Crypto Academy / Season 3 / Week 8 - Homework Post for professor @stream4u - Let's open the Cryptography
Hi everyone and Assalam U Alaikum,
Q. 1. Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms?
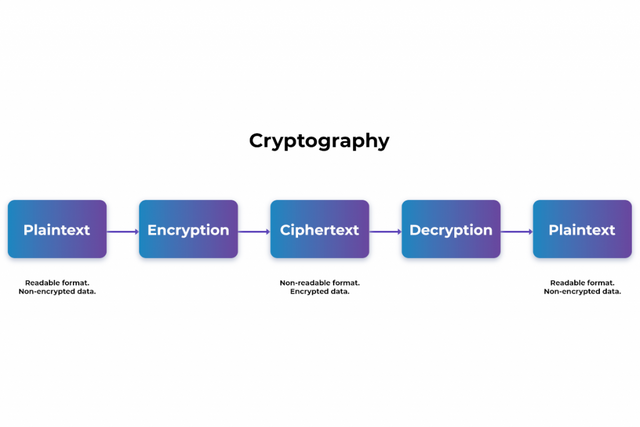
Blockchain is a digital ledger in which data of different transactions is saved on blocks. The saved data cannot be altered or changed afterwards. Once a block is saved, then a copy of the data is distributed among nodes on the entire network. While Cryptography is the technology through which communication between the individuals, in the presence of others, is made secure and hidden, if chosen. Only the targeted audience is able to view this secured communication.
Blockchain CryptoGraphy is a termed used for technology through which data on Blockchain is secured. There are two types of cryptographic algorithms that are used in the Blockchain which are Hash functions and Asymmetric-keys Hash consists of alphanumeric combinations that are used to contain large data of a transaction into a fixed-length that cannot be changed when data is saved into a block on the network. All the blocks on the network are connected with each other through Cryptographic Hash.
The other type of cryptographic algorithm that is Asymmetric keys deals with digital signature of the transactions. It involves the use of Private and Public keys that will be discussed in detail in the later part of the post. The privacy of the data is achieved on the Blockchain whereby a hidden message is encrypted by the sender and on the other end, it is decrypted by the targeted audience to see the hidden content of the message. This whole procedure involves the use of Private and Public keys.
Blockchain Platforms.
Below is the list of some of the Blockchain platforms that have been built using Blockchain Network technology.
• Ethereum
• EOSIO
• Stellar
• EOS
• Steem
• Fantom
• Neo

Q. 2. Explain the Public Key CryptoGraphy.
Public key is one of the products of Asymmetric-keys algorithms. It is an alphanumeric combination, and as the name refers, it is a key that is to be used as Public and it can be shared with others on the blockchain. Public key is used to create wallet address that can be used to receive funds. It is just like a bank account that can be shared with others. It is one of the pair of keys, that are Private key and Public key. Public key can be generated using Private key, while on the other hand, Private key cannot be generated using Public key.
When any data id encrypted and sent to the other individual, it can be decrypted by the receiver with the public key of the sender. On the other hand, when a transaction is digitally signed by the sender using Private key, before adding the transaction data to the block, public key of the sender is required for verification purpose.

Q. 3.Explain the Private Key CryptoGraphy.
As the name refers, this key is very private that belongs to the owner only. Cryptocurrency in the wallet can only be accessed using Private Key. This key cannot be shared with anyone.
Private key is one of the Asymmetric-keys algorithm and it consists of Alphanumeric combination of characters. The only owner can have this key as it is a secret key and should not be shared with anyone otherwise wallet will not be secure. This key is used to secure the assets in a wallet and also used to digitally sign the transaction.
Without Private key, an owner has not total control over his assets in the wallet. Private key is essentially required for total control of the owner. The other use of Private key is that when a transaction is created, Private key is required to sign the transaction digitally before broadcasting the transaction on the network.
Private key is generated on the creation of wallet and it should be kept very safe as the owner cannot have total control over his assets in the wallet without Private key.

