US Army and NSA are able to unmask Tor, I2P, VPNs
The image of a memo leaked online suggests US Army and NSA are able to unmask Tor, I2P, VPNs users and they are working to track Monero,
US Army and NSA are able to unmask Tor, I2P, VPNs users and they are working to track Monero, this is the truth revealed by a photo alleged leaked by US Army.
The image revealed a joint project to track anonymous cryptocurrencies conducted by US Army’s Cyber Protection Team (CPT) from the Cyber Protection Brigade and NSA.
The photo of the memo is dated August 21, 2017, and was posted in the biz section of 4chan. The content reads:
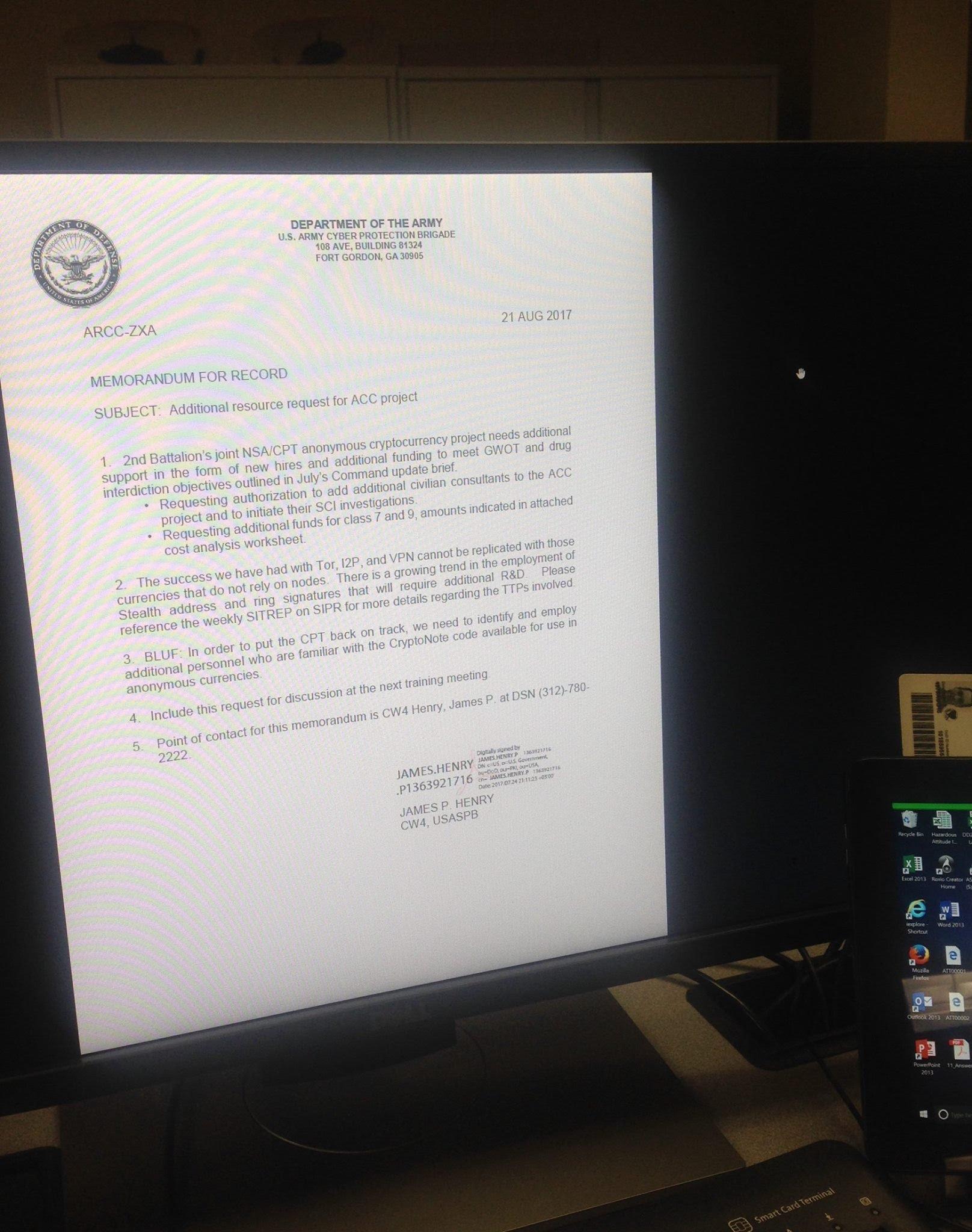
“MEMORANDUM FOR RECORD
SUBJECT: Additional resource request for ACC project
2nd Battalion’s joint NSA/CPT [Cyber Protection Team] anonymous cryptocurrency project needs additional support in the form of new hires and additional funding to meet GWOT [Global War On Terror] and drug interdiction objectives outlined in July’s Command update brief.
