Hacking-- How Hacking actually looks like. Is your password hacked? How to check?
Hello Everyone!
Hacking and stealing information like passwords and other private data is very common these days. The hacker tries to steal your data and by many methods. They will steal your data and sell it on dark wek or post it on the internet publicly. In this post, we will know how exactly hackers hack your private information and we will know Is our credentials available on the internet or not. In order to protect ourselves first, we need to know how the hacker was able to steal your credentials? Well there are a lot of ways to by which the hacker can steal your credentials but the main three methods are

- Breaches
- Social Engineering
Man in the Middle.
Let's discuss each of them and see what they mean.
Breaches
Your password may already of there. Shocked? I was as well when I read about it. This happens when data breaches. When we create an account on a website they store our data and when the hacker attacks the website and steal all the information your password and other information(if you have provided) are also gone. Most of the time the hacker sells the information on the dark web or posts it publicly its hacker choice of course. So if you are the user of a website that is hacked then your data is leaked too.
Most of the websites Hash your password before they store it in the database. then if the website got breached then the hacker has to decode the password into plain text before selling or posting it on the internet. But even if the password is hashed it is not a big deal of a hacker to crack it because if he can breach a website he can crack its password also, it is difficult to crack password but not impossible. Most of the famous website like twitter, LinkedIn, etc already suffers manor breaches and all the data from theses website are publicly available on the internet latterly everyone can see it. There is a Breach compilation that contains 1.4 billion Email-Password combinations. If you want to check whether your Email-Password is compromised or not you can visit How I been pwned
This website allows you to check if your password is in the breaches or not. Just visit this website and type your Email. If you are safe it should tel, you something like this.
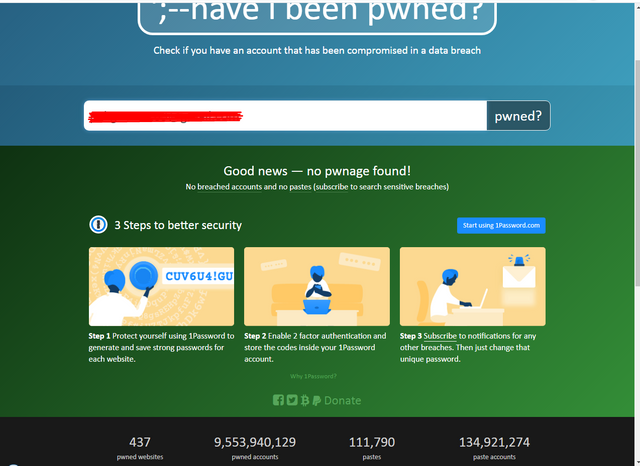
And if your password is compromised then it will tell you that your password is available on the internet and you should change it. Even if your result on this website is positive there is still a chance that your password is may be available on a website that is not popular and is not on the list. Down in the website you can see the websites that are breached recently
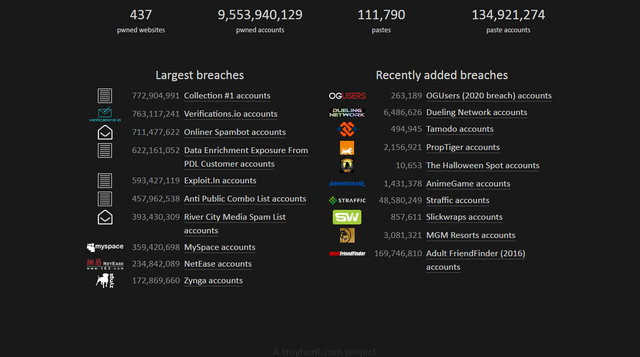
To avoid breaches like this better use different passwords for every website( It is quite difficult but we have to do it for sake of security :P). Use a trussed password-manager to generate a unique password every time.
Social Engineering.
This is lithely you are giving away your password to a stranger on the internet the hacker can pretend to be some else to extract your username and password.
For Example, you revive a message with a link that claims to give you free Instagram/FB likes, You click on the link and the website asks for your cradinationals. You give them your username and password thinking that this is a legit website but you don't know that you are hacked. The hacker has your username and password. He can do everything he wants with it. Sometimes the hacker installs a Rat in your computer through social engineering. Now you will be thinking what is RAT so according to google
The RAT Virus is a type of malware program that creates a virtual back door on your computer. That back door provides hackers with remote access to your system whenever they want to take advantage of it.
The RAT virus will give complete access to the hacker by which he can see your password and even change your settings on your computer.
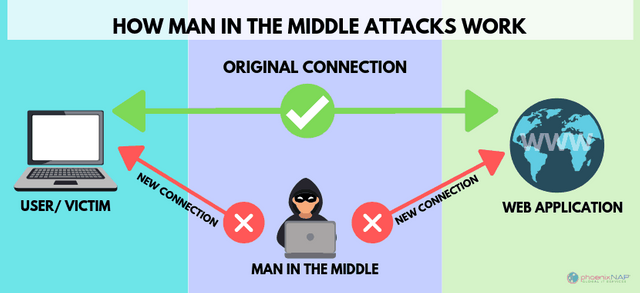
Man in The Middle
This type of hacking is not very likely to occur but there is a change that it may happen. In this kind of hacking a hacker can put himself a man in the middle
it means that the hacker put himself between you and the internet you are browsing. by this technique, the hacker can see your data and even modify it before sending it to the providers. By as I said it happens very rarely.
That's all for today. This post was just to spread awareness among steemit users. As all of using the internet the whole day so it is very important to keep knowledge about this kind of treats