Intruducing Web Server
BASIC THEORY
A. Web Server
Web server is a service provider with HTTP protocol. The web server is also known as the HTTP server, providing the ability to send hyper-text documents to users. Hypertext documents that will later be used to serve as a view. The normal Web server runs on port 80. The secure version of the web server, or HTTPS server, runs over port 443. Ordinary HTTP servers, providing access only to files that are inside the HTTP server folder.
HTTPS is protected with encryption so that the data sent is secured. Websites that require extra security like banks, transactions, emails, file storage using HTTPS. Although some do not use HTTPS, but inevitably such critical webweb must use HTTPS to get customers. When an HTTP server serves users, most of the data that is sent is HTML format. But the HTML itself works compactly with files of other formats, such as CSS to organize the view, JS to manage interactions, and other extras like images.
Usually, when a user requests a HTTP Server, the HTTP server responds by providing the original file that is on the server. But, it does not have to be that way, according to how the HTTP server was implemented. HTTP server is dynamic, if you want to add the functions in the system, can be through two ways. That is with the re-creation of HTTP server software, or use server-side programming languages or server side scripting. By using a language like ASP, or PHP, the HTTP server can provide different functions without the need to rewrite the code for the HTTP server software itself.
HTTP server does not necessarily only provide data to users, HTTP server can also request data from users either using the form, or by uploading files. HTTP server is now not only to provide services through web server in the form of big machine. Now, some tools use HTTP as the user interface, such as router, printer, webcam. But in these small tools usually HTTP is used in local network only.
B. HTTP Server Type

There are two types of HTTP servers, namely Kernel and User. The kernel version of the HTTP server has more speed because it is directly integrated with the OS and is intended for HTTP servers. So it has direct access to lower level resources such as network adapter, buffer, or memory. The user-type HTTP server is longer and limited, because they do not have direct access to hardware and lower-level resources. They should first ask the OS for resources, then they should share resources with other applications. On Windows systems, can use IIS, or on Linux using TUX.
C. Web Server Limits
Web server is limited, he has limitations on how many users can be served simultaneously. Therefore, there is usually more than one web server provided if the number of users served is very large. The web server's boundaries are affected by several factors:
- Web Server Configuration
- HTTP Request Type
- Type of Dynamic or Static Content
- Hardware or Software Boundaries
When this limit is reached, then the web server will experience stuck and unresponsive.
Usually, these limits are achieved when there are several things that happen.
- The number of users connected simultaneously. When a user is connected simultaneously. Then the resources of the web server will be fragmented also at the same time. The input output process takes a long time, the reading of files many times in a time that is not much different will make the web server lose balance and finally can not complete the request.
- DDOS attack or Distributed Denial Of Service, making the server overwhelmed serve the attack. As a result, other users will not get the requested resources.
- The existence of viruses that spread through millions of computers can hamper the performance of the server. If there are one million computers infected, then they will try to spread through the internet network, and one of the services that are also hit by a web server is attacked.
- A slow network will result in the server memrposes a request longer than usual. Things like this cause bottlenecks, so when the server should finish processing, he has to wait a long time because the network is slow, hinga finally all the loads accumulate and the server finally down. Some ways can also be done to make the boundaries of the web server is not reached. By optimizing the existing resources, and capabilities of the web server.
- Arrange network traffic by limiting a request with a firewall, and also filter out bad HTTP requests, as well as set bandwidth.
- The web server must use cache technology, so the same resource requested many times does not need to go through the old process. Moreover, through the IO path is solid and slow.
- Using a web server will make the system burdened, but when using two web servers, the other server can rest and free up processed resources, and other web servers work on some of the web server's responsibilities. Breaking up this web server is one very effective way, but because the cost factor of making over web server is not a cheap price.
D. HTTP protocol
Each HTTP request has two parts, namely header and content. Headers for requests and headers for different services. HTTP server only responds when there is demand. The HTTP request is provided via the URL, also the HTTP method used.
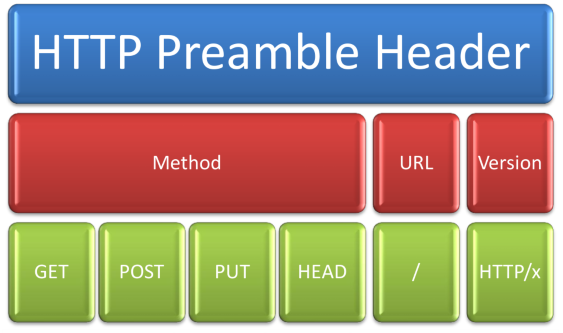
HTTP header header, consists of three parts. Methods, URLs, and HTTP versions. Method can contain GET, POST, PUT, HEAD. The URL may contain the requested resource address, and the version indicates the version of the HTTP protocol (now 1.1 is currently written) HTTP server responds differently with different method, url or version. GET method, used to retrieve data. While POST method, used to install data. The PUT method, used to put data, and the HEAD method is used to request information. Unlike the opening header of the request, the response header shapes like this.
