How to Configure Your Yubikey for Use with GnuPG
Goal
The goal of this procedure is to set up a Yubikey 4 with a strong master key and three derived subkeys, one for authentication, one for encryption and one for signing. Generally keys can be generated directly on the Yubikey, which is probably the most secure way to do it, but this way you cannot backup your key. The method I present here is to use a live-system that is air-gapped during key-creation.
What you need:
- 1x Yubikey 4
- 1x USB thumb drive or SD-card that you trust will live a long time
- 1x Bootable Ubuntu USB thumb drive
You can download the latest Ubuntu images here. Instructions on how to create a bootable USB stick can be found here: - 2x Computer. One to read this guide and one to use as air-gapped machine to create your keys on
Unboxing a new Yubikey
Because it has been shown that Yubikeys can be falsified by an attacker it is very important that you make sure you receive a genuine one. The best way to do that is to order directly from the manufacturer Yubico, instead of using some re-seller like Amazon or eBay.
Once you receive your package, first make sure there is an unbroken seal on the bag containing the device, then check the device itself for any signs of tampering. Have a look at other images of your Yubikey online to be sure you really received a genuine one.
Enabling CCID
In case you are using an older Yubikey NEO, you will have to download the Yubikey NEO manager in order to enable the CCID feature. For the Yubikey 4 this is no longer required.
Preparing the live system
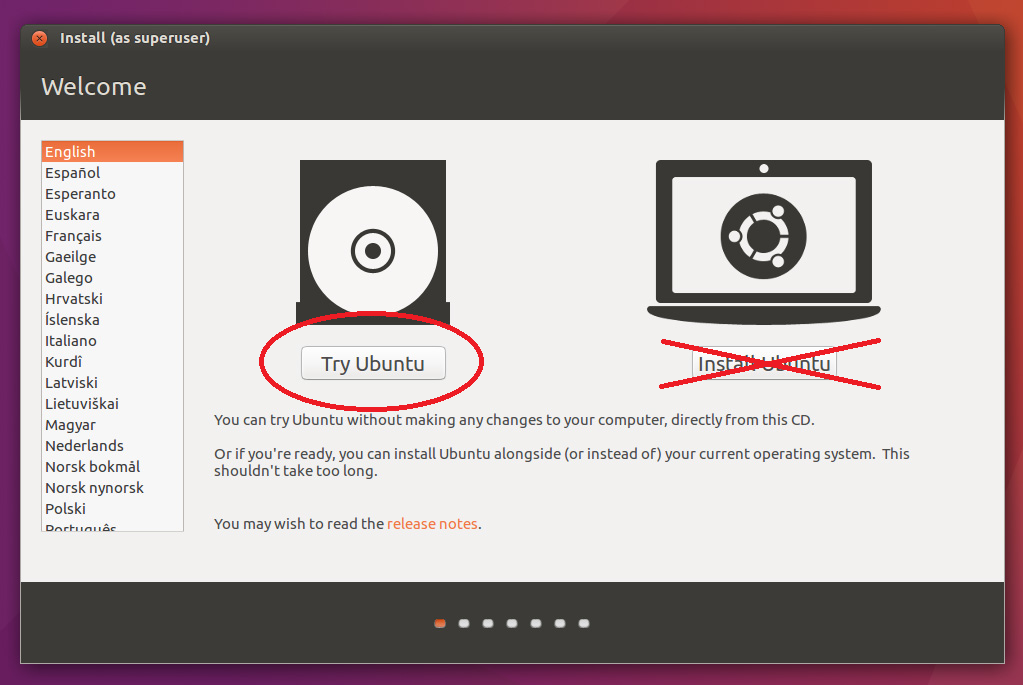
Shut down the computer you want to create the keys on. Insert the bootable USB stick and start it up. Do not install Ubuntu, simply choose 'Try Ubuntu'. This should take a moment and then show you a nice clean Ubuntu desktop.
The first thing you might want to do is reconfigure the keyboard-layout to fit your country. See this post for instructions.
Next, you need to enable the package-source 'universe' to be able to install the required tools. This is most easily achieved via the Ubuntu Software Center. For more detailed instructions, see this link.