• Requesting authorization to add additional civilian consultants to the ACC project and to initiate their SCI investigations
• Requesting additional funds for class 7 and 9, amounts indicated in attached cost analysis worksheet.
The success we have had with Tor, I2P, and VPN cannot be replicated with those currencies that do not rely on nodes [?]. There is a growing trend in the employment of Stealth address and ring signatures that will require additional R&D. Please reference the weekly SITREP [SITuation REPort] ON SIPR for more details regarding the TTPs involved.
BLUF [Bottom Line, Up Front]: In order to put the CPT back on track, we need to identify and employ additional personnel who are familiar with the CryptoNote code available for use in anonymous currencies.
Include this request for discussion at the next training meeting.
Point of contact for this memorandum is CW4 Henry, James P. at DSN (312)-780-2222.
JAMES,HENRY
.P1363921716
JAMES P. HENRY
CW4, USASPB”
NSA US army unmask Monero Tor I2P VPN
The memo explicitly refers to the difficulties in unmasking cryptocurrencies that are based on the CryptoNote that is an application layer protocol implemented in the scheme of several decentralized privacy oriented digital currencies.
The document requests the allocation of additional resources to track anonymous cryptocurrencies like Monero (XMR), Anonymous Electronic Online CoiN (AEON), DarkNet Coin (DNC), Fantomcoin (FCN), and Bytecoin (BCN).
The US authorities believe that Monero would become the main cryptocurrency in the criminal underground.
Researchers at DeepDotWeb verified the authenticity of Defense Switched Network (DSN) phone number listed for James P. Henry
“There is a Defense Switched Network (DSN) phone number listed for James P. Henry. When this DSN phone number was converted into a phone number that can be reached from the regular commercial phone network and called, the number was in fact the US Army’s Cyber Protection Brigade located in Fort Gordon, Georgia, just as the document purported to originate from.” states the blog post published by DeepDotWeb.
“While it is possible someone could have done a search for the Cyber Protection Brigade telephone number and used the conversion chart to recreate the DSN version of the phone number, it should be noted that the DSN phone number was not published on the internet prior to the release of this leak.”
DeepDotWeb requested comments from a Monero developer and others sources who were formerly in the Army, they all confirmed that the document appears to be authentic and its content plausible.
DeepDotWeb cited an anonymous source who is still serving in the US Army, that after analyzed the document said it was accurate.
Security experts believe that the US intelligence and military are using internal resources to conduct surveillance on blockchains.
It is still unclear who leaked the memo, someone speculates it was intentionally published with a deterrence purpose.
Tor, I2P, and VPNs are not completely compromised by the intelligence agency, persistent attackers have already proposed and implemented techniques to unmask users but that are not effective for dragnet surveillance.
Documents leaked by Edward Snowden revealed that the NSA is able to unmask VPN solutions based on vulnerable VPN protocols such as the PPTP, however, VPNs which rely on OpenVPN may not be compromised.
Don’t forget that anonymizing networks are essential to fight censorship and to ensure freedom of speech.
Looking at the photo it is possible to note above the laptop’s monitor, in the bottom right of the photo, a Common Access Card (CAC) that is a smart ID card used by the Department of Defense.
I believe it was intentionally put there with a diversionary intent.
https://securityaffairs.co/wordpress/68684/digital-id/nsa-memo-anonymizing-systems.html
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
http://securityaffairs.co/wordpress/68684/digital-id/nsa-memo-anonymizing-systems.html
very interesting article, will dig a little bit more into it, thank you.
Thank you for checking it out.