Siz Education||what is virtualization and How it Works?||by @fatimawasif||15%of reward for siz-official
Assalamualaikum every one.Hope all of you will be fine and enjoying the good health. Today I come up with a very informative topic of Information Technology.That is Virtualization.
What is virtualization?
Virtualization is to create a virtual rather than real version of something, such as an operating system (OS), server, storage device or network resources.
Virtualization uses software that simulates hardware performance to create a visual program. It allows technology organizations to run multiple operating systems, more than one virtual system and multiple applications on a single server. The benefits of tangible assets include greater efficiency and economy.
How virtualization works?
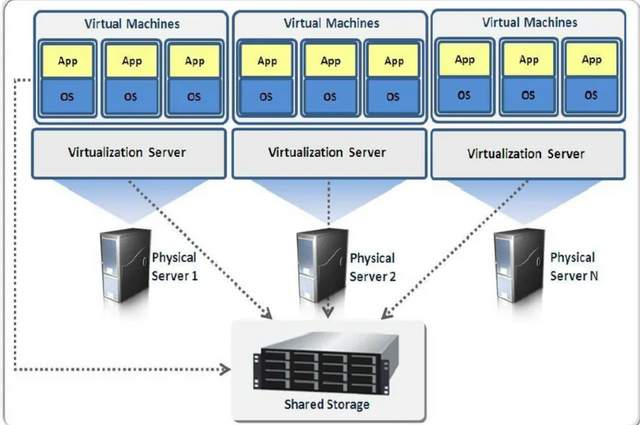
Virtualization defines a technology in which a system, guest application (guest OS) or data storage is removed from the original basic hardware or software. The primary use of virtualization technology is server virtualization, which uses a layer of software - called a hypervisor - to mimic the underlying hardware. This usually includes CPU memory, input / output (I / O) and network traffic. Hypervisors take physical resources and classify them for use by the physical environment. They can stay on top of the OS or can be installed directly on the hardware. Lastly is how many businesses make their plans work.
Xen hypervisor is a program used to managing low-level connections that occur between virtual machines (VMs) and virtual hardware. The Xen hypervisor allows simultaneous operation, production and management of various virtual machines in one visible environment.
With the help of a hypervisor, the guest OS, which usually works with real hardware, now does so by mimicking the software of that hardware; often, the visitor OS is unaware that it is a masterpiece. While the functionality of this visual app is not the same as the performance of an app running on real hardware, the concept of visualization works because most guest apps and apps do not require the full use of the underlying hardware. This allows for greater flexibility, control and separation by removing the reliance on a given hardware platform. While originally intended for server identification, the idea of doing good has spread to applications, networks, data, and desktops.Each traditional side view is compared to the actual construction.The fraudulent process followed the steps outlined below:
Hypervisors separate resources from their physical areas.Resources are taken and separated, as needed, from the visible area to the various visible areas.
System users interact and perform calculations within the physical environment.In response, the hypervisor transmits a message to the body system and maintains changes. This process will happen at almost traditional speed.
The visual environment is often referred to as a guest machine or a visual machine. It acts as a single data file that can be transferred from one computer to another and open to both; it is expected to do the same for all computers.
Types of virtualization technology
You probably know a little bit about efficiency when you have partitioned your hard drive into different partitions. Partitioning the logical partition of a hard disk drive is to create, in fact, two separate hard drives.
