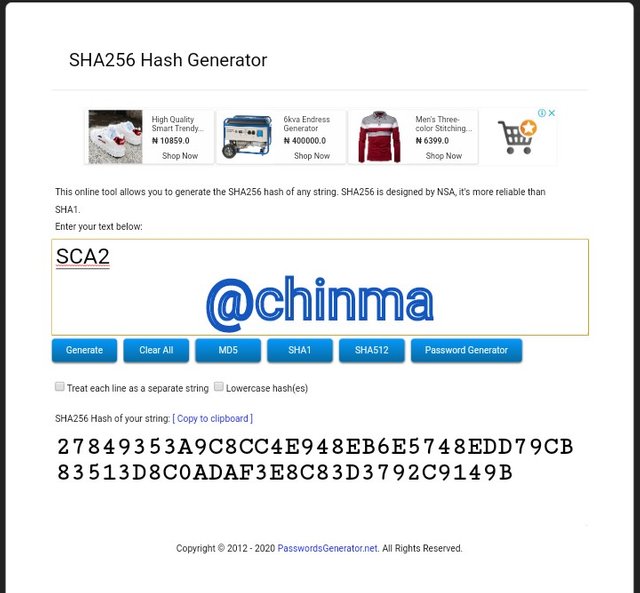
SCA3 Hash:
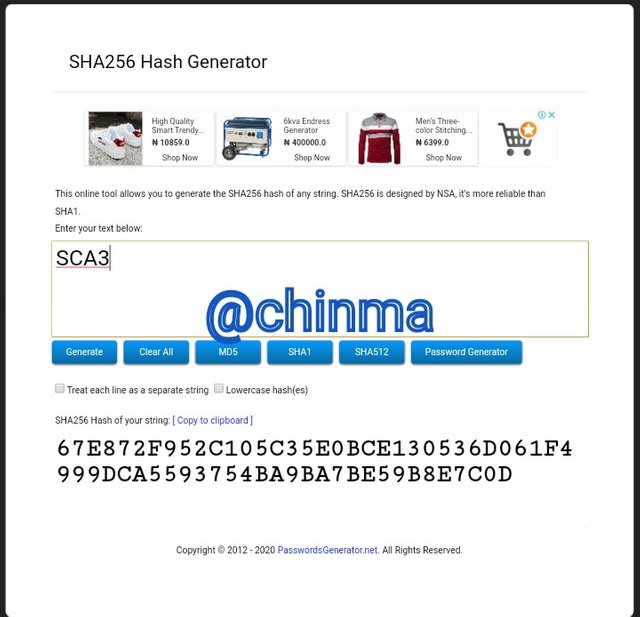
SCA4 Hash
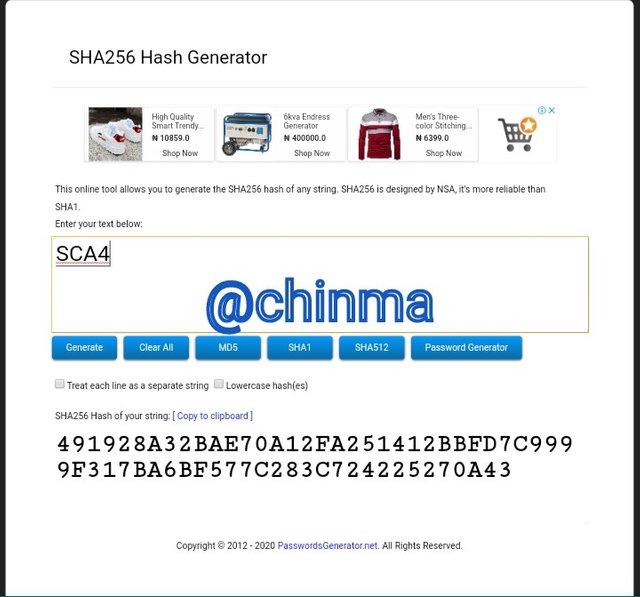
SCA5 Hash:
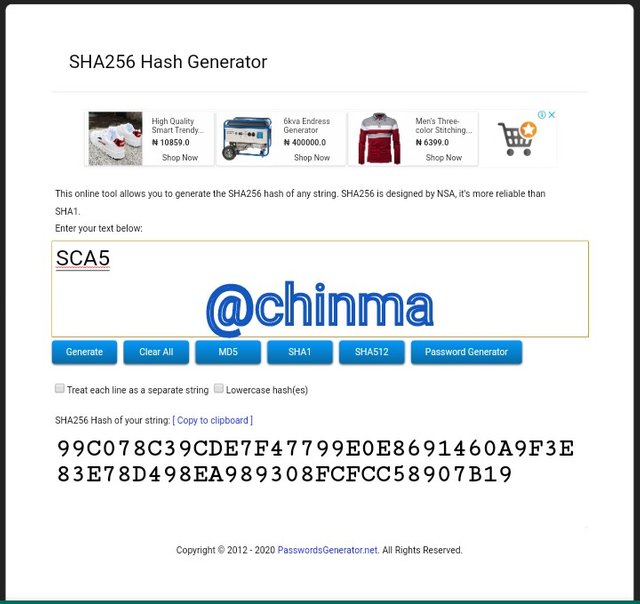
SCA6 Hash:
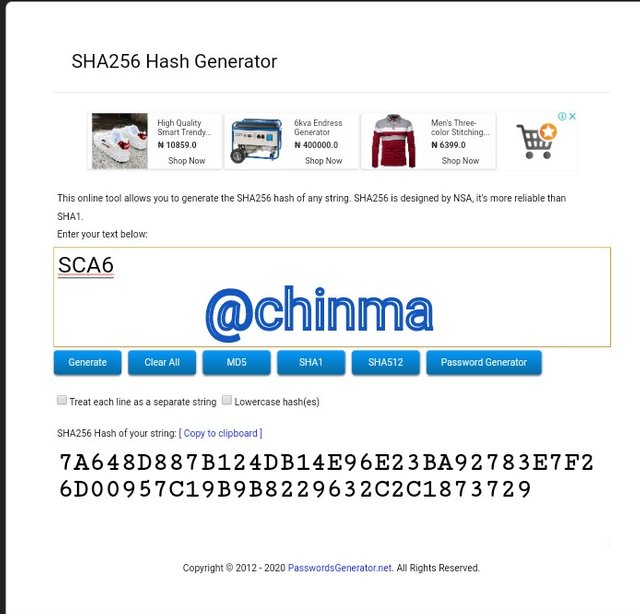
SCA7 Hash:
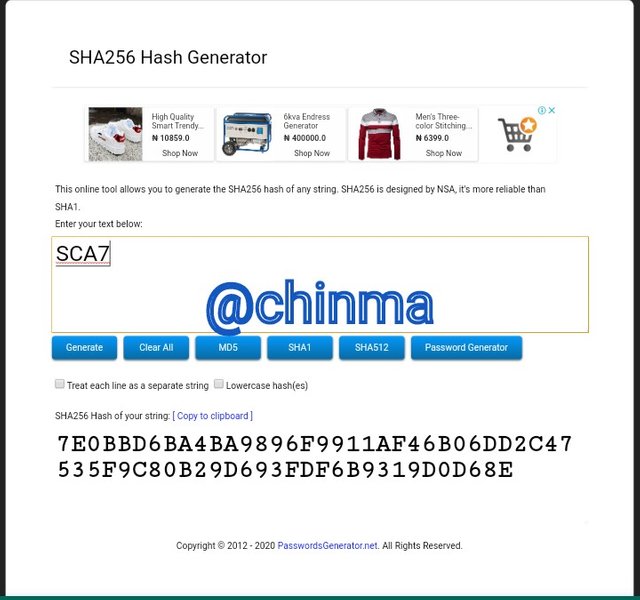
SCA8 Hash:
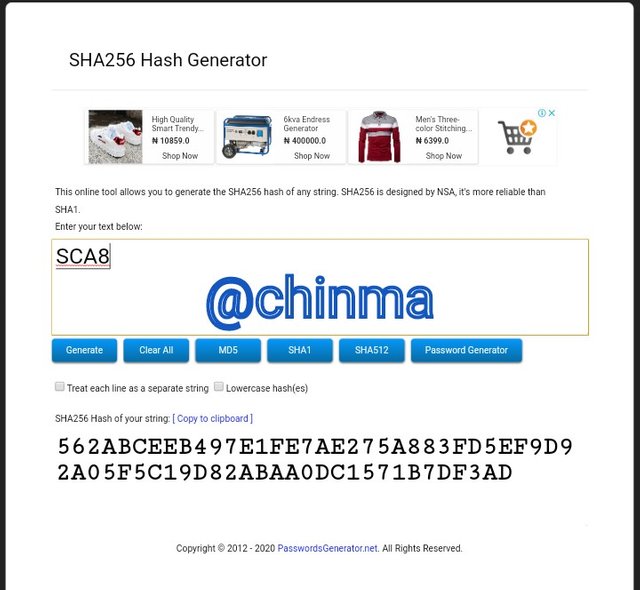
Now, let's begin the second phase of the Markle Tree construction:
SCA1SCA2 Hash:
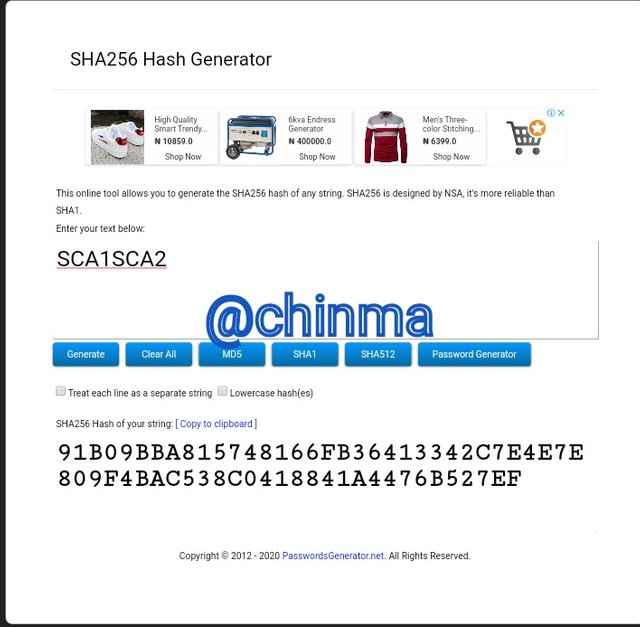
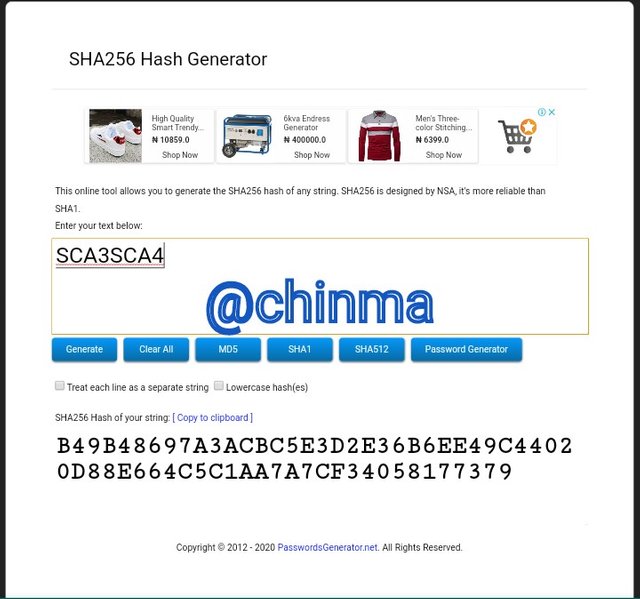
SCA3SCA4 Hash:
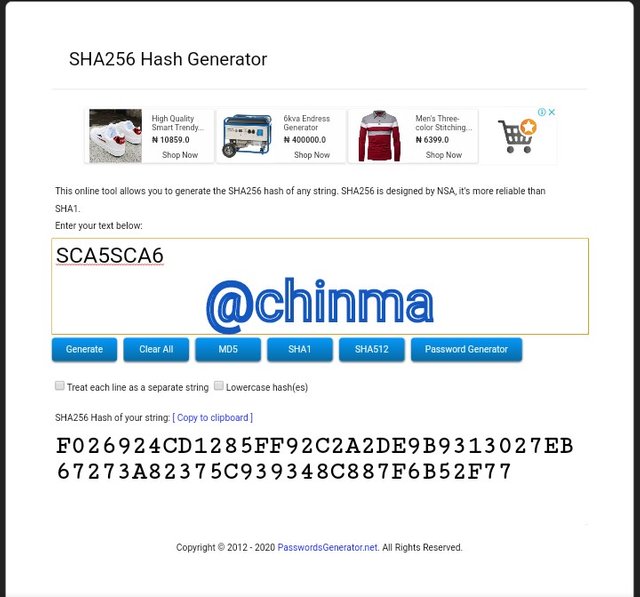
SCA5SCA6
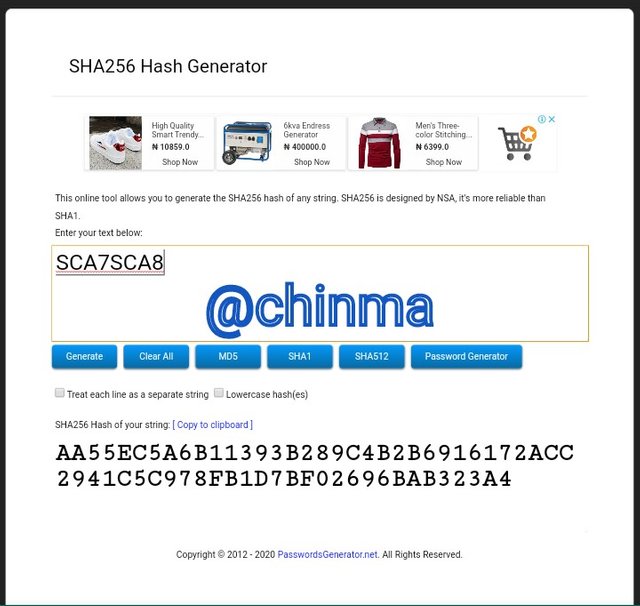
SCA7SCA8
In this phase we hash the individual branches:
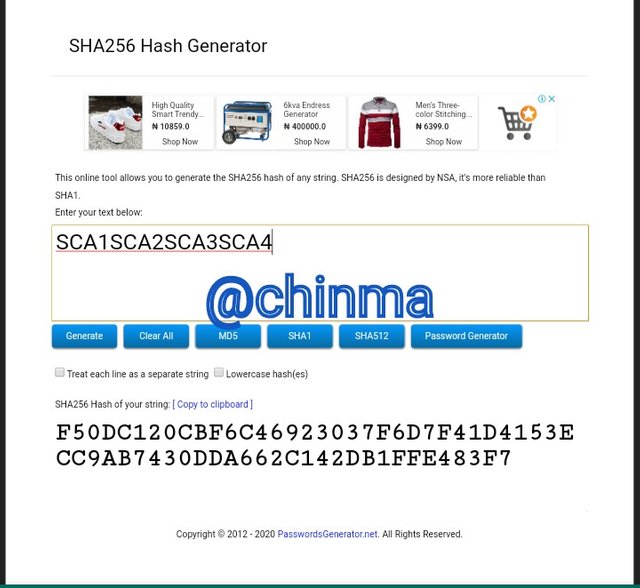
SCA1SCA2SCA3SCA4 Hash:
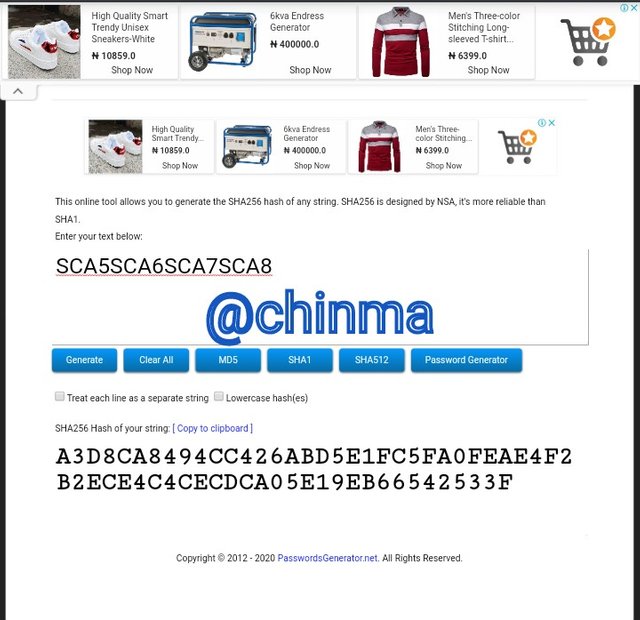
SCA5SCA6SCA7SCA8 Hash:
Finally, it's now time to hash the last phrase to generate the Markle Tree.
