Hacked at home. Why is my computer infected? ~TnkSecurity
Welcome back as this is another guide meant to keep you safe from online attacks. In today's lesson we will go over how to understand if a site is trustworthy, if it matters and how you can get viruses or lose data. Then we will talk about how those viruses affect your computer. Last time we talked how you can lose data when in public networks. Today is about losing data when you are in the safety of your home. This is really important as people keep accepting attacks and don't know how to defend themselves. The keyword here is "accept" because no one can just attack you and take your data without your permission. Forget what you see in movies, all of that is fake of course. The only series that has taken a more realistic way of showing how hacking works is Mr.Robot which I highly recommend for its great plot and acting.
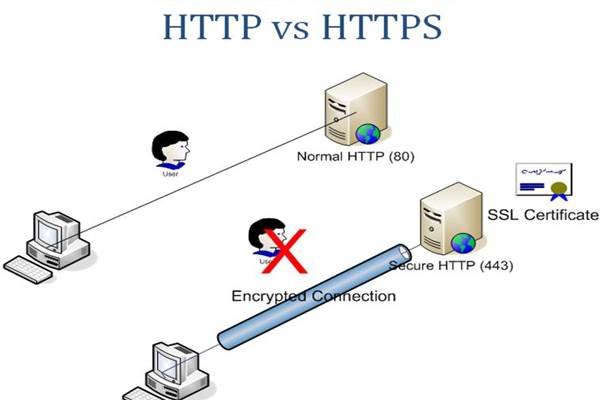
- Http VS Https
Now what does it mean to be trustworthy. In this day and era, every website, almost, requires you to register. Then you may manage "private" actions. Private should always be escorted by quotes for nothing is actually private. Anything you do in a website, will be sent to the website. The nudes you sent to your boyfriend/girlfriend are in fact in an archive in Facebook. So no, your conversations are not completely private. What really matters is for them to be encrypted. The 's' after http means secure. A website sends you packages and you send it packages back. Those packages contain your password and messages. If a site doesn't have that 's' those messages travel to the websites server the way they are. That means anyone interfering with those packages, will be able to get your information. That is why whenever you are sending sensitive information, a.k.a your password, make sure the site is https. The difference is that these packages will now be encrypted thus unreadable to anyone but the server you are sending them to. Then again if you are not sending any information then it really doesn't matter if the site is https. For example the site I watch anime isn't, but since I am not registered and don't really send them packages, it doesn't really matter.
- Viruses
People are terrified when faced with the download button. Or even the redirect button. Well, fear not, I am here to clarify and guide you through downloading porn. Actually don't, you shouldn't download porn. Anyhow. Do not be afraid to visit sites. Though you CAN get infected by just visiting a site, if you don't visit random and non-certified sites, there won't be a problem. There are exploits where a site can have its virus be downloaded and executed without being detected and without permission but it is pretty hard to happen.
The biggest foes here are downloadables. Lot's of people just download stuff. It's sickening. Someone sends them a link, they just press it. They see a download link, they press it. They see they won a million dollars for visiting a site, by Cthulhu's blessings it must be true, they press it. Please stop. This is what I mean by accepting to get attacked. When you download a file and run it, it might have hidden code, which can create infestations on your device. If you run a file it might then lay eggs which will hatch and breed more, overflowing your device (worms), or might just take control of your device, or can simply send hidden messages to your crush and steal them away from you. Some of the simplest viruses are key loggers. You run a program, that program installs another program which will now run at start up, and that program logs every key you press, and then sends it to the attacker. This way an attacker can find your passwords if you don't have them saved. This is why you should always save your passwords, a virus might find these saved passwords but they will be encrypted. The only way for another person to get your saved passwords is if they take your computer physically. If this happens, not even God herself can stop them from taking everything.
A file, means any file. Videos, images, texts. Everything might contain viruses. However you need to RUN the file. If the malware is in an image, you will probably not activate it since you are simply viewing the image. Same goes for video and texts. The most dangerous extensions are EXE, BAT, PY, C, JAR, and any other executable. Word documents and other products like that can also be infected but can't be activated as long as you don't allow their macros to run. That is why now Microsoft asks you first before letting the documents run wild. So don't ever download any kind of executables unless it is from a unmistakably trusted source.
Also when installing things never take the express road, and never spam next. Always check what you are installing otherwise you will end up with your browsed hijacked, having yahoo as home page, unable to do anything against the evilness and desperation that has now taken over it.
- What if it's already infected
Tough luck. You can try and uninstall the last things shown in the Uninstall Programs but dates can be manipulated and you can never be truly sure. Even if you have a strong antivirus, if you let something in, it won't protect you. Best solution is a complete format, and make sure to change all your passwords from a clean device while your infected device is being reinstalled.
Your biggest enemy is ignorance. Always check the website's address and make sure to press the correct download buttons. Don't listen to ads, you didn't win money, and make sure not to fall victim to scams. Simply, don't be a fool. As for the hackers that can hack systems without having someone download anything, well, you can't do anything about that so no sense in worrying. Once again, I am Tsinik and I hope this helped you understand a bit better how hacking works and how you can protect your self. Until next time, goodbye.

Don't open suspicious emails attachments. It's as simple as that. I've seen it many times. People then calling me wanting my computer support later on ;-)
J
emails dont even allow executables anymore and people still find ways to get infected from them :P
They see they won a million dollars for visiting a site, by Cthulhu's blessings it must be true, they press it.:D:D so true man, so true
Cthulhu commands it! :D