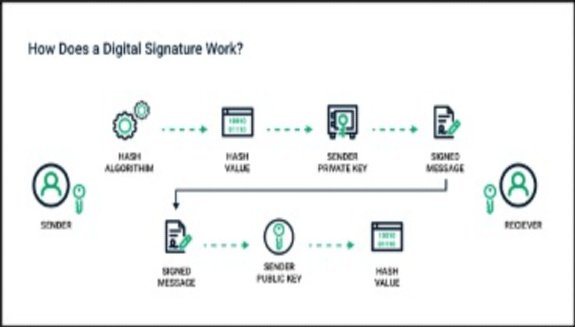
Q. 4. Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
In conventional banking system, when a transaction is made, the originator had to sign the document and then this signature is verified by the bank by matching the scanned signatures that are saved in the system of banks. Likewise, in digital world, before a transaction is broadcasted onto the network, digital signatures are required by the sender of the transaction.
Digital Signature Cryptography is yet another product of Asymmetric-keys algorithms in which use of Private key is essential for signing a transaction or message in order to broadcast it to the network. Private key is required to digitally sign the transaction and then this transaction is sent to the miners on the network for verification of transaction. These miners verify the validity of signatures by taking the Public key of the originator and then complete the transaction and save it in a block on the network.
Signing of Transaction.
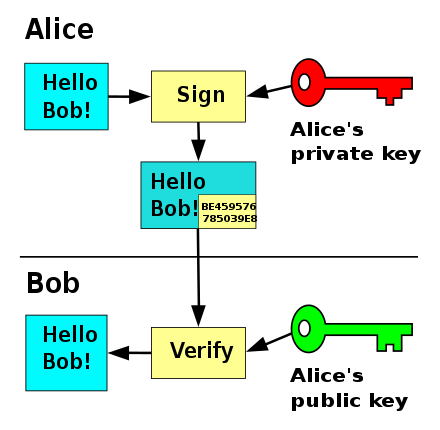
In digital world of cryptocurrency, signing of a transaction is carried out using Private key of the owner. A transaction is signed digitally whereby cryptographic signing of a transaction is done by attesting the transaction using Private key that is like password of an account/Debit or Credit Card. This digital signature certifies that the owner has attested the transaction.
In digital world, there are two steps involved from digitally signing the transaction to its completion. These are Signing and Verification that are discussed in detail below.
Signing.
When any user wants to make a transaction on the network, private key is required for signing the transaction and to broadcast it on the network, thus a user signs the transaction digitally using Cryptographic Asymmetric-keys algorithms.
Verification.
When a transaction has been digitally signed using Private key by the sender, then it is sent to the miners for validation purpose. These miners validate the authenticity of the transaction using the Public key of the sender. After the completion of validation process done by the miners, transaction is completed and then it is saved in a block on the network.
Private key is also used to sign the encrypted message by the sender and then the receiver will be able to decrypt the message using the Public key of the sender without exposing the message to others on the network.

Q. 5. Explain what is Symmetric and Asymmetric cryptography?
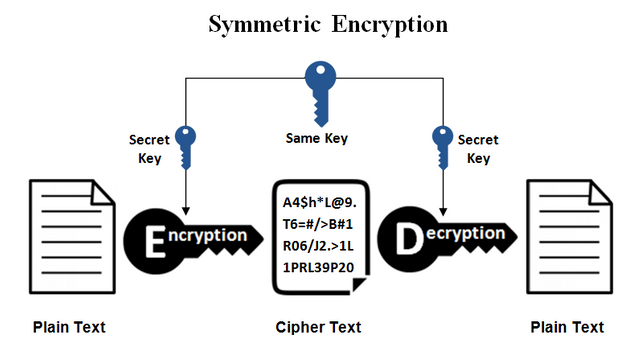
Symmetric Cryptography.
This type of Cryptography has been being used since long times which is called symmetric Cryptography where one key is used to encrypt and decrypt data. Parties involved in a transaction decide one key that is called Secret Key that is used by the sender at first. With the help of this, readable data form is changed to machine readable language called cipher text that cannot be read by and understood by human. Then the receiver decrypt the data using the same Secret Key and data is again in its original form that can easily be read by the receiver.
Symmetric Cryptography is very useful where two parties exchange confidential data regularly. Whereby exchanging bulk data is very easy as it is encrypted and decrypted very fastly using one secret key.
In Symmetric Cryptography, less computational power is required as it creates small size file that uses very small space thus making its transfer faster and reliable. On the other hand, if we look at its disadvantage, a large number of keys will be required in case of a Larger group and it is not easy to keep record of all of these keys.
Asymmetric Cryptography.
