The Cyber-Security Training Tips Your Business Has Been Looking For
Entirely Enforce a Multi-Tiered IT Security Plan for ALL Staff
As new dangers emerge, it is basic to stay up with the latest to ensure your business. Your representative handbook needs to incorporate a multi-layered IT security design made up of approaches for which all staff, including officials, administration and even the IT office are considered responsible.
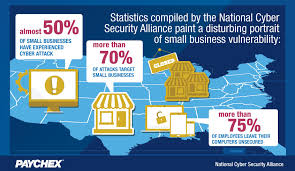
Image source
Satisfactory Use Policy - Specifically demonstrate what is allowed versus what is restricted to shield the corporate frameworks from pointless introduction to hazard. Incorporate assets, for example, inner and outer email utilize, web-based social networking, web perusing (counting satisfactory programs and sites), PC frameworks, and downloads (regardless of whether from an online source or blaze drive). This strategy ought to be recognized by each worker with a mark to mean they comprehend the desires put forward in the approach.
Secret Data Policy - Identifies cases of information your business considers private and how the data ought to be dealt with. This data is frequently the sort of documents which ought to be routinely moved down and are the objective for some cybercriminal exercises.
Email Policy - E-mail can be a helpful technique for passing on data however the composed record of correspondence likewise is a wellspring of obligation should it enter the wrong hands. Having an email arrangement makes a steady rules for all sent and got messages and reconciliations which might be utilized to get to the organization arrange.
BYOD/Telecommuting Policy - The Bring Your Own Device (BYOD) strategy covers cell phones and additionally organize get to used to associate with organization information remotely. While virtualization can be an extraordinary thought for some organizations, it is pivotal for staff to comprehend the dangers advanced mobile phones and unsecured WiFi display.
Remote Network and Guest Access Policy - Any entrance to the system not made specifically by your IT group ought to take after strict rules to control known dangers. At the point when visitors visit your business, you might need to tighten their entrance to outbound web utilize just for instance and add other safety efforts to anybody getting to the organization's system remotely.
Episode Response Policy - Formalize the procedure the representative would follow on account of a digital occurrence. Consider situations, for example, a lost or stolen portable PC, a malware assault or the representative falling for a phishing plan and giving secret subtle elements to an unapproved beneficiary. The speedier your IT group is informed of such occasions, the snappier their reaction time can be to ensure the security of your private resources.
System Security Policy - Protecting the trustworthiness of the corporate system is a fundamental bit of the IT security design. Have an approach set up indicating specialized rules to secure the system foundation including techniques to introduce, benefit, keep up and supplant all on location hardware. Furthermore, this strategy may incorporate procedures around secret key creation and capacity, security testing, cloud reinforcements, and organized equipment.
Leaving Staff Procedures - Create guidelines to repudiate access to all sites, contacts, email, secure building doorways and other corporate association focuses instantly upon acquiescence or end of a worker notwithstanding regardless of whether you trust they old any pernicious plan towards the organization.
Worker digital security mindfulness preparing significantly decreases the danger of falling prey to a phishing email, grabbing a type of malware or ransomware that locks up access to your basic records, spill data by means of an information rupture and a developing number of malignant digital dangers that are released every day.
Untrained representatives are the best danger to your information security design. Preparing once won't be sufficient to change the hazardous propensities they have grabbed throughout the years. Consistent discussions need to occur to guarantee collaboration to effectively search for the notice indications of suspicious connections and messages and additionally how to deal with recently creating circumstances as they happen. Steady updates about the most recent dangers and implementation of your IT security design makes singular duty and trust in how to deal with occurrences to restrict introduction to an assault.
Make standard chances to share topical news about information ruptures and investigate distinctive cyberattack techniques amid a lunch and learn. Once in a while the most ideal approach to build consistence is to hit near and dear by making preparing individual. Odds are your workers are similarly as ignorant about their own IT security and basic tricks as they are about the security dangers they stance to your business.
Develop this thought by stretching out an encouragement to instruct their whole families about how to shield themselves from cybercrime amid a nightfall occasion. Consider covering subjects to such an extent that may interest a scope of age gatherings, for example, how to control the protection and security settings via web-based networking media, web based gaming, and so forth and how to perceive the threat indications of somebody phishing for individual data or cash both by means of email and telephone calls. Seniors and youthful kids are particularly helpless against such abuse.
Try not to Make a Hard Situation Harder; Remember you WANT warnings announced
Making continuous security preparing a need will incredibly decrease rehash blunders and avert numerous avoidable assaults, however botches happen. It can be exceptionally humiliating and a stun to ones pride to recognize their mistake and report association in a potential security break. Your first nature might be to revile and shout, yet this would be a genuine mix-up. Resisting the urge to panic and gathered is the way to the trust required for representatives to come to you immediately, while they are feeling their generally powerless.
Consequently, treat each report with thankfulness and quick mindfulness. Regardless of whether the ready ends up being a false alert or a genuine emergency, abstain from castigating the representative for their slip-up regardless of how red your face may progress toward becoming.
At the point when circumstance is under control, accept an open door to express gratitude toward them for detailing the circumstance with the goal that it can be dealt with fittingly. Keep in mind it takes a great deal of strength to venture up when you know you were to be faulted. Enable the worker to comprehend what to pay special mind to next time is it was something that could have been anticipated, for example, a client blunder.
Digital Training Recap
Actualize a Multi-Tiered IT Security Plan Strictly Enforced for ALL Staff
Preparing isn't a One Time Thing;
Keep the Conversation Going
Preparing Should Be Both Useful Personal AND Professional to Stick
Try not to Make a Hard Situation Harder; Remember you WANT warnings revealed
good..
love the way of cyber security..
Cyber security is very important by online. so everybody learn about cyber crime