Chaos as Guardian of a Public Peace. Hash Functions and Their Applications
Hi Steemers! This is Kate.
In my introduction post I mentioned that I'm interested in blockchain technologies, so today I would like to tell you about concept that lies at the basis of #blockchain and bitcoin and also used in many fields of IT.
Yes, as most of you might guess I'll tell about Hash Functions
What is Hash Function?
Wikipedia says: "A hash function is any function that can be used to map data of arbitrary size to data of fixed size". This is not quite true. In fact, when hash functions are mentioned, it's implied that they should also have a Avalanche or Snowball effect. That means that if at least one symbol of function argument was changed, then function value should be changed drastically.

Here are examples of MD5 hash functions applied to the following strings:
| Function argument | Hash Sum |
|---|---|
| "Hi Steemers!" | 9d0f664eed40fa3b02fc08e8a31e430c |
| "Hi steemers!" | a4f4f4f12c248041ea21288dc85e6366 |
| "Hi, Steemers!" | 8781a9cc0e5222a372d022b96b611974 |
You can check and play around with hashes here
Can you see that? We just forgot one comma and the value of the hash function has changed to beyond recognition! The same effect we will observe if we just change upper case to lower. This effect is called the Avalanche effect. This is the Chaos. This particular property of hash functions forbids to find the input argument. You might wonder, what "Output of hash function" means. Let me briefly explain.
Each output character is a digit in hexadecimal notation. Of course you can convert it to decimal and binary numerical system, it all depends on the circumstances of a particular task.
There are various hash functions. Firstly they differ in the transformation algorithm (mapping) and secondly in the size of the output word. The most popular hash functions are SHA (a whole family), MD4, MD5.
Note that hashfunction can be calculated not only for the text information, but for any type of data. We remember that any file is a sequence of bits, right? :)
How to use chaos for your own purposes
Hash functions have countless applications but here we'll focus on those that seem to me most revealing.
Error checking on received messages
Let's imagine that our company produce microchips and uses silicone and silicon. For example, when you submit the order you write a message to your supplier: "Hello, Jimmy! I need 3kg of silicone. Can you please deliver it tomorrow?"
But due to poor communication channel, the last character "e" is lost and he gets the message: "Hello, Jimmy! I need 3kg of silicon. Can you please deliver it tomorrow?". Then you get the wrong product. In general, consequences can be very serious.
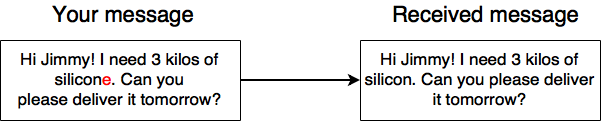
Hash functions can be used to avoid such a situations. You just should concatenate hash sum of the message to its ending. Then receiving party will be able to understand if the incoming message contains any errors. Here is a clear explanation:
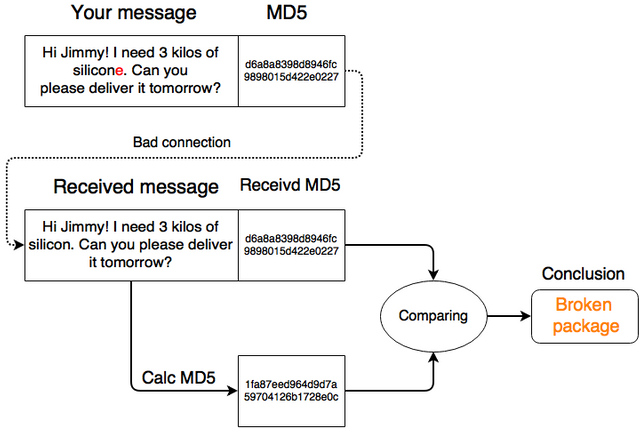
Thanks to such checks you always get the right messages. In a case when wrong message was received, resending is required that obviously leads to loss of connection speed.
Check username and password without storing them to the database
Nowadays almost every web site requires to sign up in order to create a personal account, for which you should make up login and password. Once you put in your credentials, server compare it with the stored one and allows or declines you access. So it turns out that if the website can check your password then it knows it somehow.
What if the website get hacked? Will hackers get your password? Not really!
Most password storage systems are built so that they don't keep your password explicitly. For security purposes, the sites store only hash sums of your passwords.
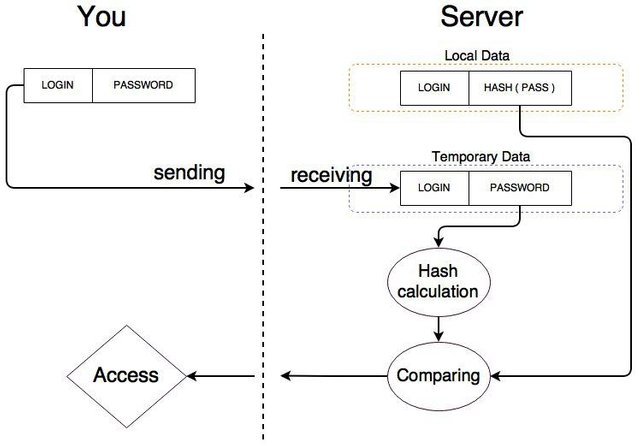
In fact this diagram just shows the basic concept and is a bit more complicated in practice.
Checking for changes in cloud storages
Most of you use cloud storage services. Usually it's a folder that is synchronized with remote server. You add image kitty.png to this folder. This picture is uploaded to the server and after a while you have edited it from your tablet. No doubts the picture will be immediately updated at your local computer folder.