In Asymmetric Cryptography, two different keys are used to encrypt and decrypt the data. First, the data is encrypted by the sender using Private key where it is used for digital signature attached to the transaction. On the other end, the receiver has to decrypt the transaction data using the Public key of the sender that is used to validate the authenticity of the transaction.
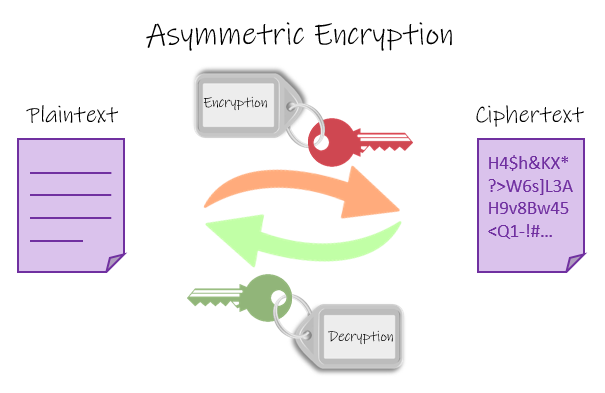
Asymmetric Cryptography is more secure as compared to the Symmetric Cryptography and to exchange data for lager group, less keys are required as compared to Symmetric Cryptography.
The only disadvantage, I can see in Asymmetric Cryptography, is that it is slower in bulk exchanging.

Q. 6. How Blockchain Wallets Cryptography works
Blockchain wallets or crypto wallets are softwares that are used to store and save crypto assets. Every crypto wallet has *Private Key, *Public key and a Wallet Address.
Wallet address serves like a bank account number in the real world which is a fixed length combination of numbers and letters generated cryptographically. Address of a wallet is unique and it will not match with any other wallet address.
Public Key of a wallet is used to receive funds into the wallet whereas identification of a wallet on the Blockchain is possible through Public key.
Private key is used to send the funds by making a transaction on the blockchain which is digitally signed using the private key of the owner. An owner has complete control over his wallet though Private key. Private key is very important and cannot be shared with anyone.
These Private and Public keys enable the user to have full control over his assets and he can use the funds without any problem using decentralized environment ad there is no authority that has control over the assets of user. User is the sole owner of his assets and has full control to use them wherever he wants.
Types of Wallets.
There are mainly two types of wallets Hot Wallets and Cold Wallets. These are discussed in detail below.
Hot Wallets.
These are the wallets that are connected to the internet. Software Wallets is the example of Hot wallets that are connected to the internet. Software wallets can further be classified into following sub-categories.
Mobile Wallets are wallets that can be installed on mobile phone and can be used easily anywhere through internet.
Desktop Wallets are the wallets that are downloaded and installed on Computers or laptops. These wallets can only be accessed on the device they are installed. These wallets are secure but in case, device is hacked, the assets in the wallet are at risk.
Online Wallets are the wallets that are opened with third party online where the keys of the wallet are stored online. These are cloud wallets where a third party hosts the cloud and these are very vulnerable to attacks. However these wallets are very easy to use and can be accessed anywhere on any device.
Some examples of Hot wallets are Exodus wallet, Trust Wallet, Metamask wallets etc.
Cold Wallets.
These are the wallets which are not connected to internet and are used offline. These are also called Offline Crypto Wallets that are not directly connected to internet. These can be USB type which are connected to the computer or any device to access the wallet. Transactions are made using internet but otherwise these wallets remain offline. That's why these are not vulnerable to online attacks and cannot be hacked easily.
Hardware Wallets are one of the Cold wallets and these are physical devices that are connected to computer or other device when needed and then unplugged after work is completed. In Hardware wallet, Private and Public keys of the wallet are kept offline thus making it less vulnerable to online attacks. Trezor Model T, Ledger Nano S are the examples of Hardware wallets.
Paper Wallets are another type of Cold wallets and these are in printed papers where keys of these wallets are kept offline thus making it less vulnerable to online attacks.
Hot wallets are considered more secure in case the user lost the password or any othe keys and these can be recovered on some cases. On the other hand, if the keys of Cold wallets are lost, then it is impossible to recover these keys and control of the wallet is lost.