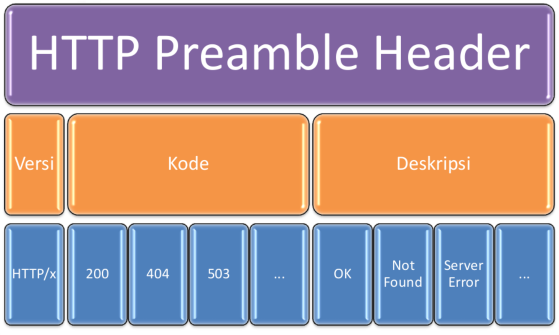
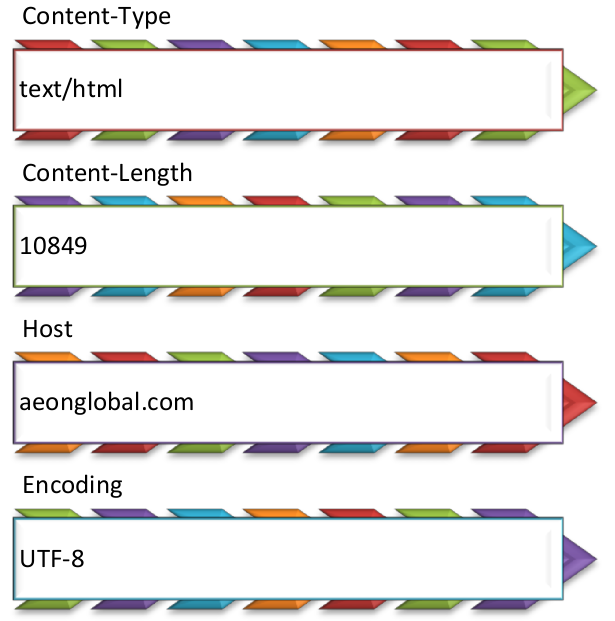
After the opening header, there will be more headers. This header is in the form of a mapping, like a dictionary, with its name and and value. Header shaped mapping is more numerous. Not following a certain pattern, and ending with a blank line.
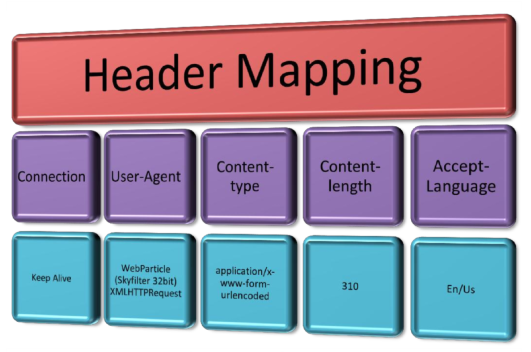
The picture above is the structure of the request header mapping. The contents are unlimited, we can even add headers according to our needs.
The formats of header mapping:
<mapping_name> : <mapping_values>
Example –-> Connection: Keep-Alive
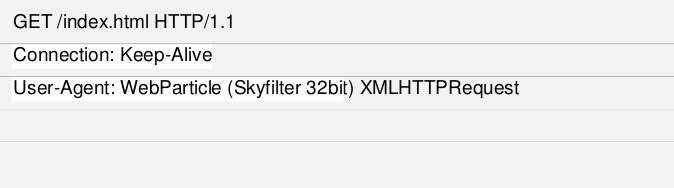
For example, if on the web server there is a file with the name index.html ̧maka way to get the file. The user must submit to the request web server that is shaped like this.
By sending a request as above, then the server will respond with a form like this.
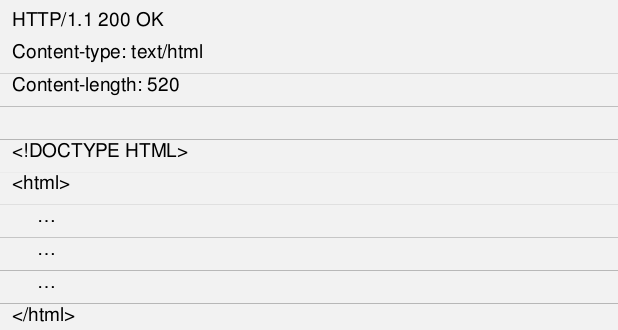
After the last header mapping, there is one blank line. In the header mapping request there is also a blank line, but is not visible because the user requesting the service does not provide any data.