Original and Edited Images
How do the computer know you changed the picture even if its name and size are same?
You could probably think that computer downloads image and compares it with the local one but It would lead to constant high load on your Internet connection (especially if it's not an image but 4k film).
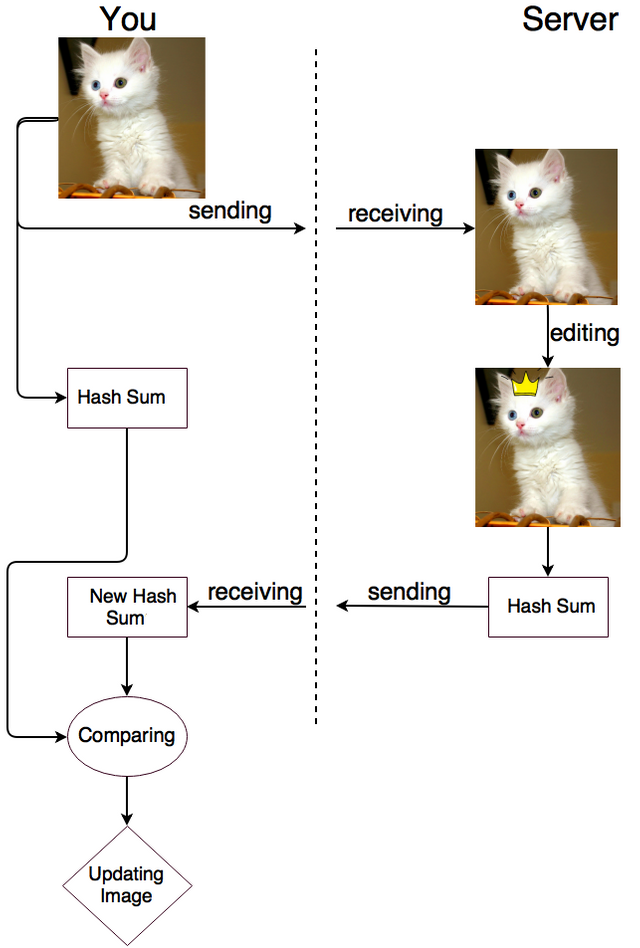
Operation principles of synchronization of cloud services
Here hash functions come to the aid again! Server calculates hash sums of all uploaded/updated files and sends them to your local computer for comparison.
Conclusion
Summing up, we got acquainted with hash functions and found out how extremely useful they can be. It should be noted that the scope of hash functions application is very large and nowadays they can be met in almost every area of IT. Moreover, hash functions formed the security basis of the blockchain technology. However this article turned out being big enough so I'll tell you about it a bit later.
Follow me on Steemit.
Best Regards,
Kate
Nice article here, I hope this article is big enough for you to talk more about it!
you smart cookie, I love you, keep them coming!!!!
Thanks @feminism.
Stay tuned
funny thing is you and somedude thought this was a stripper whore on her introduction earnest. you sick piece of shit! I hope I'll find you soon so I can kill you
I still think the same thing, I just dont like repeating myself :)
When you have something to say about me say it to my face, not on other people's comment.
I think this post is trash, and the other one was written by her nerd friend who introduced her to steemit, with whom she is probably sharing rewards, as it would not have gotten the same amount if it was from a guy. I'm sure you know that.
And FYI, I have nothing against stripper whores
Thanks a lot for this article. As always, very clear! :)
thanks,
I do my best to develop popularscience rubric and lay out clear material
How I wish I can relate to this topic. I still have a lot to learn about blockchain.
Just keep learning and you will notice your advancements soon.
Never give up
@krishtopa I wish your doppelgänger lived in Long Beach , California!!
I dream to live in California)
I live a few blocks away from the beach. We have the best weather in the world if you like sunshine every day.
This is almost, but not quite, beyond me. Cool post. Does this have broader, as yet unrealized implications for the future?
Sure, really nice post and explanation, thank you!
Thanks, @smailer.
Follow me to learn about my further posts
Lol, I'm follow you already few days :)) check your followers list .
@pierce-the-veil: Excellent Post @krishtopa! Your diagrams cleared up a lot of confusion for me. Well explained and thank you for inspiring me to feel a little smarter about hash after reading.

Keep up the good work, you seem to have hit your stride. Upvoted.
@pierce-the-veil
Thanks.
Worked a lot on this post to provide good and clear examples of hash functions applications
Very Good
thanks
Nice :) new post about math! I like it :) But need to read first :)