Q. 7. What is the Merkle trees and What its importance in blockchain?
As we all know that data on blockchain is saved on blocks in Hash form that is a product of Cryptographic Hashing Function. The transaction details are kept in a fixed length of number and character combinations called Hash which makes the verification process of a block very easy. In case of numerous transactions, verification process may be very difficult to carry on and here comes the Merkle Tree to make this verification process easy.
Ralph Merkle introduced the concept of Merkle Tree in 1979 which was later adopted by blockchain. Merkle tree is used effectively for verification purpose that enables the computers to work very fast. It is a data structure that is used to store transaction data on blockchain more effectively and securely.
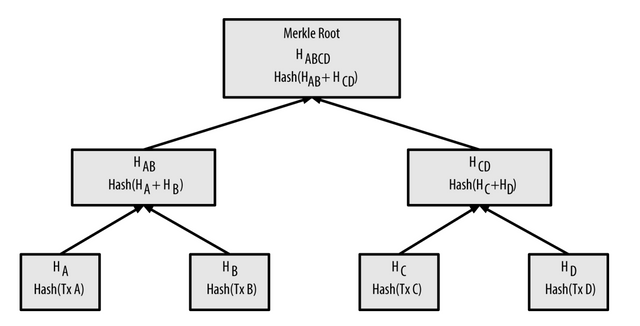
It is a structure of hashes relating to different blocks of data on the blockchain, arranged in such a way that it looks like a tree with roots, leafs and branches. Root hash is the hash of all hashes relating to transaction data on the block and this tree looks like upside-down shaped tree where root is on the top of the Merkle tree.
In the above image, it can be seen that Merkle tree has leaves hash of Trx A, Trx B, Trx C and Trx D which are Hash A, Hash B, Hash C and Hash D. Then there are branches that are made by pairing Leaves hash that will become Hash (A+B) and *Hash (C+D). Finally the root which is the hash of hashes and it will be *Hash (ABCD).
In case, where leaf nodes are odd in number, so what will happen. In this case pairing would be effected by this, so a duplicate of last transaction is made and paired with the original transaction.
Importance of Merkle Tree in Blockchain.
Merkle tree has proved to be very important in blockchain as it provides the process for verification of the data stored on a block. It also helps in reducing the space required to save the data on blockchain by summarizing all the data on a block in one hash. So here are some of the points that show the importance of Merkle Tree in blockchain.
Merkle tree is very effective in storing data on a block and securing the data by making it temper proof.
Merkle tree is also very effective in validation of data as too short time is required to verify the data by verifying the root hash.
Merkle tree helps in reducing the memory required for data storage and validation on a block.

Q. 8. Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
In this section of the post, I will do some practical work on Blockchain Demo developed by Anders Brownworth as per required in homework task.
Keys.
As we all know that in asymmetric cryptography, two keys are used which are Private key and Public key and these are alphanumeric combinations. These are linked to each other in such a way that a Private key of the wallet has a unique Public key and every wallet has different keys.
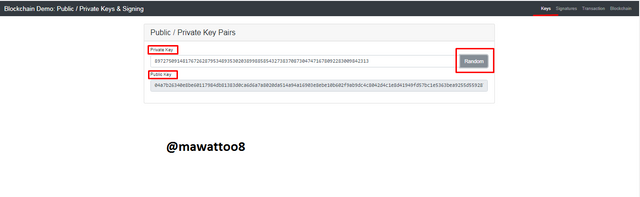
In this screenshot above which is the landing page of website under Keys tab, you can see there are two keys. Private key and Public key that are connected to each other. Details of the these keys are given below.
Private Key:
89727509148176726287953489353020389988585432738370873047471678092283009842313
Public Key:
04a7b26340e8be60117984db81383d0ca6d6a7a8020da514a94a16903e8ebe10b602f9ab9dc4c8042d4c1e8d41949fd57bc1e5363bea9255d559287f8bbba74e9d
As I have said that Private/Public Keys are unique so I will try to change Private key by clicking on Random and see what happens.
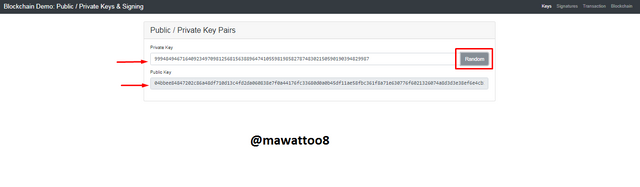
Now you can see that by clicking on Random, Private key has changes and Public Key has also changed because every Private key has a unique Public key. Details of new keys are given below.
