Fake Cell Phone That Can Infect Your Computer Just by Plugging It In.
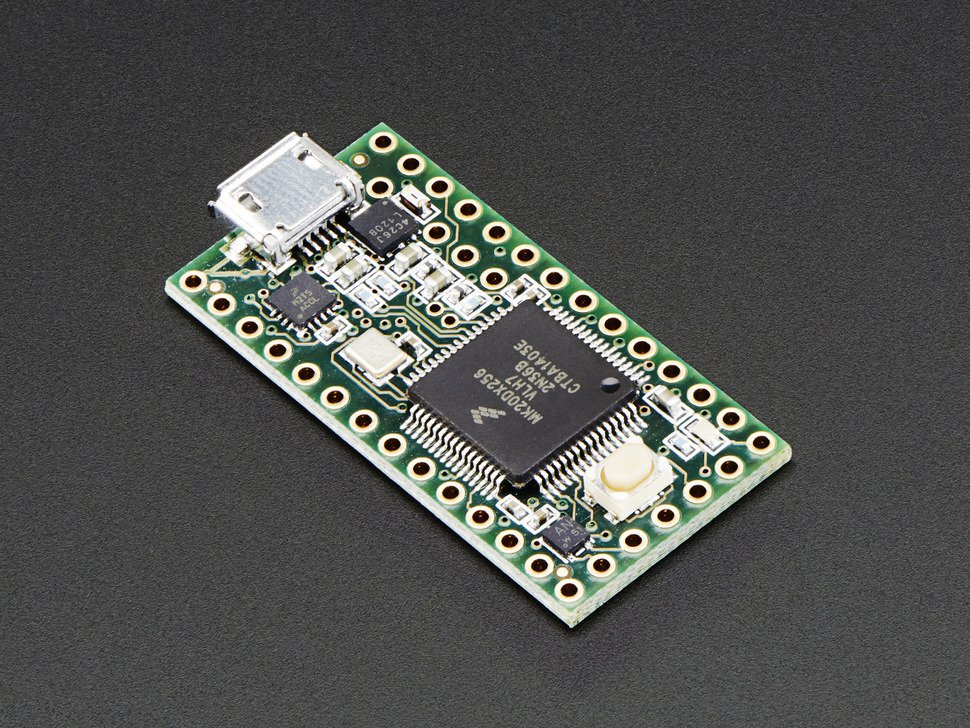
This is a device that I used to use on pentests for physical engagements it works like the old leave USB's every where trick except this one evades most malware and uses a small microcontroller called a Teensy 3.1
This small device hidden in a "Dummy phone" when plugged in tricks you computer into thinking it is a USB keyboardand types the commands to visit an infected webpage and performs a drive by attack. Which is an attack that requires no user interaction.
The only way to stop devices like this is to USB white list. which is expensive. I am actually working on a opensource free version of usb white lister it stops HID (Human Interface device) attacks like this Ill keep you posted.
Thanks again for viewing and make sure to subscribe for more news about hacking and security.
I'm going to show this to my friend in netsec. Awesome stuff, man. I'll be thinking twice before I plug in random tech that I find lying around. I guess a virtual machine might help with that?
As you should its crazy the amount of stuff people do to hack computers