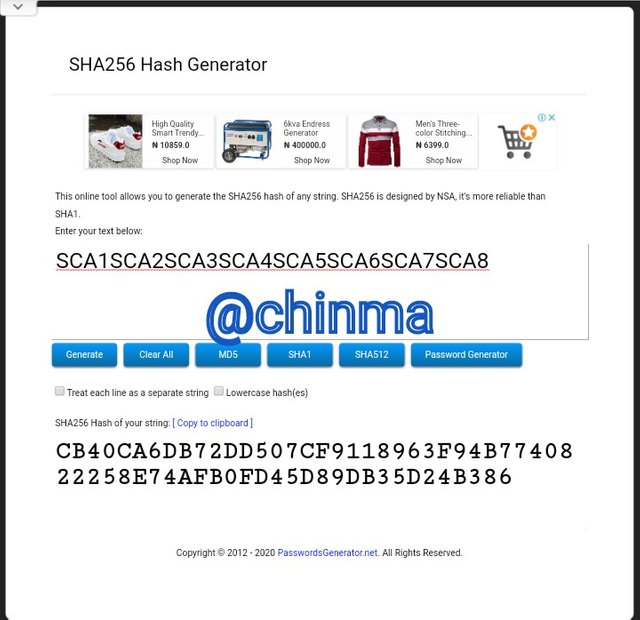
SCA1SCA2SCA3SCA4SCA5SCA6SCA7SCA8 Hash:
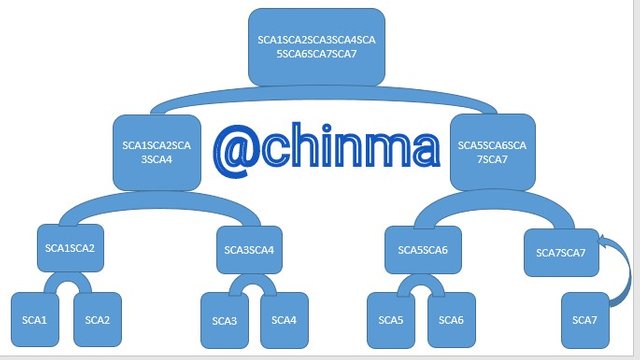
If the number of leaves on the tree is odd, what should you do? Explain.
When we encounter an odd number during the building of the Merkle Tree. We then have to concatenate (add up) the very last node with itself.
Let's say we have SCA1 upto SCA7.
The illustration is as shown below:
Conclusion
We have seen the hash rate as a product of the speed of the computer devices used in processing transactions to add a block to the blockchain. Furthermore, to make the system more fluid and secure, a higher hash rate is required.
Although we have ascertained that a higher hash rate gives a great degree of security to the blockchain, the Merkle tree has a huge role to play as it not only aids data verification and validation as learnt from the lesson, it also ensures that security and integrity is distributed in the blockchain.
You've got a free upvote from witness fuli.
Peace & Love!