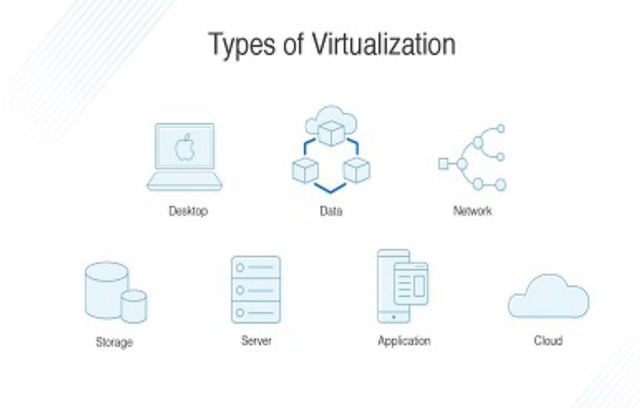
There are six IT areas where virtualization is at the forefront:
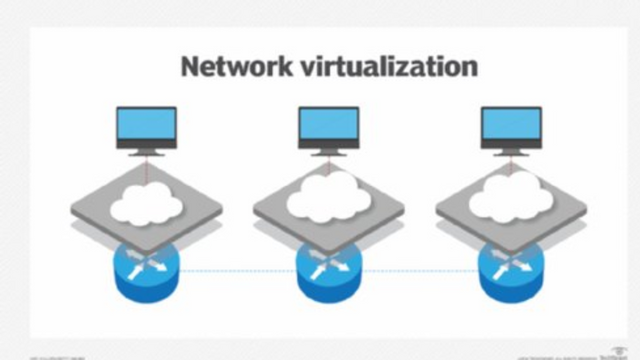
1•Network virtualization
It is the process of integrating available resources into a network by splitting available bandwidth into channels, each of which is independent and can be assigned to a specific server or device in real time. Virtualization hides the real complexity of the network by splitting it into components, like your partitioned hard drive that makes it easier to manage our files.
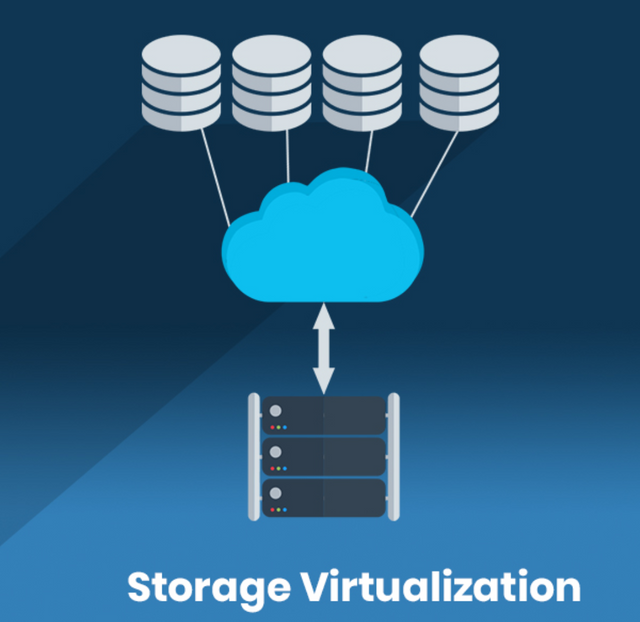
2•Storage virtualization
It is the integration of actual storage from multiple network storage devices that appears to be a single storage tool managed from a central console. Storage detection is often used for storage networks.
3•Server virtualization
It is helpful to encrypt server resources that includes number and identity of individual physical servers, processors and operating systems . The aim is to prevent the user from understanding and managing complex server resource information while maximizing resource allocation and usage and saving for later expansion capabilities.
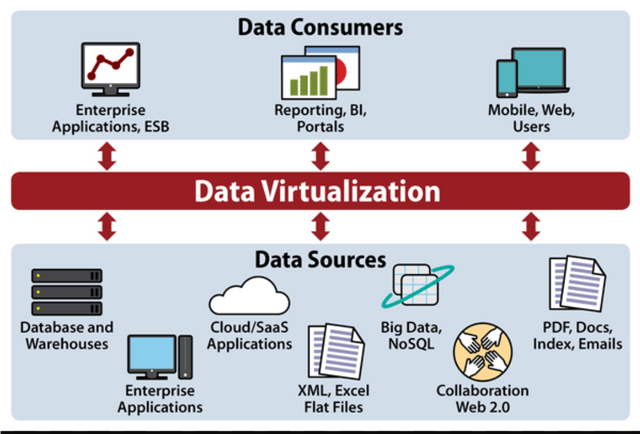
4•Data virtualization
It removes the details of traditional data management and data management technologies, such as location, functionality or format, allowing for greater accessibility and greater robustness to suit business needs.