As soon as you've done this, open a terminal (using Ctrl+Alt+T) and run the following commands:
sudo apt-get update
sudo apt-get install gnupg2 pcscd scdaemon pcsc-tools
This will install (and/or upgrade) all the tools you will need to create your keys and store them on the device. Do not run a full apt-get upgrade, as this will take a lot of time and possibly fill the live-system's very limited RAM-drive to the limit.
To test if all is working, plug in your Yubikey and run gpg2 --card-status. If this command produces output that looks like this, you're good to go:
Turn off networking completely
To make sure no one can steal your keys once they have been created you must now completely remove the computer running the live system from the internet. If the computer is a laptop with some kind of hardware switch for networking, deactivate it there as well. The more certain you make that a connection to the internet is impossible during and after the next steps, the more secure your keys will be. After you have taken all measures to disconnect the machine from the net, try to use Firefox to access google or some other page. If this does no longer work you can be relatively certain there is no more connection.
The Heart of the Issue: Key Generation
ECC or RSA
All the preparations are out of the way and we are ready to create the keys to be stored on the Yubikey. But first there's a choice to be made concerning the type of keys you want to use. There are two major categories:
- RSA keys
- ECC keys
From a users perspective, the two variants are somewhat identical, however the math behind them is (afaik) completely different. The most important points to help your decision:
- Yubikey 4 supports either ECC-keys with 256 or 384 bits, or RSA keys with up to 4096 bits.
- ECC gives you more 'security per bit', meaning an ECC key with 384 bits is at least as secure as an RSA key with 4096 bits
- For ECC, there are currently three popular variants: NIST curves, Brainpool curves and the 25519 curve. NIST is rumored to have some NSA backdoors, Brainpool is much slower than NIST, and 25519 is currently not supported by the Yubikey 4.
I would prefer to go with ECC-25519, but since it is not supported and the other two ECC variants do not convince me either, my current recommendation is to go with RSA-4096 keys.
Key structure
A Yubikey has three 'slots' for keys. One for authentication, one for signing and one for encryption. Based on that, we are going to create a master-key with three derived sub-keys, one for every functionality. Furthermore, we will create a revocation certificate and export all the required gpg- and ssh public-keys.
A word concerning key expiration: It is good practice to set an expiration date for your keys. Why? If you lose the key or simply do no longer wish to use it, it will automatically be invalid after that time. Also, it does not hurt you in any way. As long as you control the master-key, you can always change the expiration date of the master- and any subkeys, even after they have already expired. The master-key itself never expires, no matter what time you set here.
When following the instructions below, you will encounter points where gpg prints something like We need to generate a lot of random bytes. It is a good idea to .... and seems to be stuck. It is not stuck, but generating your key now. Because it is not relying on any pseudo-random number generator, it uses entropy generated on your computer. Long story short: Leave the console window open and be patient. If you want to speed up the process, open and close applications, move the mouse, write text.
Master-key
ubuntu@ubuntu:~$ gpg2 --expert --full-gen-key
gpg (GnuPG) 2.1.15; Copyright (C) 2016 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
(7) DSA (set your own capabilities)
(8) RSA (set your own capabilities)
(9) ECC and ECC
(10) ECC (sign only)
(11) ECC (set your own capabilities)
Your selection? 8
Possible actions for a RSA key: Sign Certify Encrypt Authenticate
Current allowed actions: Sign Certify Encrypt
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? s
Possible actions for a RSA key: Sign Certify Encrypt Authenticate
Current allowed actions: Certify Encrypt
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? e
Possible actions for a RSA key: Sign Certify Encrypt Authenticate
Current allowed actions: Certify
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? q
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 503d
Key expires at Mon 31 Dec 2018 12:32:37 PM UTC
Is this correct? (y/N) y
GnuPG needs to construct a user ID to identify your key.
