New Ransomware Variant Petya Spreading Rapidly
Wanna cry (again)? Many companies as of this morning are likely thinking of the recent ransomware outbreak as a massive outbreak occurred this morning throughout Ukraine.

Image of infected supermarket in Ukraine uploaded by Twitter user NewsReport365
This ransomware is a new variant of "Petya", and from initial reports it apparently both utilizes a vector similar to WannaCry by exploiting the now infamous "ETERNAL BLUE" exploit (See Microsoft Security Bulletin MS17-010 here) along with the addition of spreading via email by taking advantage of a Microsoft Office vulnerability CVE-2017-0199, click for FireEye documentation on the exploit.
Part of how Petya varies from WannaCry is also in the execution of the encryption itself. Rather than encrypt files on the filesystem individually, it instead encrypts the MFT (Master File Table) on the target computer and replaces the MBR (Master Boot Record) with its own code providing the ransom note & payment address... rendering the device unable to boot.
As of the time of this post, it appears that 15 ransom payments have occurred to the bitcoin address 1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX (current + pending transactions).
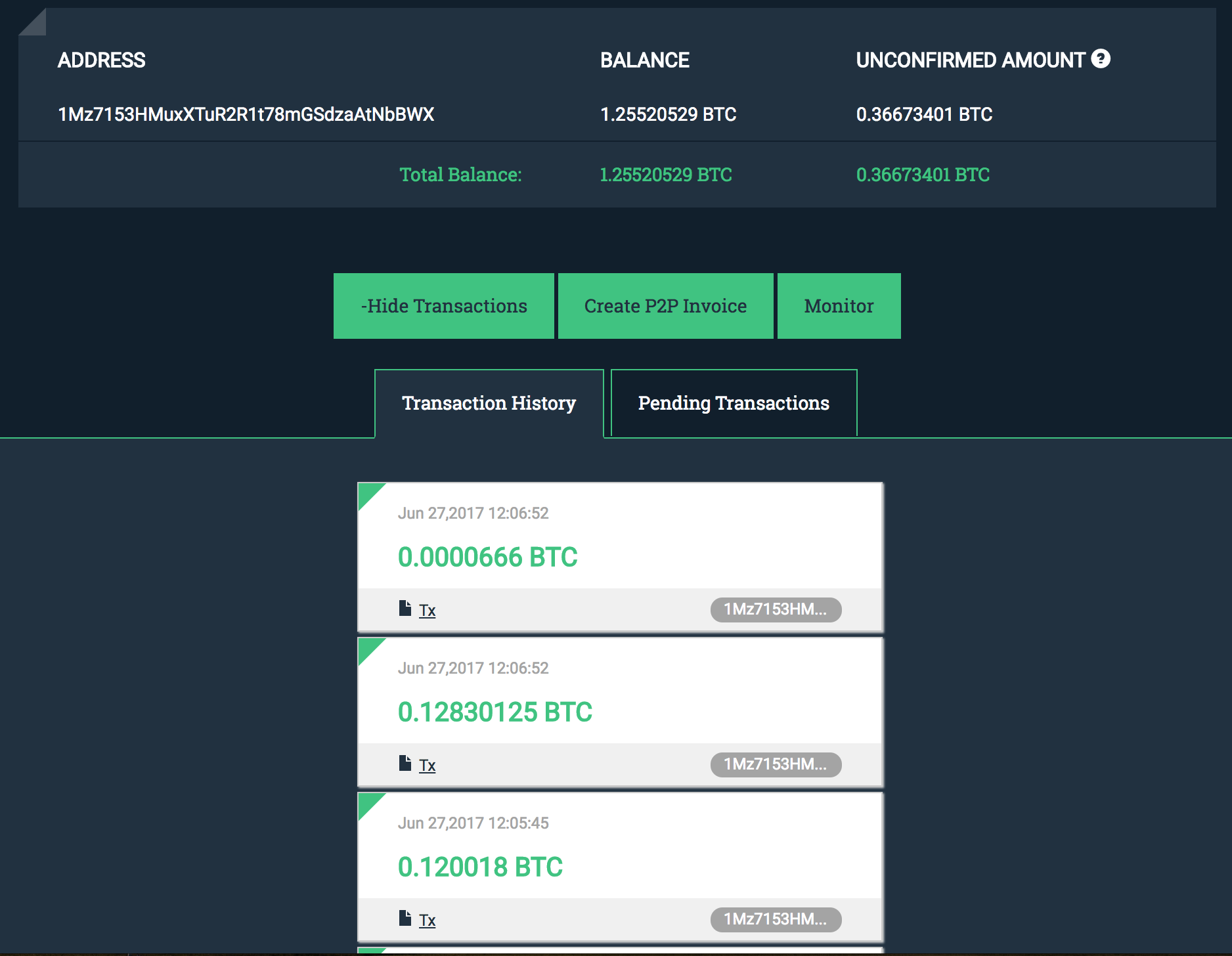
Screenshot from Blockonomics
This is spreading rapidly beyond Ukraine and has affected several large companies in multiple industries. As far as prevention goes, it is important to ensure the previously mentioned vulnerabilities are patched and as always, think before you click! File attachments, even word documents and spreadsheets can contain malicious code so it is unadvisable to open anything you receive in an email you don't recognize to avoid becoming a victim of a phishing attack. Additionally, it's a good idea to frequently backup any data you don't want to lose offline and/or remotely.
Hope you've all found this post informative, feel free to drop any questions below and let me know if you have any suggestions or enjoy the content! This is my first security-related post, but it's an interest of mine so I'm curious if there's an interest for similar topics on the platform here.
Edit to add one last thing
If infected, I wouldn't recommend paying the ransom. At this point, due to the uncommon method of handling payments they don't have a way of receiving emails to identify who paid (see article from TheVerge below):
https://www.theverge.com/2017/6/27/15881110/petya-notpetya-paying-ransom-email-blocked-ransomware

Congratulations @echozaurora! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honnor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPBy upvoting this notification, you can help all Steemit users. Learn how here!
Congratulations @echozaurora! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honnor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPBy upvoting this notification, you can help all Steemit users. Learn how here!