#CoolTools for hackers! A really powerful one: NMAP
If you are learning about cibersecurity and pentesting, you need to know the basic tools to perform the basic tasks. And one of those tools is: Nmap.

Nmap ("Network Mapper") is a free and open source utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. It is a really popular, easy to use tool and you can find a lot information about it on the Internet, but I will try to show you the basics in this post.
By default, it is installed in your Kali Linux machine. You can check it typing in the console: nmap.
Anyway, you can download it from: https://nmap.org/download.html and follow these instructions to install it: https://nmap.org/book/inst-source.html
Once it is installed, you can start "playing" with it but take into account that some of its features can be illegal to use in your country. Always use this tools at your own risk and only for learning purposes.
Let´s see a few command examples.
- Basic Nmap scan against hostname or IP:
nmap cyberspacekittens.com
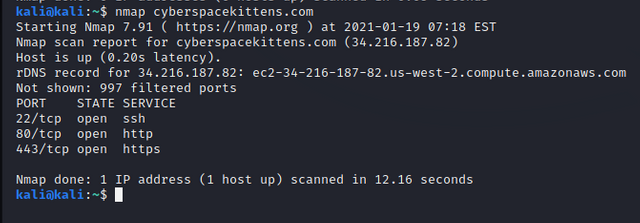
As you can see in the screenshot above, the main usage of the tool will tell us which ports are open (and some more information is given as location and owner of the host). Nmap command can be performed with the next format, too: nmap 1.1.1.1
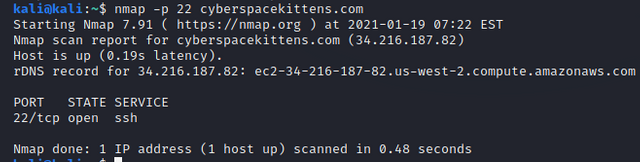
- Scan a specific port:
nmap -p 22 cyberspacekittens.com
Scan IP ranges:
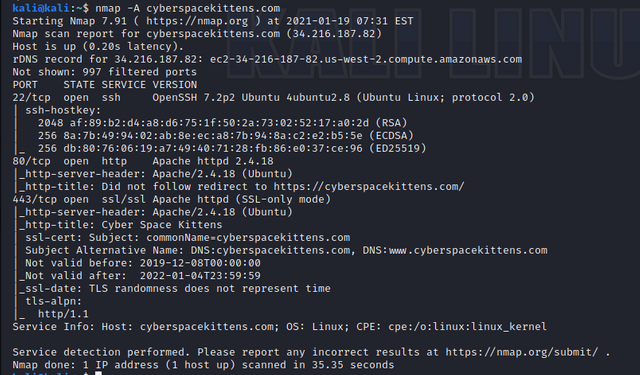
nmap -p 1.1.1.100-200 (the last 100-200 is the IP range set)Scan to find out information about the OS:
nmap -A cyberspacekittens.com
Really helpful command. Once you know information about the server, you can search for tested exploits.
Scan hosts and IPs reading from a file.
The "-iL" parameter lest you read from a specified file, where you can list any site for the scan.
nmap -iL list.txt
list.txt could contain something like this:
google.es
marca.com
cyberspacekittens.com
192.123.24.12Set timing template, from 0 to 5, where 5 is the fastest setting.
A faster execution can be performed by using -T<0-5>
nmap -A -T3 cyberspacekittens.comNmap Scripting Engine.
The NSE is a really powerful feature. It allows users to write (and share) simple scripts (using the Lua programming language ) to automate a wide variety of networking tasks. Those scripts are executed in parallel with the speed and efficiency you expect from Nmap.
nmap -sC performs a script scan using the default set of scripts.
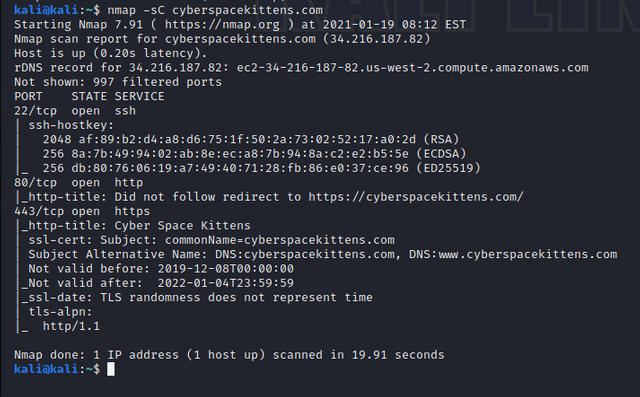
--script <filename>|<category>|<directory>/|<expression>[,...]
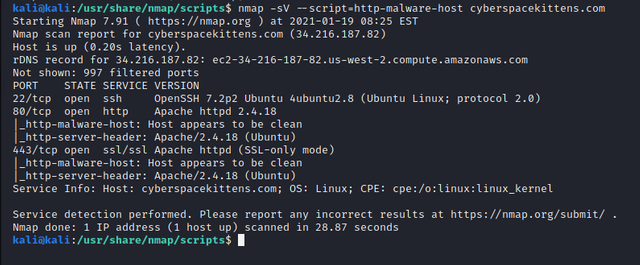
Runs a script scan using the comma-separated list of filenames, script categories, and directories. Each element in the list may also be a Boolean expression describing a more complex set of scripts. Each element is interpreted first as an expression, then as a category, and finally as a file or directory name. These scripts are predefined in /usr/share/nmap/scripts. One example is: http-malware-host, used to detect malware infections on remote hosts.
I hope you find this post useful, more #cooltools will be brought to you. Have a nice week!
🎁 Hi @georgygar! You have received 0.2 STEEM tip from @panosdada!
@panosdada wrote lately about: My Actifit Report Card: January 20 2021 Feel free to follow @panosdada if you like it :)
Sending tips with @tipU - how to guide.
Hello you earn a tip for my Giverway in Community!
Also you have a change to win 2.50 STEEM in the end of the week 24/01/2021
Keep post in community and be active
Many thanks for doing that
@tipu !tip 0.2 STEEM
Thank you sho much! @panosdada
You welcome 🙂