Steemit Crypto Academy, Season 3: Week 2 Homework || Hash and Cryptography.
In this post I will be submitting my homework task for professor @pelon53.


Question 1:- Explain what does the resistance to Collision mean and what does the resistance to Preimage mean?

Collision resistance

Collision resistance is a property of hash technology that is used in all the hash functions and this property ensures that it is nearly impossible or very hard to find inputs for a hash that is producing the same output.
Why did a hash produce the same output for different inputs?
As per the pigeonhole principle, when the number of inputs is larger than the number of outputs for a hash function, this leads to the property of resistance to collision and these resistance collisions will appear, where the security of a hash function is determined by the difficulty level of finding the Inputs for the same output.
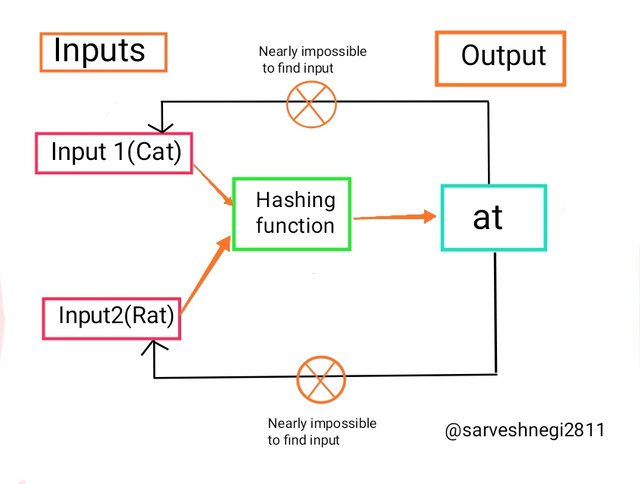
Let us take an example of the resistance of collision:
In tis example
Input 1 is Cat and the corresponding output to the input 1 is "at".
Input 2 is Rat and the corresponding output to the input 2 is "at" too.
So for different inputs we are getting a same input but it is nearly impossible to find input for that hash function.


Collision attack
Collison attack is an attack on resistance to collisions property of hash technology, this attack tries to find the inputs for the same output.
Collision resistant property has become a necessity in hash technology to secure the data or information.
Preimage resistance
Preimage resistance is another property of hash technology used for securing data and information and this property ensures that it is nearly impossible or very hard to find the input from its corresponding output, this shows the irreversible property of hashes.
Why it is difficult to trace or find the input from the corresponding output?
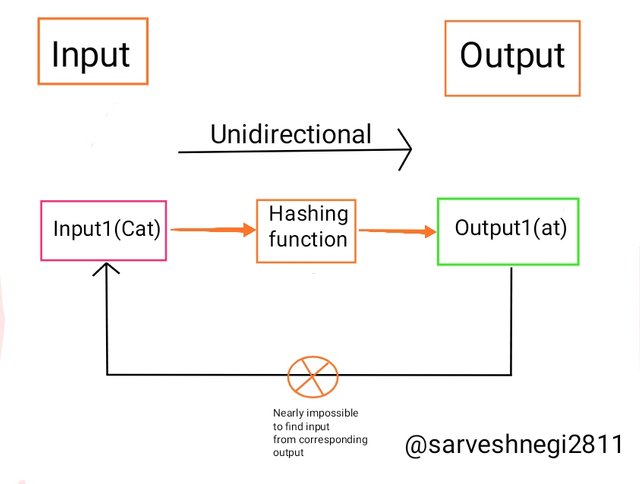
Diffie and Hellman proposed the idea of the one-way hash function, which means we can only produce output for input but we can't produce the input back from the corresponding output, in other words, it is unidirectional and can't be reversed.
Preimage resistance is of two types:
(1) First preimage resistance: In this property of hash technology, it is nearly impossible or very hard to find the input from its corresponding output.
Example of the First preimage resistance:


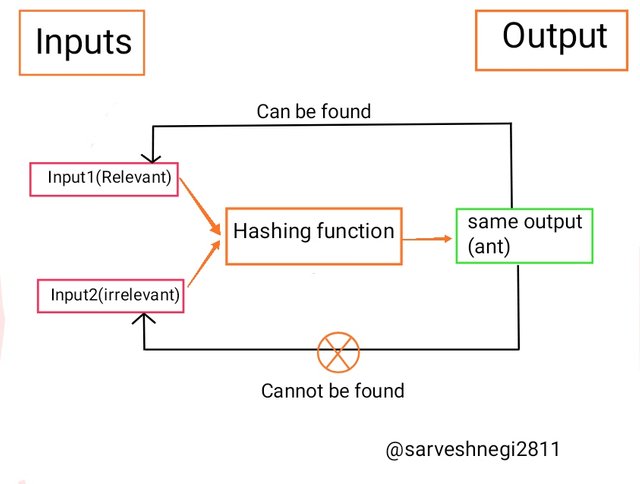
(2) Second preimage resistance: As we talked about the different inputs for a single output earlier in collision resistance, the second preimage resistance is the property of the hash function that ensures that it is nearly impossible or very hard to find the second input(which is not necessary or irrelevant or confidential) that has the same output as the first input(which is not confidential and can be seen by anyone).
Example of the second preimage resistance:



Question 2:- Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshots is required for checking.

Steps for using tronscan to verify the hash of last block and the hash of last transaction.