Real name: Homer Simpson
Email address: h.simpson@domain.com
Comment: Programmer
You selected this USER-ID:
"Homer Simpson (Programmer) <h.simpson@domain.com>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? o
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
gpg: key C50738FFBA0FC25A marked as ultimately trusted
gpg: revocation certificate stored as '/home/ubuntu/.gnupg/openpgp-revocs.d/79634C2F9AD0D03CB47EAF17C50738FFBA0FC25A.rev'
public and secret key created and signed.
pub rsa4096 2017-08-15 [C] [expires: 2018-12-31]
79634C2F9AD0D03CB47EAF17C50738FFBA0FC25A
uid Homer Simpson (Programmer) <h.simpson@domain.com>
Backup of master-key
This backup can restore your master-key. Keep it safe and offline.
gpg2 -a --export-secret-keys 79634C2F9AD0D03CB47EAF17C50738FFBA0FC25A > Desktop/masterkey.txt
Revocation certificate
This certificate can be used to invalidate your master- and all subkeys. Keep it safely stored.
ubuntu@ubuntu:~$ gpg2 --gen-revoke 79634C2F9AD0D03CB47EAF17C50738FFBA0FC25A > Desktop/revocation-cert.txt
sec rsa4096/C50738FFBA0FC25A 2017-08-15 Homer Simpson (Programmer) <h.simpson@domain.com>
Create a revocation certificate for this key? (y/N) y
Please select the reason for the revocation:
0 = No reason specified
1 = Key has been compromised
2 = Key is superseded
3 = Key is no longer used
Q = Cancel
(Probably you want to select 1 here)
Your decision? 1
Enter an optional description; end it with an empty line:
>
Reason for revocation: Key has been compromised
(No description given)
Is this okay? (y/N) y
ASCII armored output forced.
Revocation certificate created.
Please move it to a medium which you can hide away; if Mallory gets
access to this certificate he can use it to make your key unusable.
It is smart to print this certificate and store it away, just in case
your media become unreadable. But have some caution: The print system of
your machine might store the data and make it available to others!
Sub-keys
ubuntu@ubuntu:~$ gpg2 --expert --key-edit 79634C2F9AD0D03CB47EAF17C50738FFBA0FC25A
gpg (GnuPG) 2.1.15; Copyright (C) 2016 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Secret key is available.
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> addkey
Please select what kind of key you want:
(3) DSA (sign only)
(4) RSA (sign only)
(5) Elgamal (encrypt only)
(6) RSA (encrypt only)
(7) DSA (set your own capabilities)
(8) RSA (set your own capabilities)
(10) ECC (sign only)
(11) ECC (set your own capabilities)
(12) ECC (encrypt only)
(13) Existing key
Your selection? 8
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Sign Encrypt
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? e
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Sign
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? q
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 503d
Key expires at Mon 31 Dec 2018 01:09:11 PM UTC
Is this correct? (y/N) y
Really create? (y/N) y
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
ssb rsa4096/83F37AC3EB3EEE94
created: 2017-08-15 expires: 2018-12-31 usage: S
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> addkey
Please select what kind of key you want:
(3) DSA (sign only)
(4) RSA (sign only)
(5) Elgamal (encrypt only)
(6) RSA (encrypt only)
(7) DSA (set your own capabilities)
(8) RSA (set your own capabilities)
(10) ECC (sign only)
(11) ECC (set your own capabilities)
(12) ECC (encrypt only)
(13) Existing key
Your selection? 8
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Sign Encrypt
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? s
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Encrypt
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? q
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 503d
Key expires at Mon 31 Dec 2018 01:10:39 PM UTC
Is this correct? (y/N) y
Really create? (y/N) y
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
ssb rsa4096/83F37AC3EB3EEE94
created: 2017-08-15 expires: 2018-12-31 usage: S
ssb rsa4096/C20F64EA1C4D2C94
created: 2017-08-15 expires: 2018-12-31 usage: E
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> addkey
Please select what kind of key you want:
(3) DSA (sign only)
(4) RSA (sign only)
(5) Elgamal (encrypt only)
(6) RSA (encrypt only)