E. HTTP Server Type
Not all HTTP servers work the same way. There are HTTP servers that only provide static files, some of which provide dynamic files. As long as the application serves the request in accordance with HTTP rules. Then he is called HTTP Server.
- Staticlet
Staticlet is a web server that is not so popular, its ability is limited and can only serve the provision of static files. Unconfigurable, and more useful as a portal for creating HTTP-based one-way sharing files. - Apache
Apache is one of the popular web servers, equipped with PHP language, CGI (Perl, Python) capabilities, as well as configuration using .ht file. Apache can do a good job, configuration is also a lot and very easy to learn. - Nginx
Nginx is one web server that works fast. Nginx uses C ++, one of the fast-working languages. - IIS
IIS is a web server from Microsoft, it is able to use and optimize Microsoft technologies such as .NET, ASP, WCF, Hyper-V, etc. - Glassfish
GlassFish is one server that uses Java as its platform. Java itself is an independent platform that can run on various platforms. - Lighttpd
(Pronounced "lighty") is an open-source web server optimized for speed-critical environments while remaining standards-compliant, secure and flexible.
F. Virtualhost
Virtualhost is a feature that exists on a web server that aims to a web server can accommodate multiple sites, with just one web server. This is quite efficient as long as the sites that are accommodated do not get very high traffic. The web server can distinguish the various requests of this site from the requested domain. Each request requested to the web browser will be answered in accordance with the destination domain by the client.
G. What is Secure Socket Layer SSL (Enrichment)
SSL is short for Secure Socket Layer which is a transport layer protocol used in secure Internet connections. If you want an internet connection via a secure way, then use an SSL connection.
SSL offers three levels of security:
- Authentication: Ensure that the data received comes from an explicit person.
- Confidentiality: Protect data from an attempt to read by unauthorized recipients along the way.
- Integrity: Ensure that the original message, has not changed in its journey.
SSL was developed by Netscape Communications in order to send data securely over the internet. If you've ever noticed in an internet browser using HTTPS, then this Internet connection is using SSL commonly used in an online transaction. So HTTPS is a protocol for transferring data that is encrypted through the web.
Differences HTTPS and HTTP
- HTTPS connects through port 443, while HTTP uses port 80
- HTTPS sends / receives data with encryption over the SSL protocol, while HTTP sends data with plain text
In online transactions, you may often see your online store (online store) you use HTTPS in financial transactions over the Internet. SSL operates between the Application and Transport layers in the OSI model. SSL does not work transparent automatically, because it can only if application protocols are explicit indeed implemented.
SSL uses public-key encryption for authentication purposes and symmetric key encryption for encryption of sent information. For public key, SSL encryption using the Rivest-ShamirAdleman (RSA) encryption algorithm, therefore depends on the implementation of a public key infrastructure (PKI) supported. Data integrity is ensured by an integrity checking mechanism called the message authentication code (MAC).
Authentication Process
An SSL session starts when a client with SSL-enabled requests a connection with a server with SSL-enabled via TCP port 443, the SSL port. This will initiate an SSL connection between client and server. All websites that use SSL have a URL with HTTPS prefix. The server then sends the digital certificate and public key to the client.The client server then negotiates which level of encryption is acceptable which is usually 40-bit, 56-bit, or 128 bit upwards. The client then generates a secret session key which is then encrypted using the public key of the server and then sends it to the server. The server then decrypts the secret session key using its private key. From this point onwards, secret key cryptography is imposed and then the session key is used to encrypt all data exchanges between client and server, providing a secure private communication.
SSL is certainly not free from problems just like that. All web transactions with SSL will increase server processing overhead. Sometimes it doubles its processing overhead rate over without using a secure SSL connection. With the same hardware, the processing load level using SSL will be very heavy compared to without SSL.
In addition, SSL becomes difficult to implement in e-commerce using web server farms and server load balancers. This is because SSL is designed for clients to use the same IP address during the session. To overcome this problem, typically used special hardware called SSL Accelerators to take over processing load and cache sessions to other servers to improve performance.

Source :
- wikipedia.org
- Image 1 - 2 - Dell PowerEdge