(1) I went to the Tronscan website and could see all the blocks and transactions .
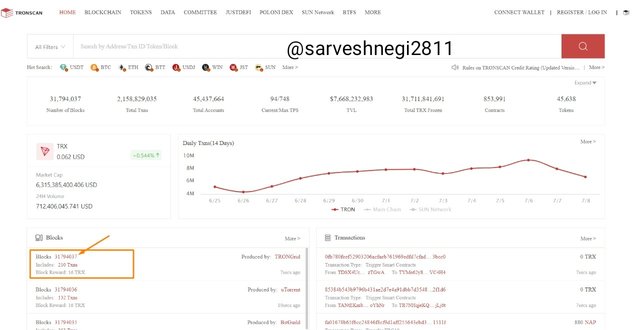
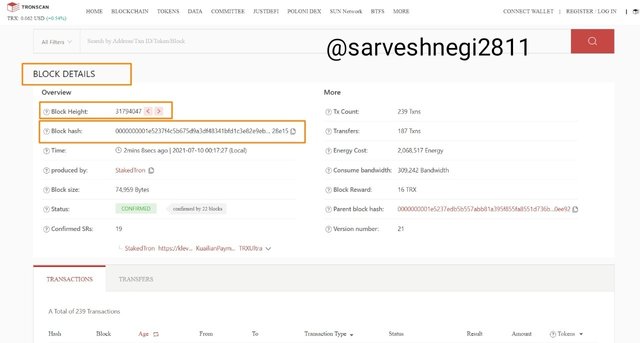
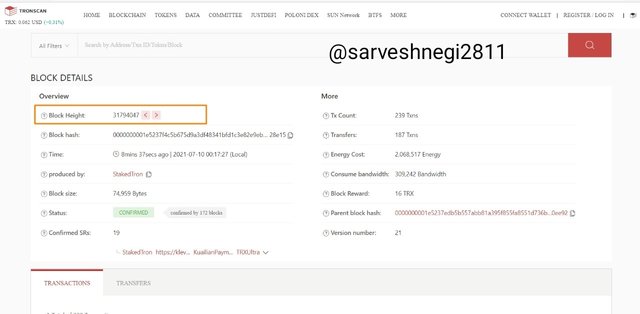
(2) Then I clicked on the latest block and could see the details like block height, block hash and transactions.
Block height: 31794047
Block hash: 0000000001e5237f4c5b675d9a3df48341bfd1c3e82e9ebd9a609dceec228e15
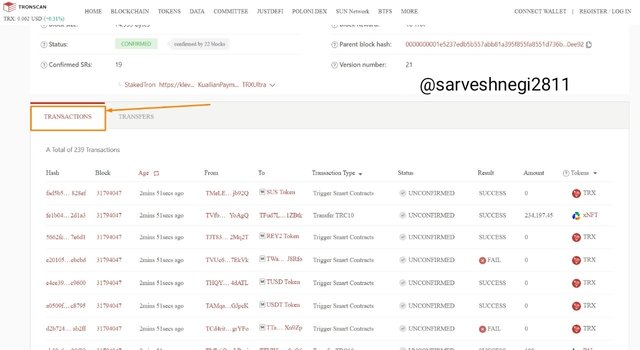
(3) Then I clicked on transactions and chose a transaction.
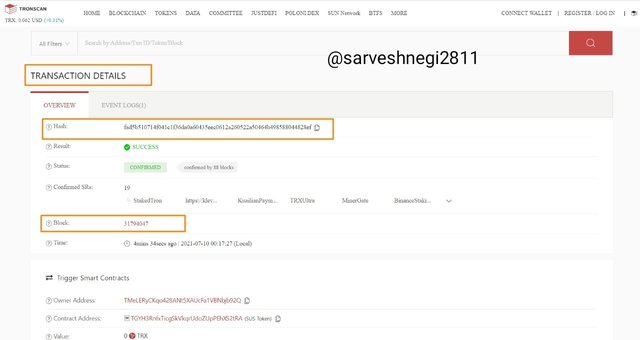
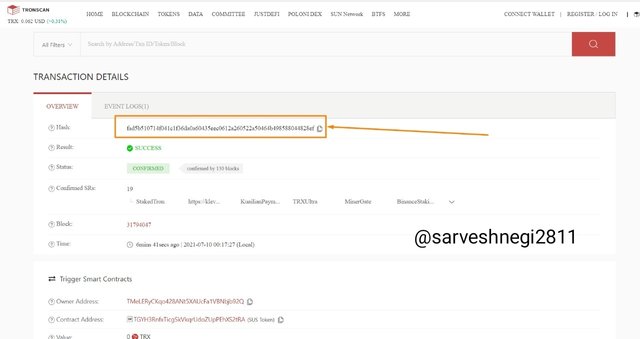
(4) Transaction details appeared along with the hash of transaction and block height.
Transaction Hash: fad5b510714f041c1f36da0a60435eec0612a260522a50464b498588044828ef
(5) Then I copied hash of transaction and searched for the transaction.
Hash code of transaction:(fad5b510714f041c1f36da0a60435eec0612a260522a50464b498588044828ef)
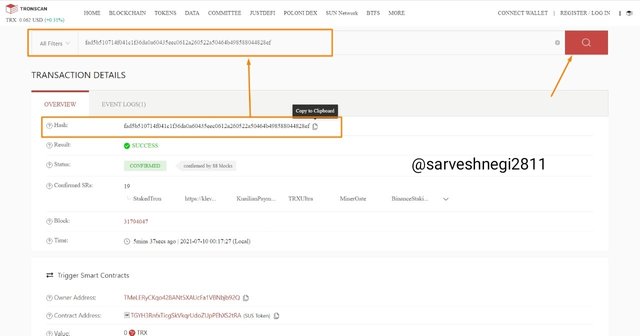
(6) You can see the transaction has been verified as I searched for it and get same transaction details as before.
Transaction Hash: fad5b510714f041c1f36da0a60435eec0612a260522a50464b498588044828ef
(7) Then I copied the block height from the transaction details and searched for it in the search section.
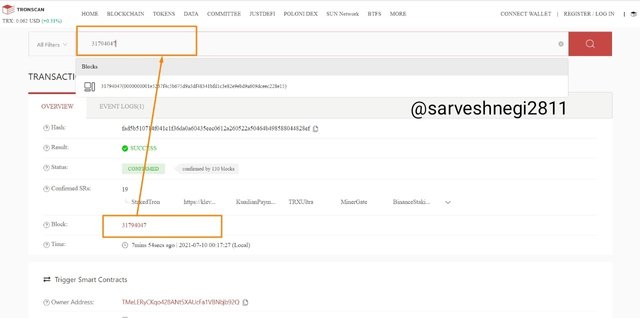
(8) Same block appeared from before in which we saw the details and transactions.
Block height: 31794047
Block hash: 0000000001e5237f4c5b675d9a3df48341bfd1c3e82e9ebd9a609dceec228e15

Using etherscan to verify the hash of block and transaction.
Steps for using etherscan to verify the hash of last block and the hash of last transaction.