(7) DSA (set your own capabilities)
(8) RSA (set your own capabilities)
(10) ECC (sign only)
(11) ECC (set your own capabilities)
(12) ECC (encrypt only)
(13) Existing key
Your selection? 8
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Sign Encrypt
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? s
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Encrypt
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? e
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions:
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? a
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Authenticate
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? q
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 503d
Key expires at Mon 31 Dec 2018 01:14:11 PM UTC
Is this correct? (y/N) y
Really create? (y/N) y
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
ssb rsa4096/83F37AC3EB3EEE94
created: 2017-08-15 expires: 2018-12-31 usage: S
ssb rsa4096/C20F64EA1C4D2C94
created: 2017-08-15 expires: 2018-12-31 usage: E
ssb rsa4096/C66FE2FCF049C26F
created: 2017-08-15 expires: 2018-12-31 usage: A
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> save
Backup sub-keys
gpg2 -a --export-secret-subkeys C50738FFBA0FC25A > Desktop/subkeys.txt
Export ssh-public-key
gpg2 --export-ssh-key C50738FFBA0FC25A > Desktop/ssh-publickey.txt
Export gpg-public-key
gpg2 -a --export C50738FFBA0FC25A > Desktop/gpg-publickey.txt
So far, so good
Puh! The hard part is over. All the keys are created and you should now have a couple of files on your desktop, namely:
- masterkey.txt
- subkeys.txt
- ssh-publickey.txt
- gpg-publickey.txt
Place the first two files (masterkey and subkeys) on one (or better multiple) backup drive like an usb thumb-drive or an SD-card and place it (or them) in very safe places like the vault of a bank. If someone with bad intentions gets their hands on this, you are SCREWED and they can do A LOT of harm. Also save the Yubikey PINs and the passphrases of your keys alongside these two files.
Anyway. The other two files (gpg- and ssh- publickey) are best stored on your NAS or in the cloud. They do not need to be kept safe, just make sure you do not lose them.
Nope, you cannot turn off the live-system yet. We still need to configure the Yubikey and transfer the keys.
Configuring PINs
Plug in your Yubikey and follow the commands below to change both the user- and the admin PIN. Best you make another textfile with these PINs and store it alongside the backup-files created above. If you forget the PINs, the Yubikey is pretty much bricked.
Note: The default PIN is 123456 and the default admin PIN is 12345678
$ gpg2 --card-edit
gpg/card> admin
Admin commands are allowed
gpg/card> passwd
gpg: OpenPGP card no. XXXXXX detected
1 - change PIN
2 - unblock PIN
3 - change Admin PIN
4 - set the Reset Code
Q - quit
Your selection? 3
PIN changed.
...
Your selection? 1
PIN changed.
...
Your selection? q
gpg/card> quit
Moving keys to Yubikey
ubuntu@ubuntu:~$ gpg2 --edit-key C50738FFBA0FC25A
gpg (GnuPG) 2.1.15; Copyright (C) 2016 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Secret key is available.
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
ssb rsa4096/83F37AC3EB3EEE94
created: 2017-08-15 expires: 2018-12-31 usage: S
ssb rsa4096/C20F64EA1C4D2C94
created: 2017-08-15 expires: 2018-12-31 usage: E
ssb rsa4096/C66FE2FCF049C26F
created: 2017-08-15 expires: 2018-12-31 usage: A
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> key 2
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
ssb rsa4096/83F37AC3EB3EEE94
created: 2017-08-15 expires: 2018-12-31 usage: S
ssb* rsa4096/C20F64EA1C4D2C94
created: 2017-08-15 expires: 2018-12-31 usage: E
ssb rsa4096/C66FE2FCF049C26F
created: 2017-08-15 expires: 2018-12-31 usage: A
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> keytocard
Please select where to store the key:
(2) Encryption key
Your selection? 2
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
ssb rsa4096/83F37AC3EB3EEE94
created: 2017-08-15 expires: 2018-12-31 usage: S
ssb* rsa4096/C20F64EA1C4D2C94
created: 2017-08-15 expires: 2018-12-31 usage: E
ssb rsa4096/C66FE2FCF049C26F
created: 2017-08-15 expires: 2018-12-31 usage: A
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> key 2