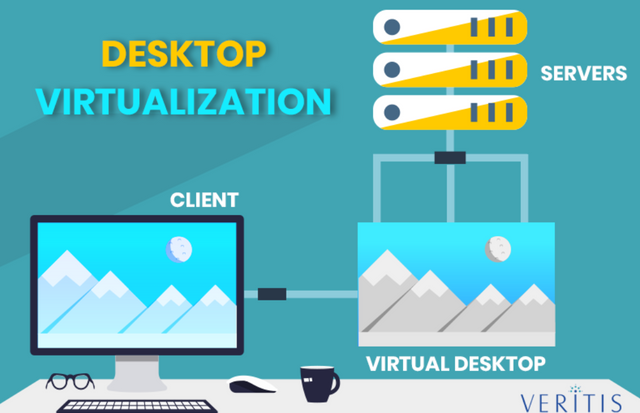
5•Desktop virtualization
Desktop virtualizationis the detection of a channel load rather than a server. This allows the user to access the desktop remotely, usually using a small client desk.
6•Application virtualization
An application virtualization still needs calculation and infrastructure.
This type of virtualization removes the application layer away from the operating system. In this way, the application can proceed in a built-in manner without relying on the application below.
Virtualization can be seen as part of a complete IT business practice that includes self-regulation, a situation in which the IT environment will be able to control itself based on visual activity, and computer usage, where computer processing power is seen as a service that clients can pay only when needed. The general purpose of eye contact is to bring the management function together while improving tension and workload.
Source
Desktop virtualizationis the detection of a channel load rather than a server. This allows the user to access the desktop remotely, usually using a small client desk.
Benefits
The benefits of using the virtualization include the following:
Low cost.
Virtualization reduces the number of hardware servers needed within the company and the data center. This reduces the overall cost of purchasing and maintaining a large amount of hardware.
Easy disaster recovery.
Disaster recovery is very easy in a personalized area. Standard abstracts provide up-to-date information, allowing visual equipment to be backed up and accessible. Even in an emergency, the visible machine can be moved to a new location within minutes.
Easy migration to the cloud.
Virtualization brings companies closer to finding a completely cloud-based environment. Virtual machines can be sent to a data center to build cloud-based infrastructure. The ability to embrace cloud-based thinking through positive visibility makes cloud migration much easier.
Lack of reliance on the seller.
Visible agnostic equipment in hardware configuration. Because of the virtualizing hardware and software sources the company has no need to rely on the vendor for these physical resources.
Simple test.
Exploration is very small in the visible area. Even if a major mistake is made, the test does not need to stop and go back to the beginning. It can simply revert to the previous image and continue testing.
Quick backups.
Backups can be taken over by both the virtual server and the virtual machine. Automatic images are taken throughout the day to ensure that all data is up to date. In addition, virtual machines can be easily moved between each other and reused.
Improved productivity.
A few resources determine the amount of time spent managing and maintaining servers. Activities that can take days or weeks in a visible area can be done in minutes. This allows employees to spend more time doing extra work, such as raising money and promoting business plans.
Increase in output
Virtualization gives companies the advantage of increasing their output.
Fast shipping and re-distribution.
When a portable server crashes, the backup server may be out of date or out of date. There may also be no image or server clone available. If so, the redistribution process can be time consuming and tedious. However, if the data center is improved, the process is faster and easier enough. Real-time backup tools, such as Veeam, are available to speed up the process into minutes.
Limitations
Before moving to a more physical location, it is important to consider the various costs involved.
•There are also safety risks associated with doing good. Details are essential to business success and,Data is critical to business success and, therefore, is a common target for attack.
•The chances of encountering a data breach are greatly increased while using virtualization.
•The investment which is required needed to make software as well as the hardware that make virtualization visible, could be costly.
•There are also software license considerations that must be considered when creating a virtual environment.
•Converting to visibility takes time and may come with a learning curve.
•Establishing and managing a computerized environment requires each IT staff member to be well-trained and competent.
•Some applications are not compatible when presented in a visual environment.
• IT staff will need to be prepared to face this challenge and must face it before turning around.
•There are also safety risks associated with doing good.
•Data is critical to business success and, therefore, is a common target for attack.
The chances of encountering a data breach are greatly increased while using virtualization.

That's all for today's topic. Hope it will be informative to you. Thanks for your time.
Special Thanks to
@ cryptokraze
@siz-official
@suboohi
@booming
@vvarishay
And all the siz team.



Very well detailed post dear friend on virtualization technology and it is too much difficult.
thanku bro
Virtualization is very good and useful thanks for sharing