(1) I opened Etherscan and could see latest blocks and transactions.
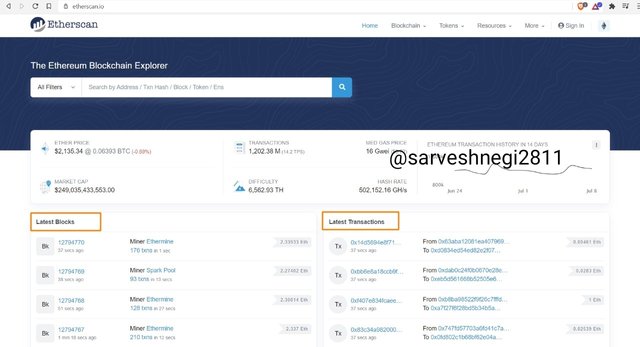
(2) Then I chose the latest block to explore.
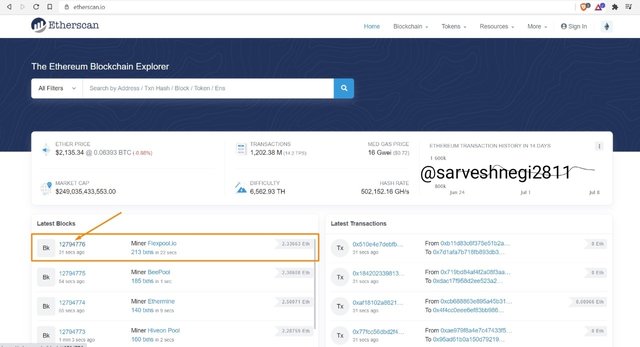
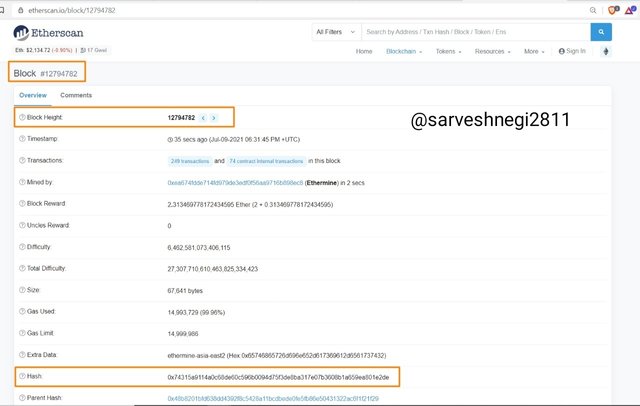
(3) All the details of that particular block appeared including block height, block hash and transactions.
Block hash:
0x74315a9114a0c68de60c596b0094d75f3de8ba317e07b3608b1a659ea801e2de
Block height: 12794782
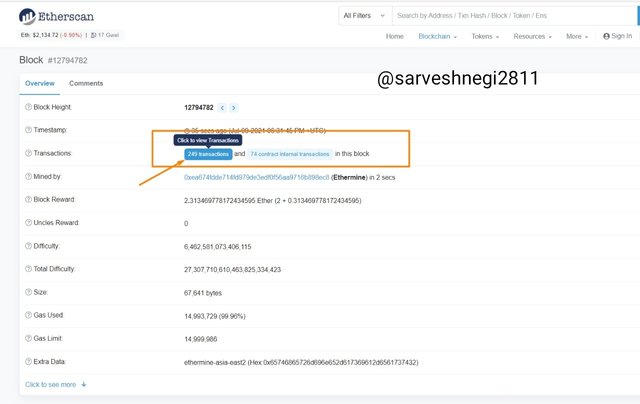
(4) Then it was showing 249 transactions, I clicked on transactions to verify transactions.
(5) I chose the latest transaction to verify so I clicked on it.
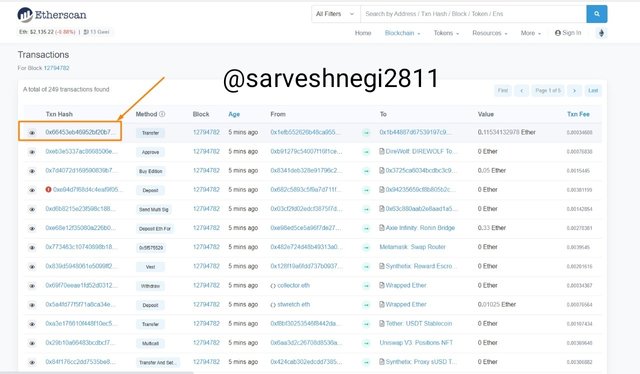
(6) Then transaction details appeared including transaction hash and block height.
Transaction hash: 0x66453eb46952bf20b786a8ba8d0183a88aef90cf801a3635cd9a512c64c09358
Block height: 12794782
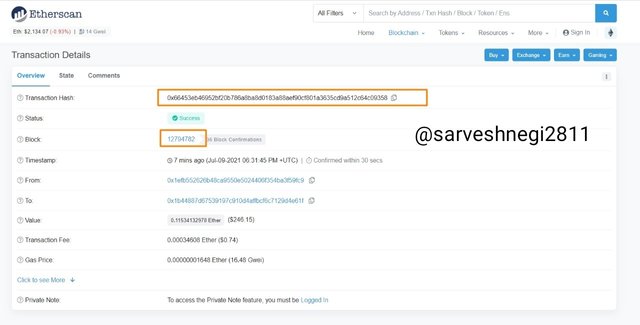
(7) I copied the transaction has to verify it in search bar.
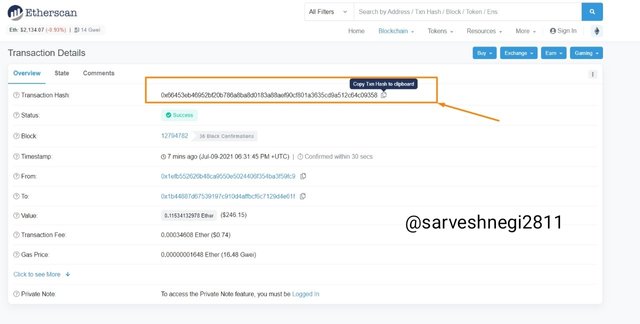
(8) I pasted or put the transaction hash in search bar to verify the transaction.
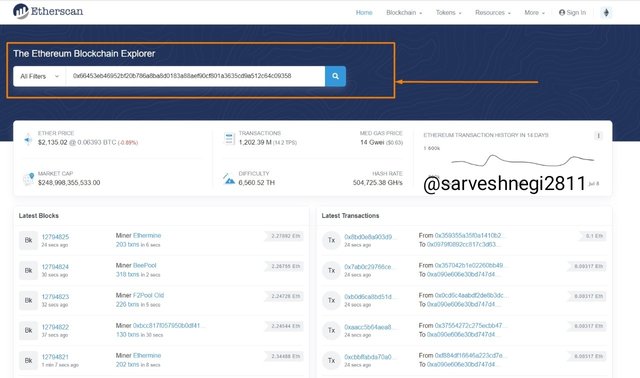
(9) Same transaction details appeared as before.
Transaction hash: 0x66453eb46952bf20b786a8ba8d0183a88aef90cf801a3635cd9a512c64c09358
Block height: 12794782
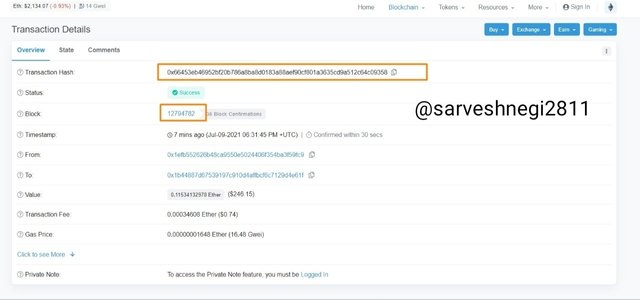

