4G LTE Loopholes Invite Unwanted Phone And Location Tracking, Fake Emergency Alerts
Now listen to Fossbytes stories!
In a new paper, the researchers at Purdue University and the University of Iowa have discovered vulnerabilities in three procedures of the LTE protocol.
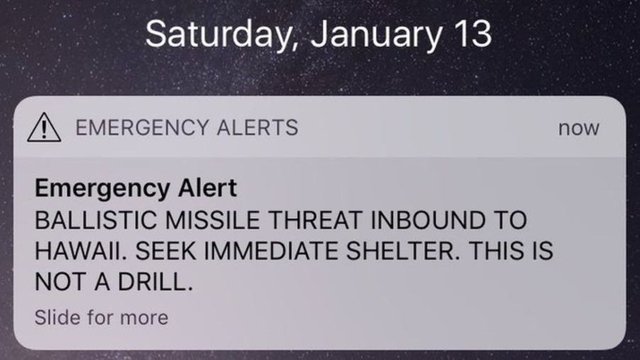
The loopholes could be exploited to launch 10 new attacks, such as location tracking, intercepting calls and texts, making devices offline, etc. With the help of authentication relay attacks, an evil mind can connect to a network without credentials and impersonate a user. A situation of an artificial emergency can be created by issuing fake threat alerts, similar to the recent missile launch alerts in Hawai.
The threat to LTE isn’t some theoretical concept confined to a research paper. The researchers have tested the flaws in the real world on four leading carrier networks in the US; one of them has already fixed their network. They have developed a testing tool called LTEInspector which can be used to detect the vulnerabilities in LTE networks.
For a person with a required know-how and apparatus, making an attack solution is just a matter of spending around $1,300.
While it’s claimed that the attacks are working, the researchers won’t be releasing any proof-of-concept until the LTE vulnerabilities get fixed.
It may be possible to work out fixed without much pain, but stress should be given on finding any existing bugs in protocols before they are deployed in the real world. On the other hand, 5G is just around the corner. It will be faster and considered more secure than the existing telecommunication technology.
We could witness first 5G networks by next year. But this doesn’t mean it would be the end of 4G right away. The technology is yet to reach many people around the globe.
Source via ZDNet