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
ssb rsa4096/83F37AC3EB3EEE94
created: 2017-08-15 expires: 2018-12-31 usage: S
ssb rsa4096/C20F64EA1C4D2C94
created: 2017-08-15 expires: 2018-12-31 usage: E
ssb rsa4096/C66FE2FCF049C26F
created: 2017-08-15 expires: 2018-12-31 usage: A
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> key 1
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
ssb* rsa4096/83F37AC3EB3EEE94
created: 2017-08-15 expires: 2018-12-31 usage: S
ssb rsa4096/C20F64EA1C4D2C94
created: 2017-08-15 expires: 2018-12-31 usage: E
ssb rsa4096/C66FE2FCF049C26F
created: 2017-08-15 expires: 2018-12-31 usage: A
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> keytocard
Please select where to store the key:
(1) Signature key
(3) Authentication key
Your selection? 1
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
ssb* rsa4096/83F37AC3EB3EEE94
created: 2017-08-15 expires: 2018-12-31 usage: S
ssb rsa4096/C20F64EA1C4D2C94
created: 2017-08-15 expires: 2018-12-31 usage: E
ssb rsa4096/C66FE2FCF049C26F
created: 2017-08-15 expires: 2018-12-31 usage: A
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> key 1
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
ssb rsa4096/83F37AC3EB3EEE94
created: 2017-08-15 expires: 2018-12-31 usage: S
ssb rsa4096/C20F64EA1C4D2C94
created: 2017-08-15 expires: 2018-12-31 usage: E
ssb rsa4096/C66FE2FCF049C26F
created: 2017-08-15 expires: 2018-12-31 usage: A
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> key 3
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
ssb rsa4096/83F37AC3EB3EEE94
created: 2017-08-15 expires: 2018-12-31 usage: S
ssb rsa4096/C20F64EA1C4D2C94
created: 2017-08-15 expires: 2018-12-31 usage: E
ssb* rsa4096/C66FE2FCF049C26F
created: 2017-08-15 expires: 2018-12-31 usage: A
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> keytocard
Please select where to store the key:
(3) Authentication key
Your selection? 3
sec rsa4096/C50738FFBA0FC25A
created: 2017-08-15 expires: 2018-12-31 usage: C
trust: ultimate validity: ultimate
ssb rsa4096/83F37AC3EB3EEE94
created: 2017-08-15 expires: 2018-12-31 usage: S
ssb rsa4096/C20F64EA1C4D2C94
created: 2017-08-15 expires: 2018-12-31 usage: E
ssb* rsa4096/C66FE2FCF049C26F
created: 2017-08-15 expires: 2018-12-31 usage: A
[ultimate] (1). Homer Simpson (Programmer) <h.simpson@domain.com>
gpg> save
Check if it worked
ubuntu@ubuntu:~$ gpg2 --card-status
Reader ...........: Yubico Yubikey 4 OTP U2F CCID 00 00
Application ID ...: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Version ..........: 2.1
Manufacturer .....: Yubico
Serial number ....: XXXXXXXX
Name of cardholder: [not set]
Language prefs ...: [not set]
Sex ..............: unspecified
URL of public key : [not set]
Login data .......: [not set]
Signature PIN ....: not forced
Key attributes ...: rsa4096 rsa4096 rsa4096
Max. PIN lengths .: 127 127 127
PIN retry counter : 3 0 3
Signature counter : 0
Signature key ....: C24A B711 7CBB CFAE EB17 6D8A 83F3 7AC3 EB3E EE94
created ....: 2017-08-15 13:08:48
Encryption key....: 8F8D 47E8 85B8 0FF8 415B 2A72 C20F 64EA 1C4D 2C94
created ....: 2017-08-15 13:10:22
Authentication key: 9D40 60F1 097D 52ED 0802 350A C66F E2FC F049 C26F
created ....: 2017-08-15 13:13:55
General key info..: sub rsa4096/83F37AC3EB3EEE94 2017-08-15 Homer Simpson (Programmer) <h.simpson@domain.com>
sec rsa4096/C50738FFBA0FC25A created: 2017-08-15 expires: 2018-12-31
ssb> rsa4096/83F37AC3EB3EEE94 created: 2017-08-15 expires: 2018-12-31
card-no: 0006 05653926
ssb> rsa4096/C20F64EA1C4D2C94 created: 2017-08-15 expires: 2018-12-31
card-no: 0006 05653926
ssb> rsa4096/C66FE2FCF049C26F created: 2017-08-15 expires: 2018-12-31
card-no: 0006 05653926
Personalizing
If you like, you can give your Yubikey a finishing touch by setting your name, sex, language preferations ect. This is only cosmetic. The only thing of real importance is the 'URL of public key'. Right now this field will probably remain blank, but at some point in the future you might decide to upload your public GPG key to a keyserver like the this one: https://pgp.mit.edu/. After uploading, you can specify the link to your key in the field mentioned above. This allows you to run the 'fetch' command to obtain your public key from the server.