Private Key:
99948494671640923497098125681563889647410559819858278748302150590190394829987
Public Key:
04bbee84847202c86a48df710d13c4fd2da060838e7f0a44176fc33680d0a0b45df11ae58fbc361f8a71e630776f6021326074a8d3d3e38ef6e4cb3bde23fca71d
From above two examples, we can see that every Private key has Unique Public key. Now I will try another change in Private key and use a very few numbers and find the unique Public key for that.
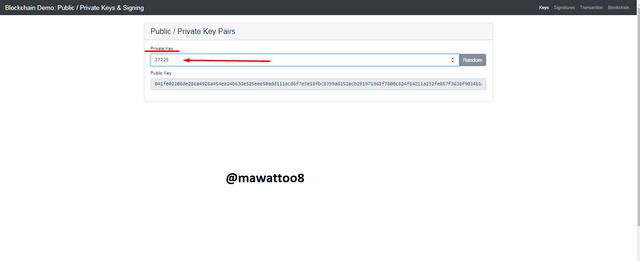
Private Key:
27225
Public Key:
041fe02208de286a4926a454ea24b63de525eee50add111acd6f7e3e18fbc8399a6152acb291971962f7800c824f64211a232fe857f3638f9034b1d342e872d252
In the above screenshot and details given above, you can see that I have changed the Private key and Public key has also changed which proves that every Private key has its own unique Public key.
Signature.
As we discussed in the earlier part of the post that Private Key is used to sign a transaction or message that creates the digital signature and the miners use Public Key to validate the authenticity of the transaction. Then after verification of the transaction, it is added to the block.
Now we will take a look at Signatures section of the website and do some practical work.
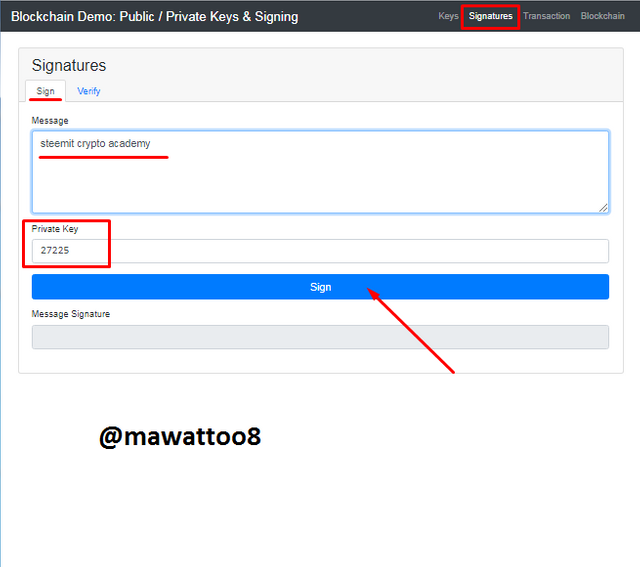
In the above screenshot, under Signatures section, there is a tab of Sign and I inputted my message that is "steemit crypto academy" and my Private key has already been added below. Now I will have to click on Sign and proceed.
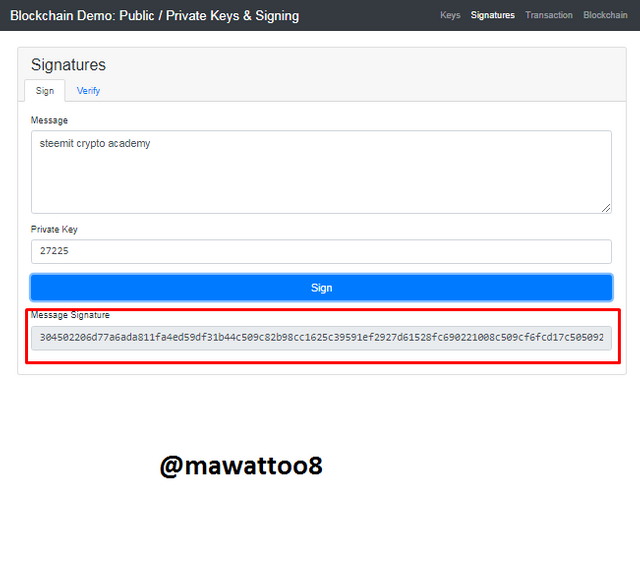
In this above screenshot, you can see that by clicking on Sign, Message Signature has been created which is given below.
304502206d77a6ada811fa4ed59df31b44c509c82b98cc1625c39591ef2927d61528fc690221008c509cf6fcd17c505092a54c1c5b31604f35187051d14757ac1726f7f81bc701
Now we will move to the next tab that is Verify and I will act as miner to validate the transaction through authenticating the valid digital signature made using Private key.
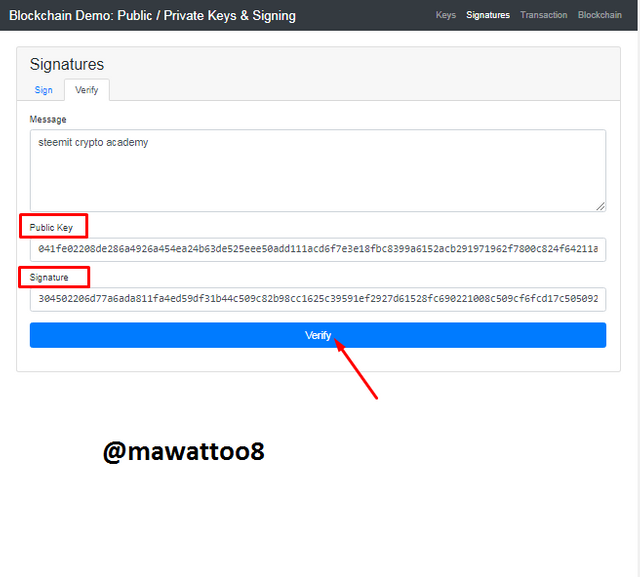
In this above screenshot, you can see that on verify tab, with my message, Public key of 27225 private key has been shared with miner and message signature has also been added, Now I will have to click on Verify to proceed further.
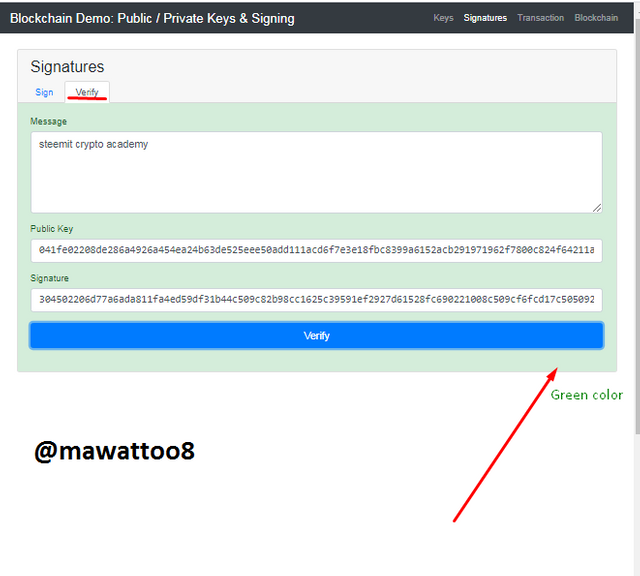
When I clicked on Verify, the color of the box has turned green that shows the verification has been done and its authenticity has been proved. It means that digital signature that was done using Private key are valid and it has been validated using Public key.
Transaction.
As we have used Sign and Verify tabs for signing with Private key and then Verifying with the Public Key, so for Transaction section, we will use Sing and Verify again.
To Sign a transaction, I have added $30 as the amount to be sent. My Private Key and Public Key has already been added. Receivers Public key is also added. Click on Sign and proceed.
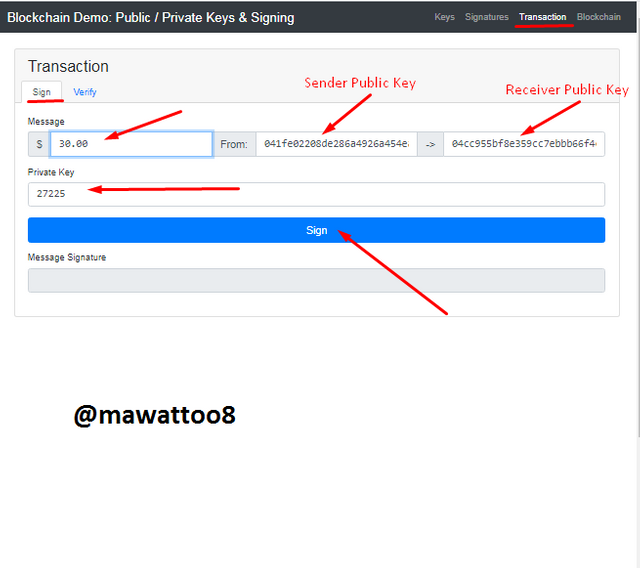
After clicking on Sign, the Message Signature has been created which is given below.
304402200d9868f2fb36c534da9463229b588ff38d26c405835647ecd24c204376fa59ed02205c55b175f60e534ab74a7c0772c6bce9fe2276334806fd543e4d74a4c8e214ed
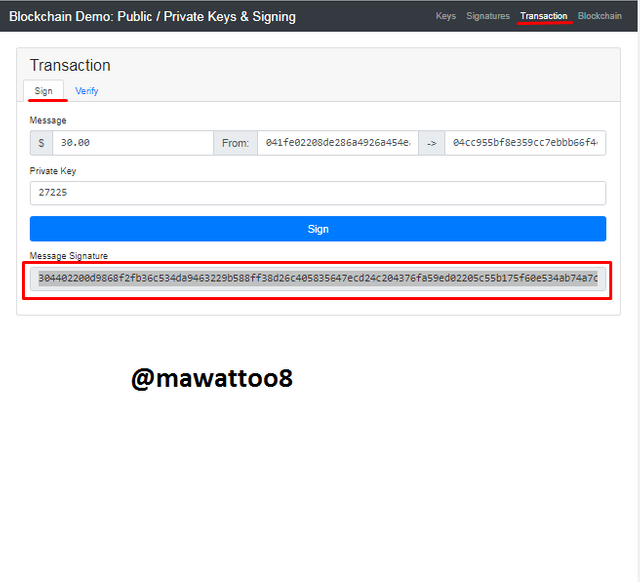
After transaction has been digitally signed, it is time to Verify the transaction before it is added to the block. I switched to Verify tab.
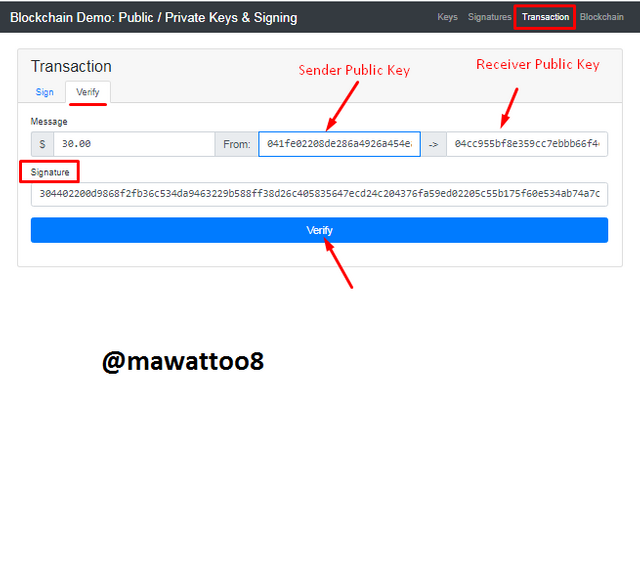
In the above screenshot, on Verify tab, Sender Public key and Receiver Key has been added and signature has already been supplied. Now, by clicking on Verify, we can proceed.
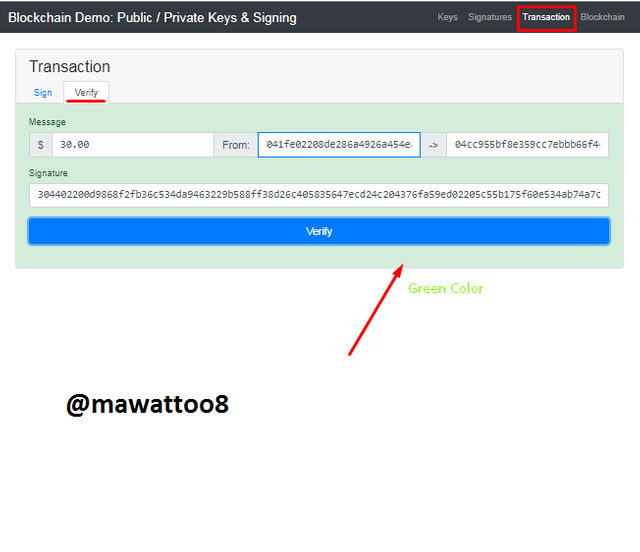
It can be seen in the above screenshot that its color has turned green which shows that the transaction is valid and digital signatures made using Private key are authentic.
Blockchain.
In this section of homework post, we will look how the transaction is stored in blocks with valid hash that is generated using Hash function of cryptographic component.
Now we will switch to Blockchain section and proceed.
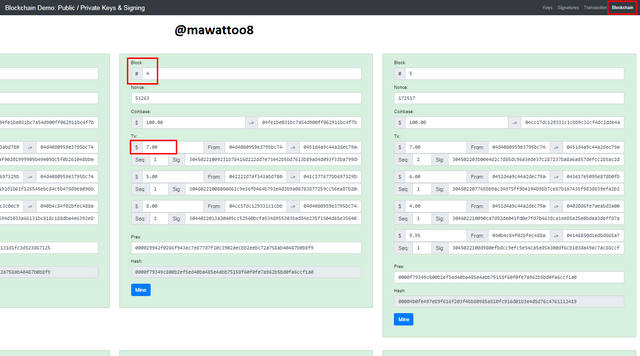
In the above screenshot, these are all valid blocks that have been added after verification by the miners which contain transaction details and valid Hash. Now I will try to alter the value of Block 4 which is 7 and I will change it to 30. We will look what happens there.

This screenshot is of Valid block and after altering the value of 7 to 30, the following change will happen.
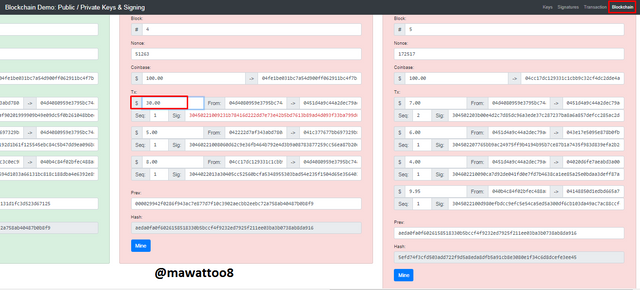
As soon as I changed the value of Tx, block color has changed to red that shows the invalidity of block and it needs to be re-mined. Block 5 has also turned red because hash value of Block 4 is not valid and it has been added in the Prev of Block 5 which is not accurate hash, that's why Block 5 is also Red now.
We will have Mine Block 4 and 5 to get correct Nonce and Hash so that it can be a valid block. Now I will click on MIne to make it a valid block. Both blocks need to Mined again.
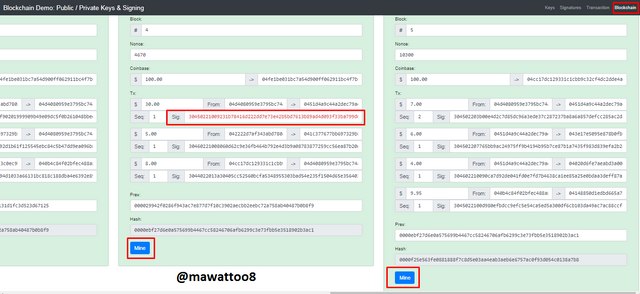
As soon As I click on Mine the Nonce of the block has changed and it has turned to Green which shows the validity of the blocks. Sig are the signatures of transaction in Block 4 that are still red because the initial amount of transaction has changed and there is a difference in the transaction and it cannot be validated using Public key. Block 5 is also a valid block because I have Mined it again to get the correct Nonce and previous hash of Block 4.
It shows that a change in any block will effect all the blocks after that block and invalid transactions are detected.

Conclusion.
In this lecture, we have learned many new things about Cryptography. It has a very important rule in effective data storage and its security. **Private and Public Keys are also very important that are connected to each other and they have also important rule in securing the transactions. These keys are components of Asymmetric-keys Algorithm that play their rule in account security, transaction signing and verification of digital signatures.
We also learned about Hashing functions that are used to create Hash, fixed-length alphanumeric combinations, that is very useful in storing data effectively in the blocks on the Blockchain. The data stored in the blocks cannot be changed afterwards.
Thanks in anticipation.