So I have verified the block hash and transaction hash for etherscan and Tronscan.

Question 3 : Generate a HASH using SHA-256, From the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.

(1) To generate a hash using SHA-256 for word
CryptoAcademy. Steps are as follow:
(a) I opened SHA-256 HASH GENERATOR.
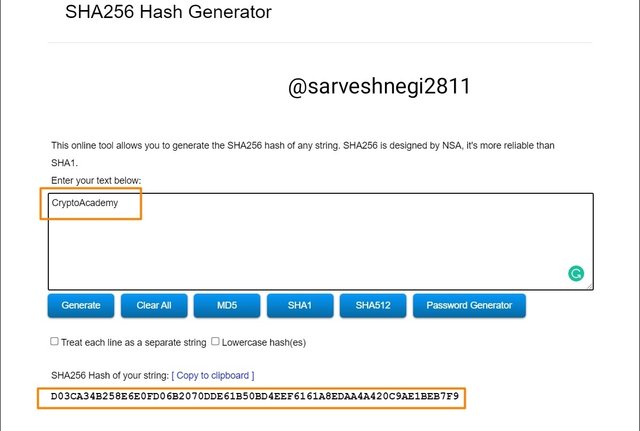
(b) Then I entered my text(CryptoAcademy) and SHA-256 hash generated.


(2) To generate a hash using SHA-256 for word
cryptoacademy. Steps are as follow:
(a) I opened SHA-256 HASH GENERATOR.
(b) Then I entered my text(cryptoacademy) and SHA-256 hash generated.


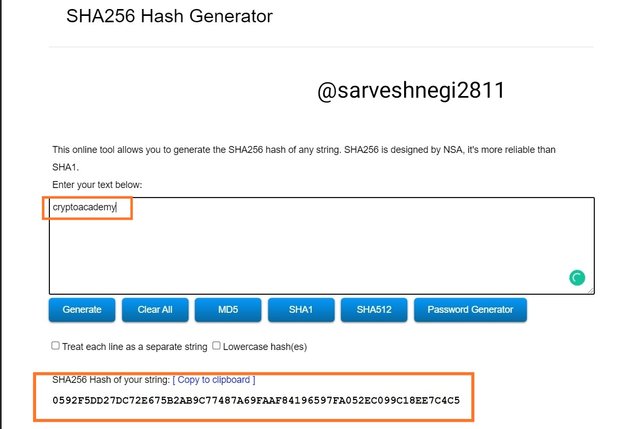

As you can clearly see the different hashes for the same word but with different uppercase and lower case letters.
CryptoAcademy has Uppercase letter C and A and that is why it generated
Hash: D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
cryptoacademy has all the letters in lower case and that is why it generated:
Hash: 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
Explanation for different hashes
The difference in the generated SHA256 hash is because of:
(1) Hashes are unique: As we all know that the hashes are unique and that means that there is only one hash for one input(except in some cases), so when we used CryptoAcademy, the hash generated based on the mixture of uppercase and lowercase letter not by the meaning of the word, same when we use cryptoacademy the hash generated based on all the lower case letter and that is the reason for the difference in the hash generated.
(2) Hashes are unrepeatable: As we all know that the hashes can't be repeated so that is why when we generated hash for CryptoAcademy, it was different from the hash generated when we used cryptoacademy.
(3) Resistance to collision: We are using the same word with same meaning but the hashes generated were different just because of some letters and this shows resistant to collision.

(4)In your own words explain the difference between hash and cryptography.

Difference between Hash and cryptography.
| Hash | Cryptography |
|---|---|
| We can not get the original information from the hash as it is irreversible. | Original information can be retrieved by using encryption key and algorithm. |
| Hash | Cryptography |
|---|---|
| Hash is more secure than cryptography due to the generation of new key for every step or process. | Cryptography is less secure than hash. |
| Hash | Cryptography |
|---|---|
| Hash has a fixed length that can't vary with the length of information provided. | Cryptography doesn't have have a fixed length and vary with the length of information provided. |
| Hash | Cryptography |
|---|---|
| Used to send private keys or passwords. | Used to send private and confidential information. |
| Hash | Cryptography |
|---|---|
| Doesn't require any key. | Requires key to decrypt data or retrieve the original information. |
| Hash | Cryptography |
|---|---|
| It converts the original information into alphanumerical data(combination of alphabet and numbers). | It is used to encrypt and decrypt data. |

Conclusion
In this lecture I came to know about hash and cryptography, their use and their features. I researched about resistance to collision and preimage collision properties of hash.
Then I explored Tronscan and etherscan to verify the hash of block and transaction. Then I generated SHA256 hash and came to know about the difference in hash due to some minor changes.
And then at last i differentiate between Hash and cryptography.

Thank you
For the attention of @pelon53
Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
👆 Un poco complicado que lo entienda cualquier persona. Debes explicarlo un poco más claro.
Buen trabajo, felicitaciones.
Recomendaciones:
Calificación: 9.7