ubuntu@ubuntu:~$ gpg2 --card-edit
Reader ...........: Yubico Yubikey 4 OTP U2F CCID 00 00
Application ID ...: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Version ..........: 2.1
Manufacturer .....: Yubico
Serial number ....: XXXXXXXX
Name of cardholder: [not set]
Language prefs ...: [not set]
Sex ..............: unspecified
URL of public key : [not set]
Login data .......: [not set]
Signature PIN ....: not forced
Key attributes ...: rsa4096 rsa4096 rsa4096
Max. PIN lengths .: 127 127 127
PIN retry counter : 3 0 3
Signature counter : 0
Signature key ....: C24A B711 7CBB CFAE EB17 6D8A 83F3 7AC3 EB3E EE94
created ....: 2017-08-15 13:08:48
Encryption key....: 8F8D 47E8 85B8 0FF8 415B 2A72 C20F 64EA 1C4D 2C94
created ....: 2017-08-15 13:10:22
Authentication key: 9D40 60F1 097D 52ED 0802 350A C66F E2FC F049 C26F
created ....: 2017-08-15 13:13:55
General key info..: sub rsa4096/83F37AC3EB3EEE94 2017-08-15 Homer Simpson (Programmer) <h.simpson@domain.com>
sec rsa4096/C50738FFBA0FC25A created: 2017-08-15 expires: 2018-12-31
ssb> rsa4096/83F37AC3EB3EEE94 created: 2017-08-15 expires: 2018-12-31
card-no: 0006 05653926
ssb> rsa4096/C20F64EA1C4D2C94 created: 2017-08-15 expires: 2018-12-31
card-no: 0006 05653926
ssb> rsa4096/C66FE2FCF049C26F created: 2017-08-15 expires: 2018-12-31
card-no: 0006 05653926
gpg/card> admin
Admin commands are allowed
gpg/card> name
Cardholder's surname: Simpson
Cardholder's given name: Homer
To see a list of available commands, run
gpg/card> help
The end?
You can power off the live-system if:
- You copied
masterkey.txt,subkeys.txtandrevocation-cert.txtalong with a file containing the passphrases and Yubikey PINs to one (or many) offline backup devices. - You copied
gpg-publickey.txtandssh-publickey.txtto your normal computer or cloud. - You successfully moved the keys to the Yubikey
Of course, this is not the end. Your next steps should involve uploading your gpg-public-key to a keyserver and completing the personalization of your Yubikey. After that, you can start the process of importing your public-key on all your computers such that you can actually start using the Yubikey for doing stuff.
One small remark here if you want to add your Yubikey to Ggp4Win: Because of a slight hiccup, you need to run
gpg2 --card-edit
fetch
and then
gpg2 --card-status
again.
Only now gpg will realize that there is actually a smartcard around with your key on it.
Touch functionality
To prevent malware from logging your PIN and then abusing your Yubikey while it is still plugged in, the Yubikey 4 has a new touch functionality. If this is enabled, cryptographic tasks will only be executed after you entered the corretc PIN and touched the golden icon on the device. Instructions on how to turn this feature on can be found here. I strongly recommend activating this.

Congratulations @the-tech-guy! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPCongratulations @the-tech-guy! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPCongratulations @the-tech-guy!
Your post was mentioned in the hit parade in the following category: